by Megan Daudelin
April 13, 2016
On April 12, 2016, Microsoft and the Samba Core Team disclosed details about the Badlock vulnerability. Badlock is a critical security bug affecting Windows and Samba, which exposes systems to man-in-the-middle and denial of service attacks. The release of details about the Badlock vulnerability was carefully coordinated to ensure that the patches to remediate the vulnerability were available as soon as the vulnerability was disclosed All Windows and Samba systems should be updated with the newly released patches and closely monitored for suspicious activity.
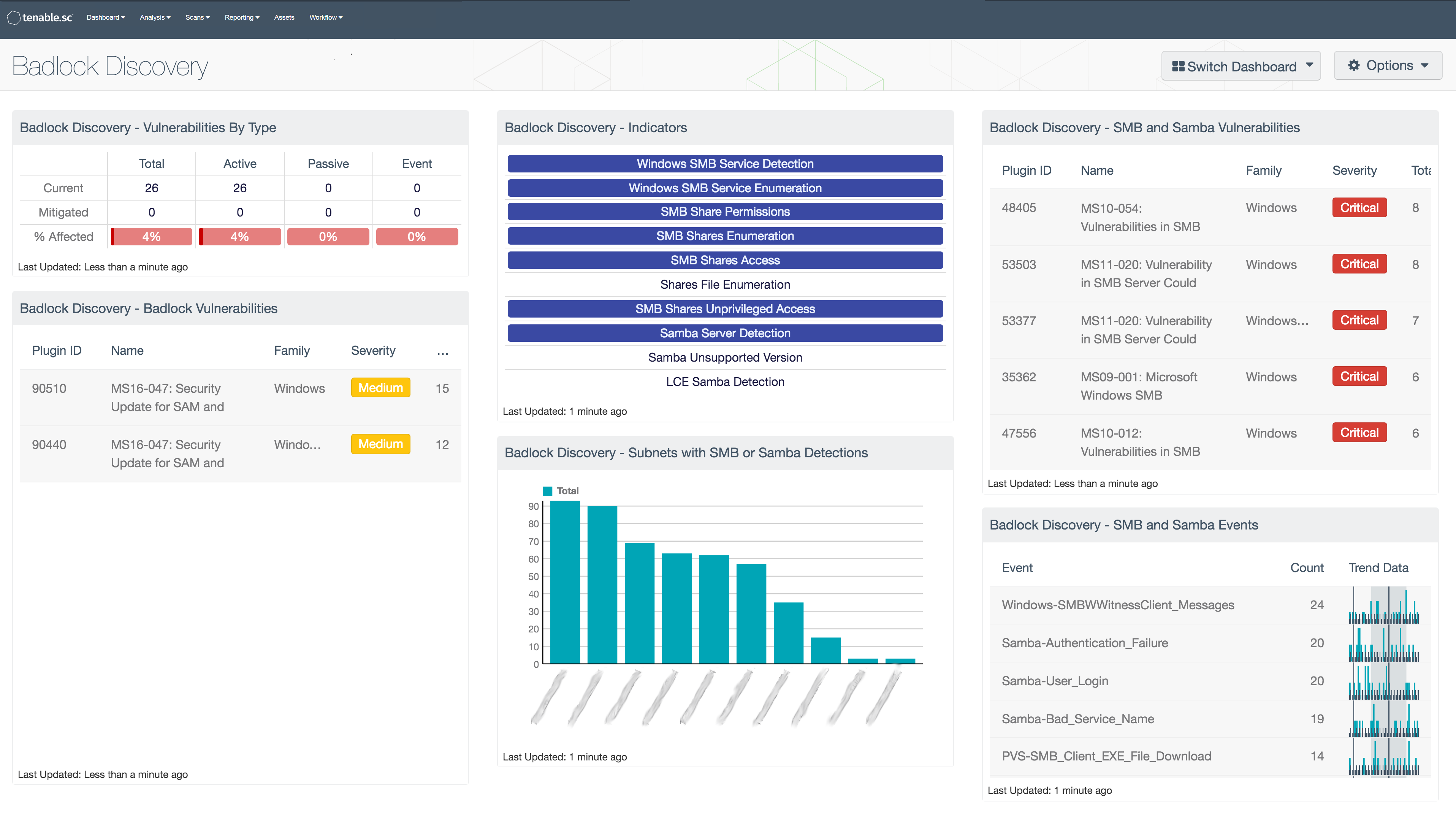
The Badlock Discovery dashboard can assist organizations with identifying hosts and vulnerabilities related to Microsoft Windows SMB and Samba. Outstanding vulnerabilities should be remediated to reduce the likelihood of compromise, and the new patches from Microsoft and Samba should be applied to all systems affected. Any outdated versions of SMB or Samba should be updated to ensure that security patches can be properly applied. Even after updating, events and vulnerabilities should be closely monitored to identify and respond to suspicious activity on systems using Samba or Microsoft Windows SMB.
