by Sharon Everson
February 26, 2016
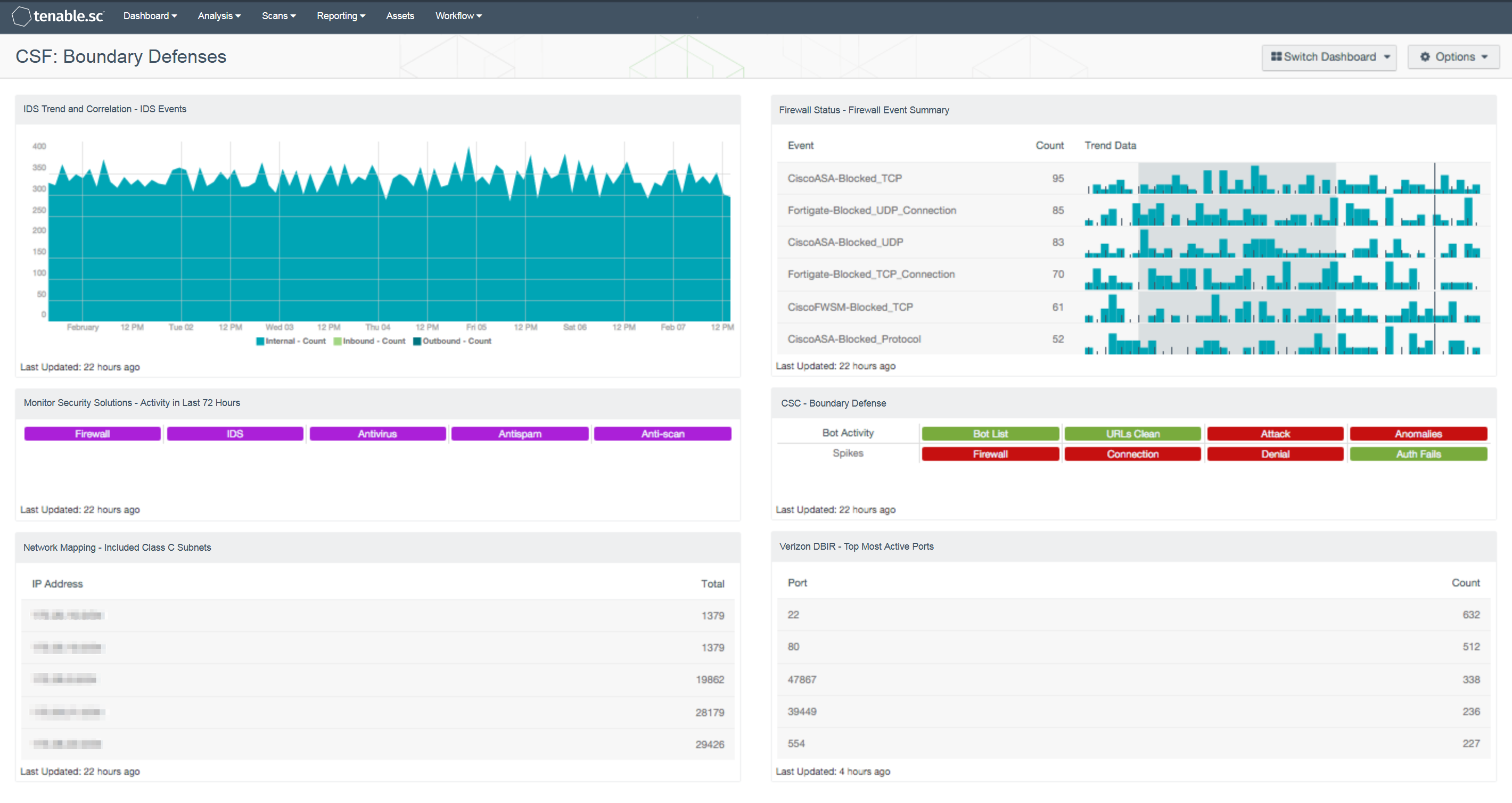
Organizations today can no longer afford to rely on conventional network defense devices to monitor and protect a network, both internally and externally. The lack of a multi-layered security strategy across each network segment will lead to increased intrusions and persistent threats. This dashboard aligns with the NIST Cybersecurity Framework (CSF) PR.AC-5 subcategory that displays information from network security devices and services, which will assist in improving network performance and security.
