by Megan Daudelin
May 18, 2016
The Verizon Data Breach Investigation Report (DBIR), first published in 2008, is an annual publication that analyzes information security incidents from public and private organizations, with a focus on data breaches. Data breaches continue to have a major financial impact on organizations, as well as an impact on their reputations. Tenable Network Security offers dashboards and Assurance Report Cards (ARCs) that organizations can use to check themselves against the common threats described in the Verizon DBIR. As in previous years, the 2016 DBIR notes that a vast majority of all attacks fall into a few basic patterns. Throughout this and past years’ reports, suggestions are given for monitoring the network for each of these patterns. Based on the best practices described in the DBIR, the Web Application Vulnerabilities dashboard can assist an organization in monitoring web application to vulnerabilities and potential exploitation vectors.
The Verizon DBIR recommends prioritizing the remediation of web application vulnerabilities due to the increased exposure to the internet. The risk associated with a single web application vulnerability may vary based on the location of the system within the network. The exploitation of web application vulnerabilities has increased since 2015, highlighting the need for organizations to prioritize the remediation of related vulnerabilities. By exploiting web application vulnerabilities, attackers can gain a foothold on the network and continue to spread their attack from within. Some of the common methods used to compromise vulnerable web applications are SQL Injection (SQLi) and Cross-Site Scripting (XSS).
The interconnectedness of web applications complicates vulnerability remediation and patch management efforts. Based on the best practices described in the DBIR, the Web Application Vulnerabilities dashboard helps security teams identify and understand vulnerabilities related to web servers and applications in their environment. The dashboard uses guidance from the Open Web Application Security Project (OWASP) and Common Weakness Enumeration (CWE) to provide clarity and categorize concerns. SQLi and XSS attacks are commonly used to compromise systems, but additional concerns include broken authentication and session management issues, weak SSL/TLS implementations, and click-jacking attacks. This dashboard provides analysts with a concise view of web server and application vulnerabilities and events.
The components in this dashboard leverage data gathered by active vulnerability scanning with Nessus and passive vulnerability detection with Nesuss Network Monitor (NNM). Collecting vulnerability data actively and passively gives analysts unique insight into the web applications in their environment. Additionally, Log Correlation Engine (LCE) is used to normalize log data and correlate events, enabling the detection of intrusion and virus activity. In-depth vulnerability visibility within an organization allows security teams to proactively respond to threats, mitigate vulnerabilities, and take preventative measures before any serious damage occurs.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends.
The dashboard requirements are:
- Tenable.sc 5.3.1