The components in this dashboard provide insight into vulnerabilities, events, and detections related to Samba and Microsoft Windows SMB. A set of indicators displays alerts when SMB or Samba services are detected. Network subnets that have Samba or SMB detections are listed to help prioritize areas of the network for vulnerability remediation. Vulnerabilities specifically related to Badlock are identified by CVE. Samba and SMB vulnerabilities are listed by severity to focus remediation efforts. LCE events related to Samba and SMB activity are listed to detect changes or anomalies over time. Security teams can use this dashboard to focus their remediation efforts and identify potential activity related to the Badlock vulnerability.
This dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. This dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends. The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.2
- LCE 6.0.0
- NNM 5.9.0
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. The Nessus Network Monitor (NNM) performs deep packet inspection to enable discovery and assessment of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, cloud applications, and critical infrastructure. The Log Correlation Engine (LCE) performs deep log analysis and correlation to continuously discover and track systems, applications, cloud infrastructure, trust relationships, and vulnerabilities. By integrating with Nessus, NNM, and LCE, Tenable.sc CV’s continuous network monitoring is able to detect events and vulnerabilities across the enterprise.
The following components are included in this dashboard:
- Vulnerabilities by Type: The Vulnerabilities by Type matrix displays the counts of current and mitigated Badlock vulnerabilities detected by plugin type. Each column displays the count of vulnerabilities for a different plugin type. The first row filters for current vulnerabilities related to Badlock, and the second filters for mitigated vulnerabilities. The last row provides a ratio bar showing the percentage of Badlock vulnerabilities detected in the environment. Security teams can use this component to monitor the presence Badlock vulnerabilities in their environment.
- Badlock Vulnerabilities: The Badlock Vulnerabilities table presents a list of vulnerabilities related to Badlock. The table is filtered for several CVEs related to the Badlock vulnerability and is sorted by severity. Security teams can use this table to identify systems and vulnerabilities that may be vulnerable to Badlock exploitation.
- Indicators: The Indicators matrix contains cells that filter for specific Samba and SMB detections. Each cell filters for a specific plugin ID to identify particular detections or events. When the specified filter is triggered, the cell turns blue. Security teams can use this matrix to quickly understand the SMB and Samba detections occurring in their environment.
- Subnets with SMB or Samba Detections: The Subnets with SMB or Samba Detections bar chart shows which network subnets have the most detections related to SMB and Samba. The chart is filtered by the plugin IDs that detect SMB and Samba services. Security teams can use this chart to understand which subnets in their environment have been detected using SMB and Samba.
- SMB and Samba Vulnerabilities: The SMB and Samba Vulnerabilities table presents a list of vulnerabilities related to Microsoft Windows SMB and Samba. The table is filtered for the keywords “SMB” and “Samba” in the plugin name and sorted by severity. Security teams can use this table to identify systems using SMB and Samba and related vulnerabilities, which may make hosts more vulnerable to Badlock exploitation.
- SMB and Samba Events: The SMB and Samba Events table presents a list of normalized events related to SMB and Samba. The table is filtered for the keywords “SMB” and “Samba” in the normalized event name. Security teams can use this table to monitor event related to SMB and Samba, which may be related to Badlock exploitation.