The CSF provides guidance based on existing standards, guidelines, and practices, which can be tailored to specific organizational needs. One of the five categories within the CSF is Protect. This category is divided into multiple subcategories that address specific security requirements with Access Control, Awareness, Data Security, Policies and Procedures, Maintenance, and Technology Protection. The first category within Protect function is Access Control (PR.AC), which provides guidance on access to assets for authorized users and devices. The PR.AC-5 subcategory is the primary focus of this dashboard, which will assist the analyst in monitoring network subnets, security devices, ports, firewall, and IDS events.
A critical aspect of protecting any network is protecting the network perimeter from outside sources. In order to accomplish this task, the organization should implement boundary protection devices and services such as anti-virus, firewalls, routers, and Intrusion Detection Systems (IDS) within each network boundary. Within this dashboard, the analyst will be able to detect firewall events, boundary defense status, port usage, and monitor security solution activity. Along with IDS inbound activity, both internal and outbound events are also presented, allowing the analyst to detect the presence of intruders, and other malicious activity.
Applying a multi-layered defense strategy will allow for multiple devices and services to protect the network in case one layer is breached. Proper network segmentation is crucial in the protection of network resources. Any network breach or disruption of network services can interfere with and compromise user productivity, business operations, and network integrity. Internal networks are just as critical, and need to be monitored frequently for insider threats, malicious activity, and attacks. Other types of networks such as wireless, extranet, and DMZs are often interconnected, allowing for attackers to gain access by pivoting to internal resources. Port activity and usage is a critical aspect that an organization should monitor regularly. The analyst can use the data provided within this dashboard to detect unauthorized ports and services. By integrating a multi-layered network security strategy, organizations will be able to effectively defend against attacks, protect network assets, and achieve a comprehensive defense-in-depth strategy.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Tenable.sc Continuous View (CV) provides continuous network event monitoring, risk reduction, and ensures compliance. Nessus is continuously updated with information about advanced persistent threats and zero-day vulnerabilities. NNM provides deep packet inspection to continuously discover events traveling the wire. LCE also has the capability to discover services, network devices, ports, and other critical infrastructure. Combined, Tenable.sc CV’s continuous network monitoring is able to detect systems, services, and security events across the enterprise.
The following components are included in this dashboard:
- IDS Trend and Correlation - IDS Events: This component displays a trend of inbound, outbound, and internal IDS events for the past seven days. This is useful to see if there have been any large spikes in attacks in any direction. Analysts can use this component to monitor for changes in traffic based on IDS events.
- Monitor Security Solutions - Activity in Last 72 Hours: This component assists in monitoring security solutions. The matrix presents activity indicators for various security solutions: Firewall, IDS, Antivirus, Antispam, and Anti-scanning. This component assumes that if log events were received in the last 72 hours from a particular technology, then that technology is active on the network, so the indicator is highlighted. Further investigation is warranted if a protection technology should be active, but no events are being received.
- Network Mapping - Included Class C Subnets: This table assists an organization in understanding the scope of its network by grouping all the IP addresses discovered actively by Nessus, passively by NNM, and from log events recorded by LCE into representative Class C subnets. This information can assist an organization in detecting any unauthorized subnets or rogue devices. Note that if the organization has a very large network, this component can be modified to present Class B subnets, if desired. The Total column displays the number of detections. This number of detections may be greater than the number of hosts in each subnet, as each host may have been detected multiple times.
- Firewall Status - Firewall Event Summary: This component displays the top 50 normalized firewall events by event count for firewalls from vendors such as Cisco, Juniper, Palo Alto, Fortinet, and many more. Each event will display the normalized event name, total event count, and trending data of this specific normalized event name. Using Tenable.sc CV for monitoring the different types of firewall events, a security analyst can determine if any malicious or suspicious firewall activity is occurring on the network.
- CSC - Boundary Defense: This component displays information on a series of plugins that detect bot activity or spikes in connection, authentication failures, and denials. Cells are green when there are no relevant detections and turn red when activity is detected. Analysts can use this component to quickly identify activity of potential concern related to boundary defenses.
- Verizon DBIR - Network TCP Port Usage: This table provides a list of the top 100 ports in use on the network. This table can be useful when monitoring network flows or establishing a baseline of traffic. Any new ports discovered should be investigated to determine their source and purpose. Any sudden change in count should be investigated as well. In the Verizon 2015 DBIR and the Mandiant M-Trends 2015 reports, common indicators of compromise were unauthorized FTP and other protocols. This component is included in dashboards related to the 2015 Verizon Data Breach Investigation Report (DBIR).