by Cody Dumont
January 12, 2016
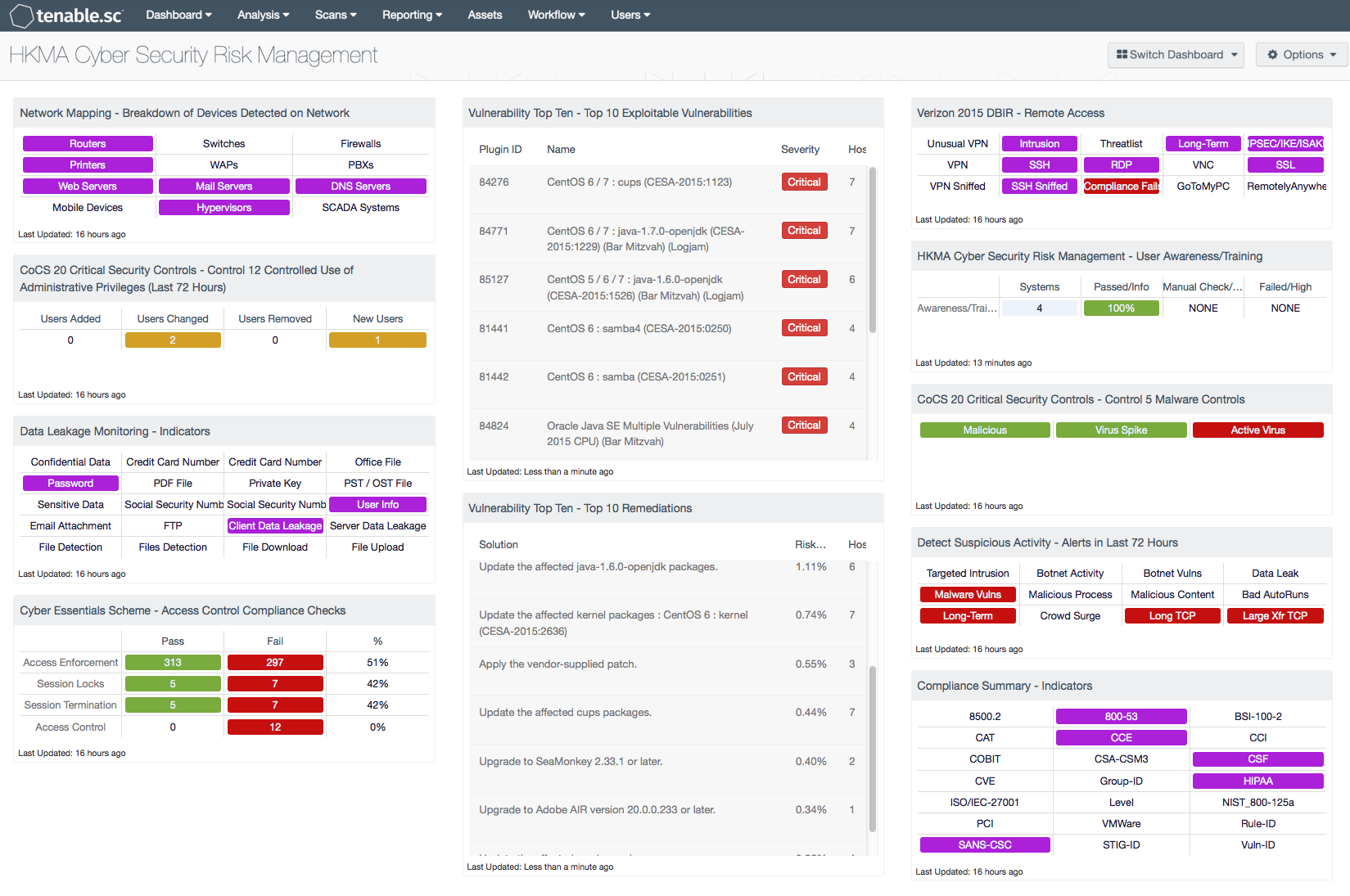
Cyber Security Risk Management is crucial for any financial institution to protect their critical assets, including the sensitive information of their customers from potential cyber attacks. As the frequency, stealth, and sophistication of cyber attacks continue to rise globally, the Hong Kong Monetary Authority (HKMA) published a circular in September 2015 highlighting the growing importance of Cyber Security Risk Management. This dashboard assists customers in gauging their adherence to controls described in the circular.
