by Michael Willison
June 27, 2014
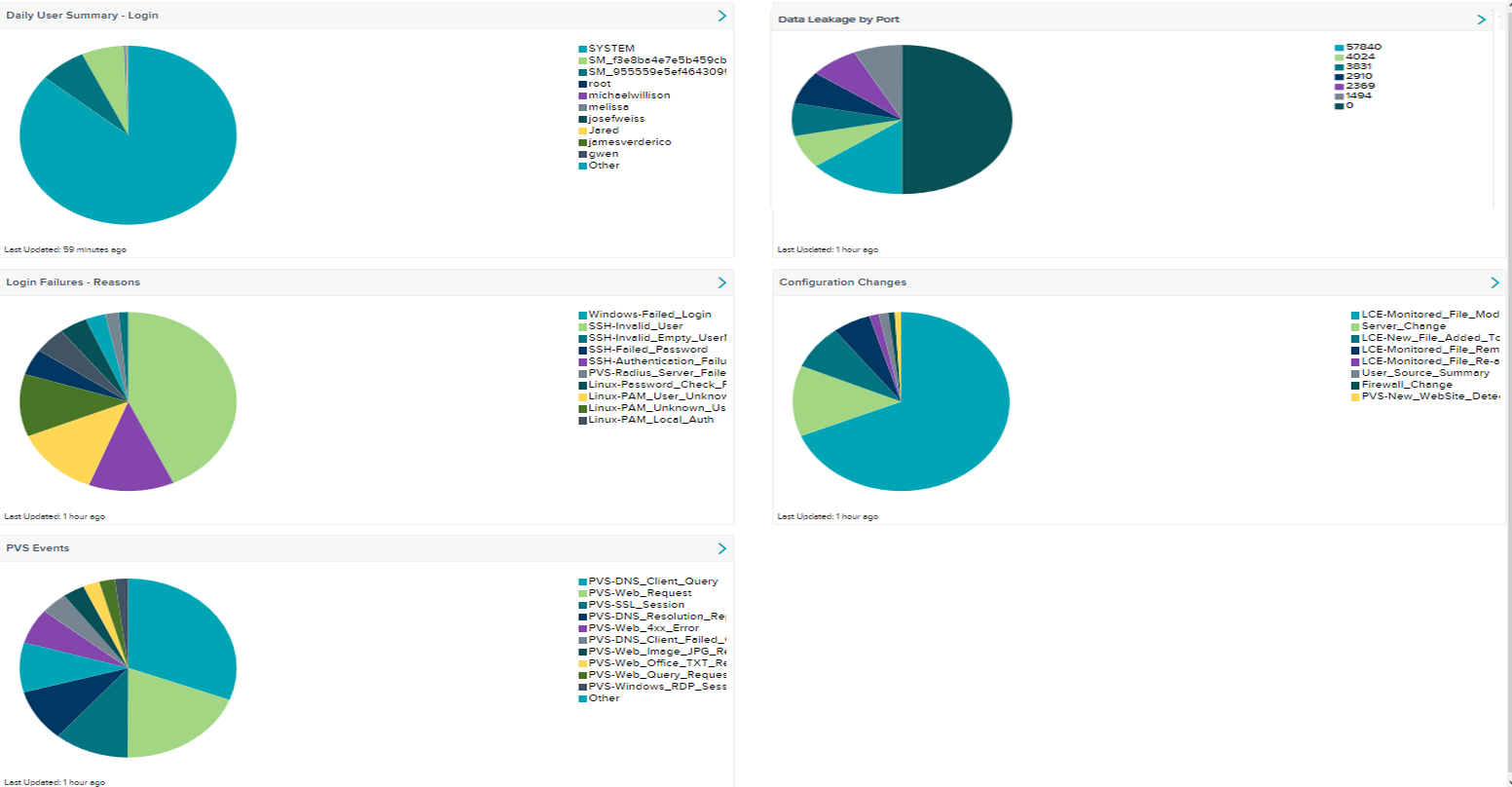
The Daily Usage Summary dashboard collects and displays daily information that the IT Security team should review frequently during the workday. These components are helpful in monitoring activity within the corporate network. For daily review, the operation center may need to monitor user logins, both successful and unsuccessful, and monitor for configuration changes. This dashboard provides several components that track data loss prevention (DLP) events, Tenable Passive Vulnerability Scanner (PVS) events, user activity, and configuration changes. This dashboard refreshes hourly and should be monitored throughout the workday.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Discovery & Detection.
The dashboard requirements are:
- SC 4.8.1
- LCE 4.2.2
- PVS 4.0.2
Listed below are the included components:
- Daily User Summary – Logins - This component collects the top 10 cumulative user logins over the past 24 hours. The data provided in the chart assists in understanding which accounts have logged in and out within the past 24 hours. Additionally, the chart provides a count of the login occurrences. For example, the service_admin account could be used as a service account and may log into multiple systems. However, the Joe_Smith account, a standard user account, may only login a few times during the course of a normal day. The result is that service accounts are more likely to exist in the pie chart, but standard users are not. This component refreshes hourly and should be monitored throughout the workday.
- Data Leakage by Port - The Data Leakage by Port component collects the top 10 ports that have been flagged for possible data leakage. Data leakage events are triggered when the presence of sensitive data such as a credit cards or social security numbers are discovered in the PVS or logged events. PVS analyzes data in motion and identifies sensitive data, such as credit card information, as well as general types of documentation sharing. PVS identifies a wide variety of file sharing and data in motion activity, which can be used to highlight inbound and outbound communications. This component refreshes hourly and should be monitored throughout the workday.
- Login Failures – Reason - This component collects the top 10 failed logins. For example, these failed login attempts could be invalid SSH users or unknown users in Linux. Failed logins could also be caused by automatic service accounts that have expired passwords, thus causing an account to try and login every five minutes. These events can also be caused by a password guessing attack. Any large number of failed logins should be investigated immediately to determine a reason for these failures. This component refreshes hourly and should be monitored throughout the workday.
- Configuration Changes - This component collects the top 10 configuration changes. Adding a new user account into Windows, changing a firewall rule, or installing new software may generate these events. Networks are always evolving and constantly require changes. SecurityCenter Continuous View (CV) customers can detect these changes by monitoring LCE and syslog events. PVS can alert in real-time when new hosts are discovered. This component refreshes hourly and should be monitored throughout the workday.
- PVS Events -The PVS Events component collects the top 10 PVS events by hour. Passive vulnerability scanning is the process of monitoring network traffic at the packet layer to determine topology, clients, applications, and related security issues. Tenable has expanded the functionality of PVS to include traffic profiling and system compromise detections.PVS detects vulnerabilities on the network by passively analyzing communication streams, and has the ability to identify interactive and encrypted network sessions. PVS can detect when new hosts are added to a network, track trusted sessions with other systems, and monitor port usage. PVS can also detect the number of hops each system is from the PVS sensor. This component refreshes hourly and should be monitored throughout the workday.