by Cesar Navas
October 18, 2016
Perimeter devices provide the first line of defense in preventing attacks that occur on a daily basis against internal systems. Organizations typically focus much of their security efforts on perimeter devices, to prevent attackers from infiltrating the network. These devices can provide organizations with multiple layers of protection in case one layer is breached. However, a single misconfiguration within any one of these devices can leave multiple systems vulnerable to attack, increasing security risks. In addition, the network perimeter is becoming less and less clearly defined. Networks may contain hundreds of devices, servers, and web applications that have administrative interfaces accessible from the internet, and that are using default credentials that were never changed. Monitoring and securing the network perimeter and internal devices accessible from the internet is critical to maintaining overall security and reducing the chance of assets being compromised.
The French Network and Information Security Agency (Agence nationale de sécurité des systèmes d’information or ANSSI) developed the "40 Essential Measures for a Healthy Network" to assist organizations in safeguarding the security of information systems within a network. Following these measures, or rules, for a healthy network will provide basic protection for an organization's critical data. ANSSI states that the majority of IT attacks that have involved ANSSI stepping in could have been prevented had the IT measures set out in the guide been applied.
This dashboard aligns with Section VII of the ANSSI 40 Essential Measures for a Healthy Network: Protect the Internal Network from the Internet. This section contains two rules:
Rule 24 emphasizes the need to monitor and secure all perimeter devices and to compartmentalize network assets. This rule references the “Definition of a secure interconnection gateway architecture” (Définition d’une architecture de passerelle d’interconnexion sécurisée) document, which provides recommendations on how to correctly configure security devices and enable compartmentalization within the internal network. Securing the network perimeter will reduce the chance of an attacker gaining access to sensitive systems and data.
Rule 25 emphasizes the importance of removing administrative interfaces from internet-accessible systems. Attackers frequently exploit administrative interfaces on external-facing systems, particularly if the vendor-supplied default credentials are still in place. Ensuring that administrative interfaces are not accessible externally will help prevent attackers from gaining access to critical systems.
This dashboard can help analysts monitor perimeter security and perimeter devices on the network. Using this dashboard, an organization will better understand how the internal network can be accessed externally and what security concerns are present. This information will assist an organization in protecting critical systems and data in the internal network from potential attacks that might come from the internet.
Components on this dashboard will alert analysts to perimeter devices with vulnerabilities and compliance concerns, and to systems using default credentials. Analysts can easily detect systems with remote access activity, which can help to ensure that access is restricted and secured properly. Internal hosts participating in connections to systems outside of the internal network are identified. Indicators monitor perimeter devices in order to provide status and valuable information about any unauthorized activity or potential attacks in progress. Analysts using this dashboard will be able to effectively manage perimeter devices and limit external access to critical systems, which will help to improve the organization’s overall security posture.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.1
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization seeking to protect the internal network from the internet. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines perimeter devices and security solutions to determine vulnerabilities and compliance concerns. Passive listening collects data to continuously monitor traffic across the network perimeter, and those devices protecting the perimeter. Host data and data from other security devices is analyzed to monitor activity and identify malicious or anomalous behavior from users and devices. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure the perimeter and safeguard critical assets and information.