The Cyber Security Risk Management circular highlights the importance of adopting a benchmark of cyber security controls for Authorised Institutions (AIs). The benchmark includes industry standard processes and services to further protect the financial systems of Hong Kong. The circular includes 11 cyber security controls, which are preventive or detective in nature. Additionally, the circular makes references to several internationally accepted standards such as Center for Internet Security (CIS) Critical Security Controls, Control Objectives for Information and Related Technology (COBIT), and ISO 27000.
The HKMA Cyber Security Risk Management dashboard maps to the cyber security controls prescribed by HKMA. The dashboard provides organisations with an overall view of their security posture and helps to identify significant risks. The components map to the different controls in the circular and can assist analysts to ensure effective cyber security risk management.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive. The dashboard requirements are:
- Tenable.sc 5.1.0
- Nessus 8.5.1
- LCE 6.0.0
- Compliance Data
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. Tenable.sc Continuous View (CV) measures compliance but collecting vulnerability data from network analysis, active scanning, and log collection and correlation. Collection data from these locations allows the organisation to identify gaps and lapses detected and the prioritized remediation efforts. With more supported technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure, Tenable.sc CV provides the best solution for managing compliance with regulations. Tenable provides peace of mind to customers, because Tenable.sc CV detects security and compliance issues before our competitors.
This dashboard contains the following components:
- Network Mapping - Breakdown of Devices Detected on Network: By helping organisations to maintain an accurate inventory and detecting any unauthorized systems, this component maps to the HKMA control “(a) Registration of authorized and restriction on unauthorized devices, software and networks”.
- Compliance Summary - Indicators: This component helps analysts monitor which compliance standards are being checked during configuration audits, thus mapping to the HKMA control "(b) Secure configuration and access controls of devices, software and networks”.
- Vulnerability Top Ten - Top 10 Exploitable Vulnerabilities: This component provides the list of the top 10 exploitable vulnerabilities sorted by severity, and maps to the HKMA control "(c) Identification and remediation of vulnerabilities of devices, software and networks”.
- Vulnerability Top Ten - Top 10 Remediations: This component helps an organisation to prioritize the vulnerability remediation tasks and reduce the overall risk, and maps to the HKMA control "(c) Identification and remediation of vulnerabilities of devices, software and networks”.
- CoCS 20 Critical Security Controls – Control 12 Controlled Use of Administrative Privileges (Last 72 Hours): This component tracks the usage of administrative privileged user accounts used within the organisation, and maps to the HKMA control "(d) Controlled use of privileged user accounts of devices, software and networks”.
- CoCS 20 Critical Security Controls - Control 5 Malware Controls: This component provides the details of malicious processes and viruses found from vulnerability scans within the organisation, and maps to the HKMA control "(e) Defenses against malwares and Advanced Persistent Threats (APTs)”.
- Cyber Essentials Scheme - Access Control Compliance Checks: This component provides the number of compliant and non-compliant settings that matches with the access control compliance checks, and maps to the HKMA control "(f) Security and access controls of application systems”.
- Data Leakage Monitoring - Indicators: This component presents warning indicators of sensitive data detected within the organisation, and maps to the HKMA control "(g) Protection of customer data and sensitive information stored in, or accessible by, different media, devices, software and networks”.
- Verizon 2015 DBIR - Remote Access: This component can assist an organisation in monitoring remote access from external devices to internal assets, and maps to the HKMA control "(h) Security related to IT systems and networks accessible by mobile devices or devices outside the AI’s physical security controls”.
- Detect Suspicious Activity - Alerts in Last 72 Hours: This component presents warning indicators for potentially suspicious network activity, and maps to the HKMA control "(i) Detection of unusual activities of, and potential intrusions into, IT systems and networks”.
- Cyber Security Risk Management - User Awareness/Training: This component helps analysts to measure IT awareness/training and effectiveness, and maps to the HKMA control "(k) User education and awareness".