by Cody Dumont
June 20, 2016
One of the biggest challenges that organizations face today regarding data leakage are employees that deliberately or unknowingly leak confidential information. Although some data loss occurs from external breaches, the majority of data leakage stems from employees engaging in behaviors that place the organization at risk. The ISO/IEC27000 Data Leakage Monitoring dashboard can assist organizations in identifying potential data leakage, which can aid in reducing risk, protect customer privacy, and keep confidential data secure.
The ISO/IEC 27002:2013 framework is a global security standard that provides best practice solutions in support of the controls found in Annex A of ISO/IEC 27001:2013. The framework establishes guidelines and general principles for initiating, implementing, maintaining, and improving Information Security Management Systems (ISMS). Each security controls and objectives provided within the standard can be tailored to specific business and regulatory objectives, and assist with maintaining overall compliance. This dashboard focuses on the ISO/IEC 27002 14.1 control, which can help to strengthen security controls by monitoring multiple network endpoints for data leakage activity.
Many organizations are not aware of the amount of data that is being transferred in and out of a network on a daily basis. Collaboration tools, instant messaging, cloud services, and peer-to-peer applications are frequently used within organizations to enhance productivity and performance. However, many applications are often left unmonitored and can introduce serious risks. Some organizations will deploy monitoring and Data Loss Prevention (DLP) solutions to protect confidential data, however this may not cover all of the potential endpoints where data loss may occur on a network. Implementing proper security controls at every endpoint, and educating employees on policies and procedures can help to protect confidential data.
The components within this dashboard will monitor data leakage activity from multiple network endpoints and highlight areas of interests for security teams and analysts. Cloud and peer-to-peer (P2P) events will help to identify employee activity and behavior that could be damaging to an organization. The Nessus Network Monitor (NNM) can analyze and detect data traversing the network such as credit card numbers, Social Security numbers, and other sensitive information. Organizations using DLP solutions can forward logs to the Log Correlation Engine (LCE), which can provide targeted information for security teams. Keywords that detect potential data leakage activity are identified through Nessus scans. Security teams will find the information on this dashboard highly valuable, as this will help to identify potential areas of interest that are reporting potential leakage.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform. Tenable’s Log Correlation Engine (LCE) performs automatic discovery of users, infrastructure, and vulnerabilities across more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. NNM provides deep packet inspection to continuously discover and track users, applications, cloud infrastructure, trust relationships, and vulnerabilities. Tenable.sc CV is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Using Tenable.sc CV, the organization will obtain the most comprehensive and integrated view of its network devices and sources of potential data leakage.
Components
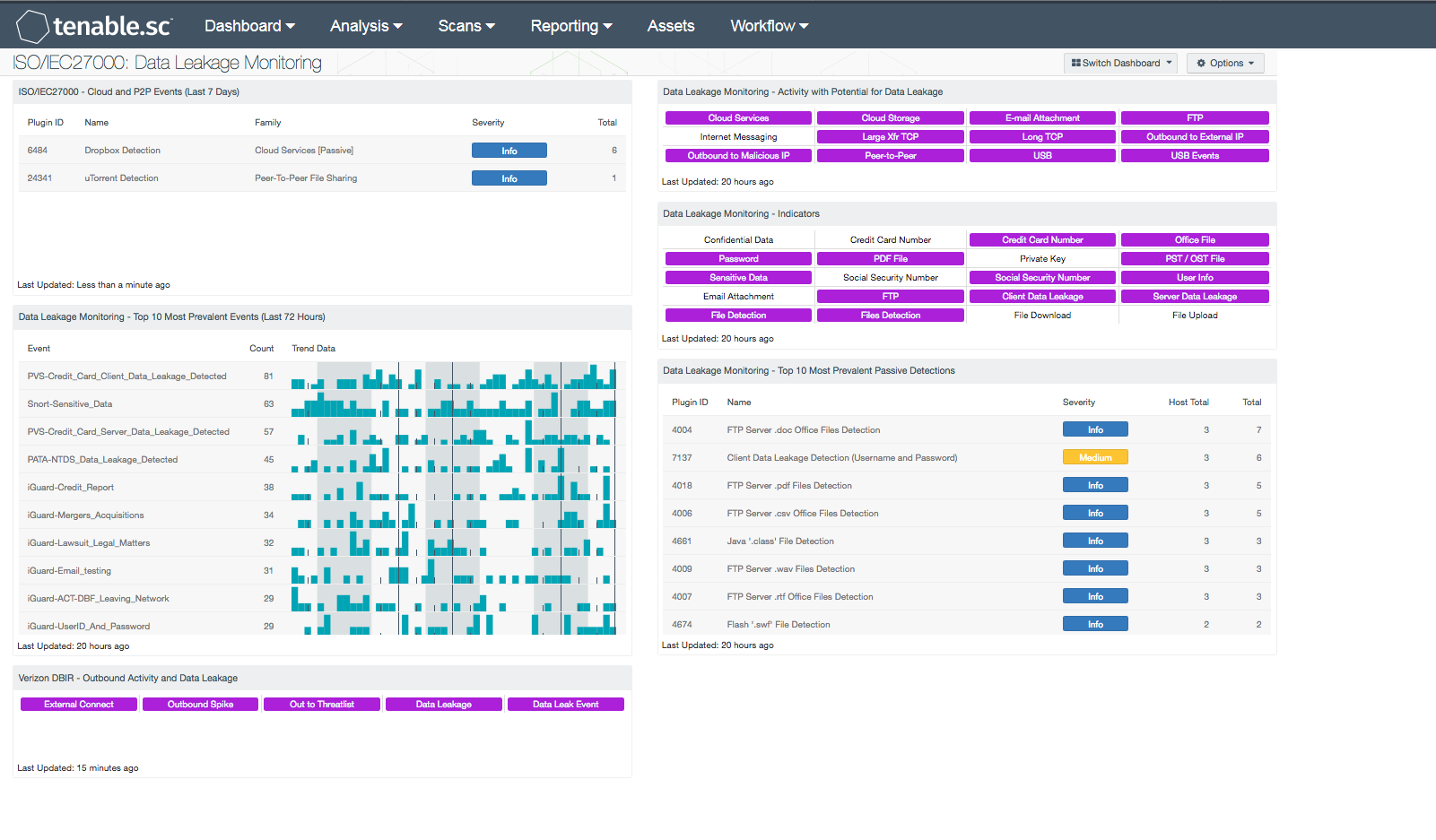
ISO/IEC27000 - Cloud and P2P Events (Last 7 Days): This component presents Cloud and Peer-to-Peer (P2P) activity on a network over the last 7 days. Both the “Cloud Services” and “Peer-To-Peer File Sharing” NNM plugin families are utilized in this component. The table is sorted by the highest number of vulnerabilities at the top of the list. This component will provide insight into users engaging in unauthorized activity that could leak to data leakage and/or malware infection. Analysts can use the data provided in this component to modify or block specific cloud or P2P services.