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Tenable's Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. The Nessus Network Monitor (NNM) performs deep packet inspection to enable discovery and assessment of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, cloud applications, and critical infrastructure. The Log Correlation Engine (LCE) performs deep log analysis and correlation to continuously discover and track systems, applications, cloud infrastructure, trust relationships, and vulnerabilities. By integrating with Nessus, NNM, and LCE, Tenable.sc CV’s continuous network monitoring is able to detect events and vulnerabilities across the enterprise.
The following components are included in this dashboard:
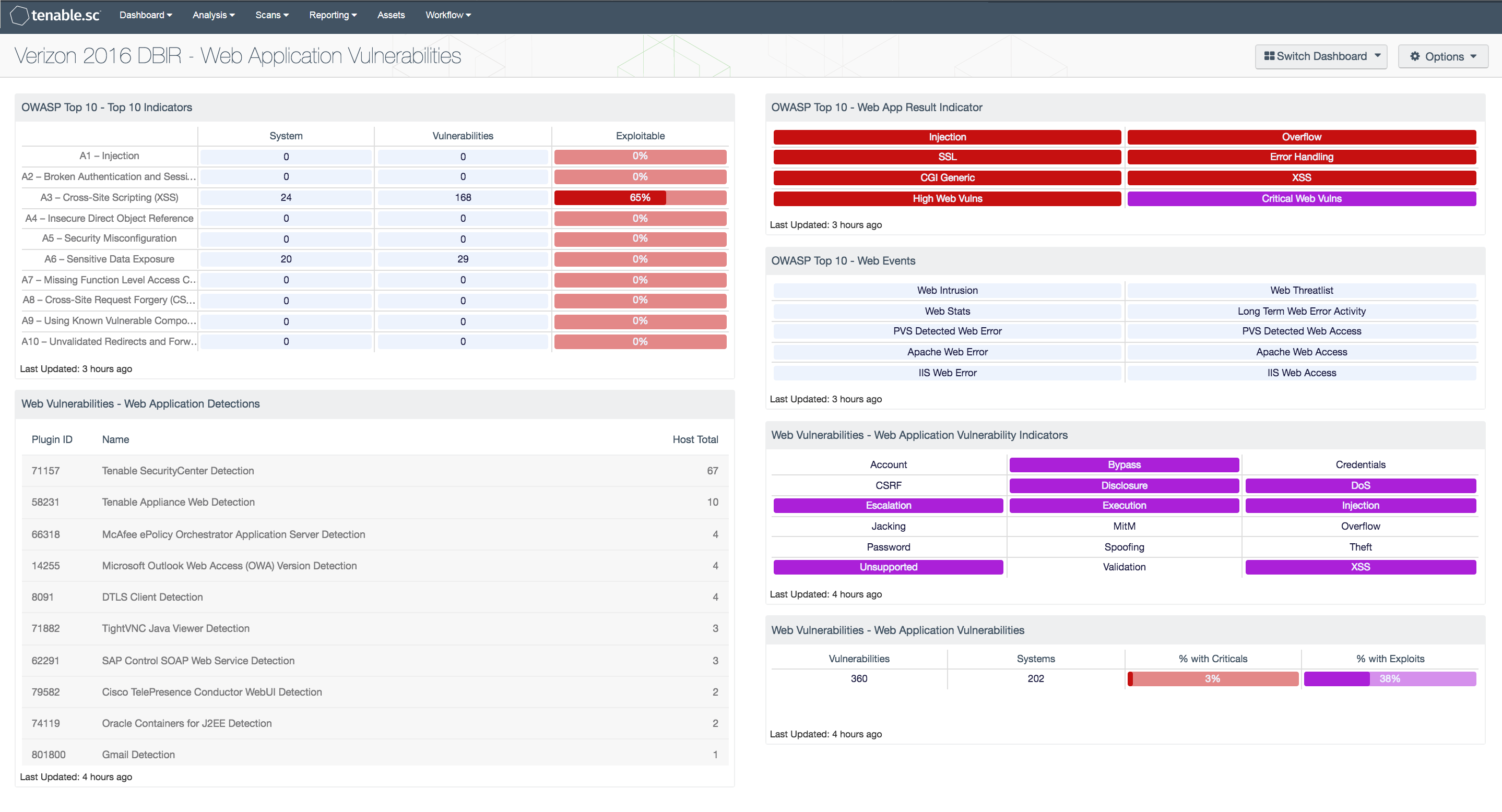
- OWASP Top 10 – Top 10 Indicators: This component collects the vulnerabilities from the CGI Abuses, CGI Abuses : XSS, and Web Servers plugin families for both active and passive vulnerabilities. The CGI Abuses family Checks for web-based CGI programs with publicly documented vulnerabilities. These checks include SQL injection, Local File Inclusion (LFI), Remote File Inclusion (RFI), Directory Traversal, and more. For web-based CGI programs with publicly documented cross-site scripting (XSS) vulnerabilities, the CGI Abuses : XSS plugin family is used. For web server vulnerabilities, the Web Server plugin family can detect vulnerabilities in web servers such as Apache HTTP Server, IBM Lotus Domino, Microsoft IIS, and many more. The matrix is comprised of three columns, with the first displaying a count of affected hosts, followed by the number of vulnerabilities. The vulnerability count includes low, medium, high and critical severities. The third column provides an analysis of known exploitable vulnerabilities.
- Web Vulnerabilities – Web Application Detections: This table displays web application detections on the network. These detections are from the active and passive CGI, Internet Services, and Cloud Services plugin families. A count of hosts is given for each detection; the list is ordered so that the detection with the greatest number of hosts is at the top. An analyst can use this table to determine if any unauthorized web applications are in use on the network.
- OWASP Top 10 – Web App Result Indicator: This component provides a summary of the common web application security flaws recommended for tracking in PCI DSS v3 Section 6.5.
- OWASP Top 10 – Web Events: This component provides indicators for logs collected by LCE that reflect potential vulnerabilities to web applications. The indicators focus on the intrusion, threatlist, stats, web-access, and web-error event types. The indicators for threatlist and intrusion turn red when a match is found. The red indicator means immediate attention is required to determine if a system has been compromised. The other indicators will turn yellow when a match is found; these indicators suggest a warning, and should be reviewed to determine the severity.
- Web Vulnerabilities – Web Application Vulnerability Indicators: This matrix displays key words that are present in the web application vulnerabilities detected on the network. These vulnerabilities are from the active and passive CGI, Internet Services, and Cloud Services plugin families and include all severity levels except Informational. The key words cover the major web threats, such as password and account weaknesses, information disclosure, improper input validation, injection attacks, cross-site scripting (XSS), and more. A purple indicator means that one or more vulnerabilities contain the keyword; clicking on the indicator will bring up details on the vulnerabilities.