by Stephanie Dunn
May 13, 2016
Internet-facing systems and devices can be exposed to a wide variety of threats and security risks. Monitoring the flow of network traffic in and out of the network can help to detect problems and reduce the chance of critical systems being affected. This dashboard will assist the analyst in detecting and monitoring systems reporting outbound network communications.
Most internet-facing devices provide the vital resources that organizations rely on to connect and conduct business operations. Every organization will have some type of internet-facing device placed within a perimeter network such as a mail server, company web server, or firewall device. Many of these devices by default face higher risks due to their placement within the network. Once deployed, some of these devices are often left unmonitored, misconfigured, or contain default or weak passwords. When combined, these risk factors can allow an attacker to easily penetrate any internet-facing device to obtain sensitive or confidential information.
This dashboard provides a comprehensive view of external network traffic activity on internet-facing systems. Several components will monitor port activity from NetFlow logs collected by the Tenable NetFlow Monitor (TFM) and Tenable Network Monitor (TNM) clients. The TNM is designed to monitor network traffic and send session information to the LCE server. The TFM client utilizes the NetFlow protocol to send network session statistics to remote collectors for processing and reporting. This information will allow analysts to monitor network traffic without having to install a sniffer on a hub or switched SPAN port. Systems accepting external connections may indicate malicious activity or unauthorized ports in use. Nessus has several built-in functions to perform compliance checks against internet-facing devices. This information will provide best practices for restricting network traffic; detecting suspicious packets, and hardening firewall solutions. Analysts can apply additional filters to monitor specific internet-facing assets or direction of network traffic. Using this dashboard, organizations will gain a better understanding of the behavior of network traffic, and can use the information provided to strengthen existing controls on internet-facing devices.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring. The dashboard requirements are:
- SecurityCenter 5.3.1
- Nessus 6.6.2
- PVS 5.0.0
- LCE 4.8.0
- Compliance Data
- Local Checks
- Tenable Network Monitor
- Tenable NetFlow Monitor
Tenable SecurityCenter ContinuousView (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. SecurityCenter CV is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. The Tenable Log Correlation Engine (LCE) correlates real-time events, such as port scanning, and then performs analysis to discover vulnerabilities and indicators of compromise (IOC). The Tenable Passive Vulnerability Scanner (PVS) is able to collect network metadata through passive monitoring, finding inappropriate activity, identifying assets and vulnerabilities from network traffic, and detecting hard to profile assets including Virtual, BYOD, and SCADA. SecurityCenter CV allows for the most comprehensive and integrated view of network health.
The following components are included in this dashboard:
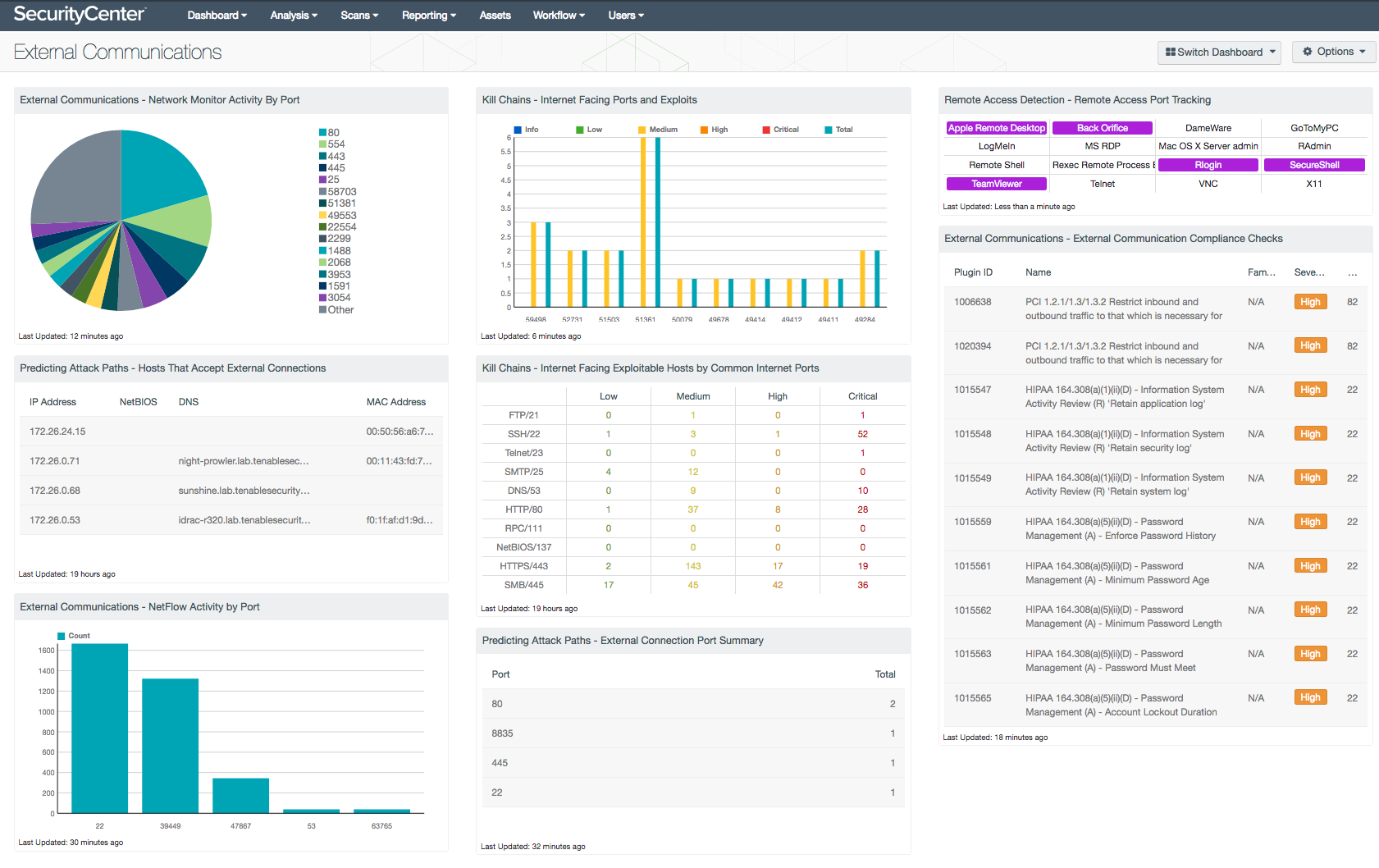
- External Communications - Network Monitor Activity By Port: The Network Monitor Activity By Port chart displays the top 15 ports with the highest session counts. This information presents a list of ports that have been analyzed by the Tenable Network Monitor (TNM) client. The TNM is a client used by the Log Correlation Engine (LCE) that monitors inbound and outbound sessions traffic from a main switch or router. The TNM can monitor and report on UDP, TCP, ICMP, and IGMP traffic. Analysts can use this information to quickly identify and close any unauthorized ports or services. Note that this component requires the Tenable TNM LCE client.
- Predicting Attack Paths - Hosts That Accept External Connections: When PVS is deployed in a manner to monitor external network traffic, PVS has the ability to readily identify any system and service that is in use. This component utilizes data from plugin ID 14, “Accepts external connections”. UDP and TCP services are both detected and the table presents data via the IP Summary tool with columns for the host IP address, NetBIOS, MAC address, and DNS Name.
- External Communications - NetFlow Activity by Port: The NetFlow Activity by Port chart displays the top 10 ports with the highest session counts reported by the Tenable NetFlow Monitor (TFM) LCE client. The TFM client takes advantage of the ability in most modern routers to use the NetFlow protocol to send network session statistics to remote collectors for processing and reporting. This enables monitoring of network traffic without having to install a sniffer on a hub or switched SPAN port. This information can assist in understanding and monitoring the dataflows and services active on the network. Note that this component requires the Tenable TFM LCE client.
- Kill Chains - Internet Facing Ports and Exploits: This chart presents a Port Summary of all known exploitable vulnerabilities, sorted by port, and not including any port 0 vulnerabilities, with the top 10 being shown. The results are presented via a bar chart, with data for each exploitable port, with the severity being displayed. SC CV is able to present the analyst with a table that displays the most potentially vulnerable hosts and displays individual at most risk. The table displays most at risk assets, filtering on severity, and if known exploits are available in a bar format displaying severity as well as total exploits for that port. When used in conjunction with the Internet Facing Hosts Asset List, provided in the SecurityCenter Feed, or other custom combination asset created by the analyst, the component reports only vulnerabilities found/detected within the assigned asset list.To gain the full use of this component, see the how to guide on Breaking Kill Chains. A detailed description of how to use this collection can be found in the how-to guide on Breaking Kill Chains.
- Kill Chains - Internet Facing Exploitable Hosts by Common Internet Ports: his component contains four columns that enumerate the number of hosts with vulnerabilities on a specific port. The columns provide a count of vulnerable hosts based on specific ports and severity level. The colors used in this matrix have a transparent background and change the color based on the severity level. The color green represents low severities, yellow is for medium severity, high severity vulnerabilities are orange, and critical severities are red. When used in conjunction with the Internet Facing Hosts Asset List, provided in the SecurityCenter Feed, or other custom combination asset created by the analyst, the component reports only vulnerabilities found/detected within the assigned asset list.
- Predicting Attack Paths - External Connection Port Summary: This component uses information from plugin ID 14, “Accepts external connections”, and the Port Summary tool to present a table that is sorted by the most commonly observed active ports. The port column displays the TCP port, and the count column presents the number of systems detected. This allows the analyst to determine which ports are open externally.
- Remote Access Detection - Remote Access Port Tracking: This component uses NetFlow and Network Monitor analysis to identify systems with traffic that may be related to a specific protocol. LCE also provides the ability to monitor NetFlow information by either collecting NetFlow or by using the Network Monitor Agent. The Network Monitor Agent works similar to a NetFlow collector, but stores the records in a LCE-friendly method. The NetFlow and Network Monitor can detect traffic patterns and which can then be identified as interesting traffic. The filters use the “Destination Port” filter as the ports are on well-known sources, and tracking based on “Destination Port” will result in less false positives. When a pattern is discovered the indicator will turn purple.
- External Communications - External Communication Compliance Checks: The External Communication Compliance Checks component provides a summary of network traffic and boundary device audit checks. Nessus uses a variety of audit files to check firewall and perimeter device configurations. High severity denotes checks that have failed to meet the compliance threshold. Medium severity shows checks that need to be manually reviewed to assess their compliance state. Organizations should review current security policies and compliance requirements that are relevant to the organization. Each compliance check includes detailed information on the respective vulnerability that the analyst can immediately drill down into. Information presented within this component is useful in configuring perimeter devices to monitor and restrict unauthorized or malicious network traffic.