The dashboard contains the following components:
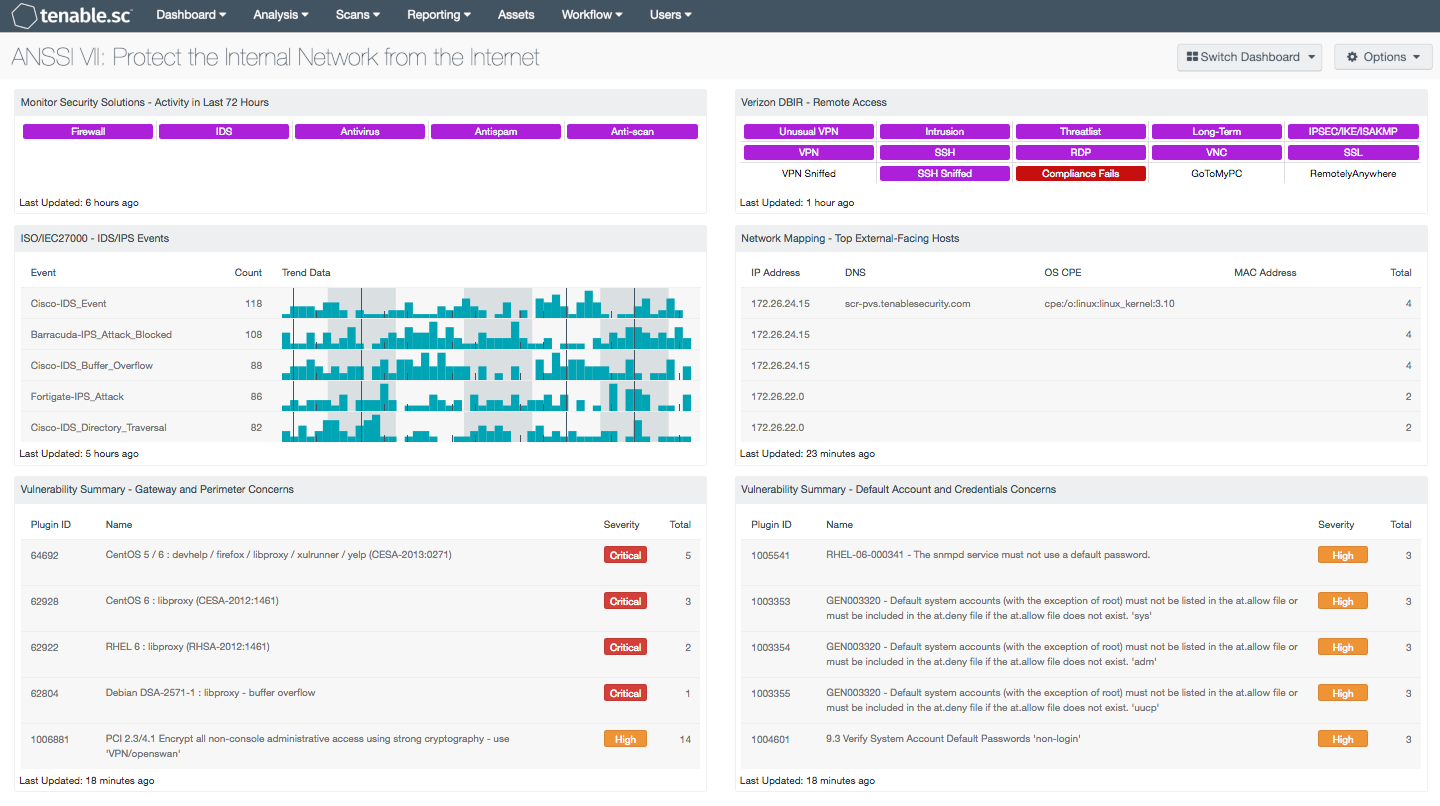
- Monitor Security Solutions - Activity in the Last 72 Hours: This component assists in monitoring security solutions. The matrix presents activity indicators for various security solutions
- ISO/IEC27000 - IDS/IPS Events: The IDS/IPS Events component presents normalized event information from IDS and IPS network devices
- Vulnerability Summary - Gateway and Perimeter Concerns: This component presents detected vulnerabilities and compliance concerns pertaining to the network perimeter
- Verizon DBIR - Remote Access: The Verizon DBIR notes that it is important to restrict remote access to systems. This matrix assists the organization in monitoring its remote access
- Network Mapping - Top External-Facing Hosts: This component uses both plugin ID 14 (Accepts external connections) and plugin ID 16 (Outbound external connections) to identify internal hosts participating in connections to systems outside of the internal network
- Vulnerability Summary - Default Account and Credentials Concerns: This component presents detected vulnerabilities and compliance concerns pertaining to default accounts and credentials