Data Leakage Monitoring - Top 10 Most Prevalent Events (Last 72 Hours): This table presents the most prevalent logged data leakage events in the last 72 hours. The logged events are reported by LCE under the 'data-leak' event type, and include events forwarded via syslog from NNM. A count of occurrences is given for each logged event; the list is ordered so that the event that occurred most often is at the top. A trend graph is also given for each event.
Data Leakage Monitoring - Activity with Potential for Data Leakage: This component presents indicators for activity detected on the network that has the potential for data leakage. The indicators are based on events logged in the last 72 hours and on actively and passively detected vulnerabilities. Indicators are included for such things as cloud interaction, outbound traffic to external IP addresses, peer-to-peer file sharing vulnerabilities, and USB usage. A purple indicator highlights a vulnerability/event detection. Clicking on a highlighted indicator will bring up the analysis screen to display details on the vulnerabilities/events. In the analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities/events are present. This component can be used to investigate the potential for data leakage.
Data Leakage Monitoring - Indicators: This component presents warning indicators to draw attention to types of data that may have been leaked and methods whereby data may be leaking. These indicators make use of both passive detections and events logged within the last 72 hours. A purple indicator highlights a vulnerability/event detection. In two cases (Credit Card Number and Social Security Number), there are two indicators: one to highlight data leakage detected passively and one to highlight data leakage detected through logged events. Clicking on a highlighted indicator will bring up the analysis screen to display details on the vulnerabilities/events. In the analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities/events are present. This component can be used to further investigate any data leakage.
Data Leakage Monitoring - Top 10 Most Prevalent Passive Detections: This table presents the top 10 most prevalent passive detections of data leakage. These passive detections are vulnerabilities reported by NNM in the 'Data Leakage' plugin family. A count of detections is given for each vulnerability; the list is ordered so that the vulnerability with the greatest number of detections is at the top. The severity of the vulnerability and a count of hosts on which the vulnerability was observed are also given for each vulnerability.
Verizon DBIR - Outbound Activity and Data Leakage: The Verizon DBIR advocates monitoring outbound connections to prevent data exfiltration. This matrix assists the organization in monitoring its outbound activity. The External Connect indicator is highlighted purple if outbound connections are passively detected from a system inside the network (as defined by the 'Monitored Network IP Addresses and Ranges' NNM configuration parameter) to a system outside the network. The Outbound Spike indicator is highlighted purple if a large spike in outbound connections was detected in the last 72 hours. The Out to Threatlist indicator is highlighted purple if traffic outbound to a known bad IP address was detected in the last 72 hours. The Data Leakage and Data Leak Event indicators are highlighted purple if data leakage was detected passively or via events, respectively. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation.