Tenable Nessus®
The Global Gold Standard in Vulnerability Assessment
Built for the Modern Attack Surface
Take advantage of the industry's most trusted vulnerability assessment solution to assess the modern attack surface. Extend beyond your traditional IT assets -- fortify your web applications, gain visibility into your internet-connected attack surface and secure your cloud infrastructure.
- Unlimited IT vulnerability assessments
- Configuration, compliance and security audits
- Use anywhere
- Configurable reports
- Community support
- Advanced support (available as an option)
- On-demand training (available as an option)
- Web application scans (5 FQDNs)
- Ability to add FQDNs
- External attack surface scans
- Ability to add domains
- Cloud infrastructure scans
- 500 prebuilt scanning policies
- Unlimited IT vulnerability assessments
- Configuration, compliance and security audits
- Use anywhere
- Configurable reports
- Community support
- Advanced support (available as an option)
- On-demand training (available as an option)
- Web application scans
- Ability to add FQDNs
- External attack surface scans
- Ability to add domains
- Cloud infrastructure scans
- 500 prebuilt scanning policies
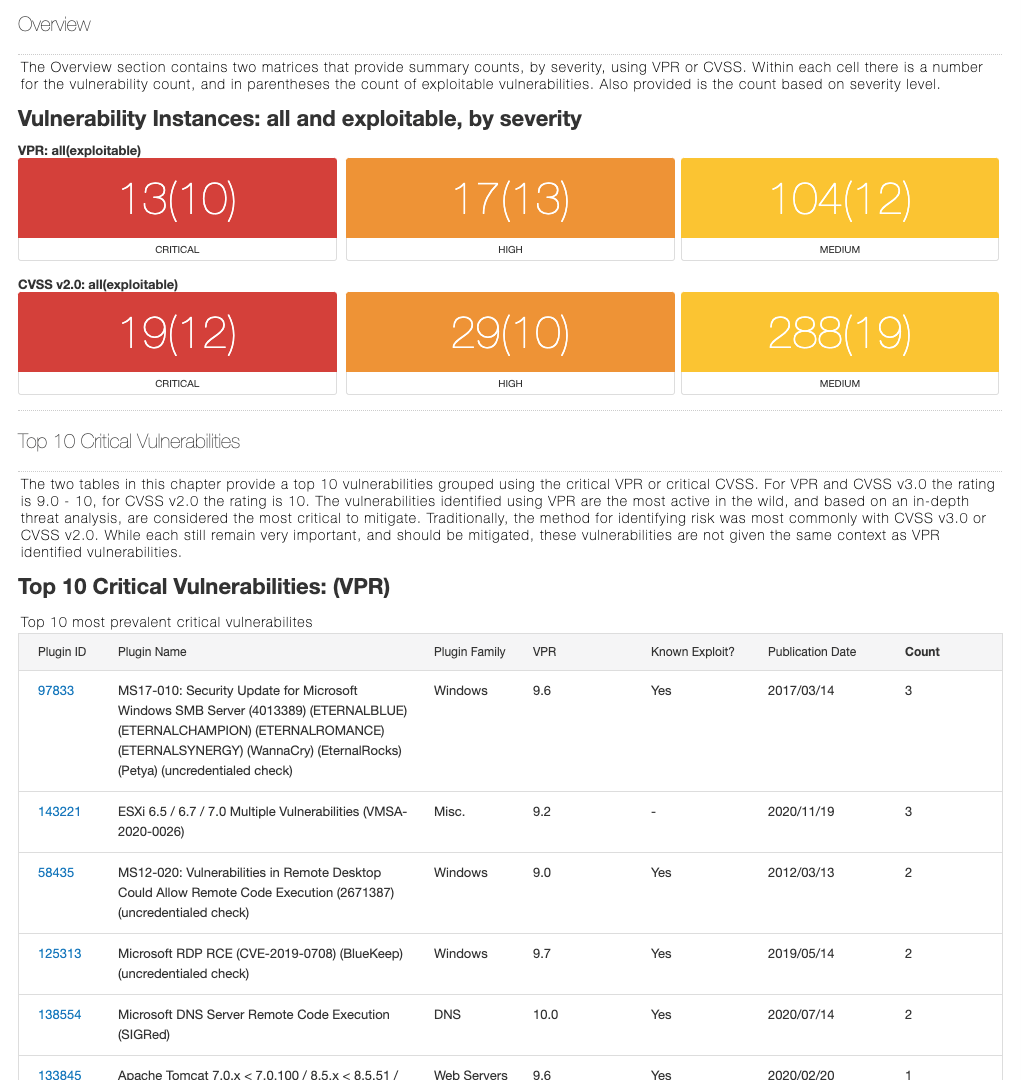
Nessus has the industry's lowest false positive rate with six-sigma accuracy.
Nessus has the deepest and broadest vulnerability coverage in the industry.
Nessus is trusted by tens of thousands of organizations, with 2 million downloads worldwide.
Don't just take our word for it. See for yourself why security practitioners around the world put their trust in Nessus.
Nessus is #1 For Vulnerability Assessment
From the beginning, we've worked hand-in-hand with the security community. We continuously optimize Nessus based on community feedback to make it the most accurate and comprehensive vulnerability assessment solution in the market. Twenty-five years later and we're still laser focused on community collaboration and product innovation to provide the most accurate and complete vulnerability data - so you don't miss critical issues which could put your organization at risk.
Today, Nessus is trusted by tens of thousands of organizations worldwide as one of the most widely deployed security technologies on the planet - and the gold standard for vulnerability assessment. See for yourself - explore the product here.
released weekly
Tenable’s Zero Day Research provides 24/7 updates into new and emergent vulnerabilities so you’ll always have full situational awareness.
KEY USE CASES FOR NESSUS
Nessus is the world’s No. 1 vulnerability scanning solution. Learn more about its power by exploring how Tenable customers put it to work in a variety of critical situations.
Pen Tester Cybersecurity Education Programs Faculty and Students Consultant SMB
Security Admin

Network penetration testers play a unique role in the IT security ecosystem.
Before executing full-fledged breach simulations that unveil how attackers can exploit specific weaknesses, pen testers often use Nessus first to identify exactly where those major vulnerabilities are hiding.
Read More
Students in cybersecurity education programs are invaluable to this highly specialized field.
Professors leading vulnerability assessment or vulnerability management courses use Nessus as a foundational tool. Its remarkable ease of use helps students quickly get acclimated to the essentials of uncovering vulnerabilities.
Read More
Cybersecurity consultants play pivotal roles in a constantly shifting threat and vulnerability landscape.
Cybersecurity consultants use Nessus to scour clients’ networks for vulnerabilities and create comprehensive reports that summarize security posture and contain key suggestions for remediation.
Read More
In years past, small and medium-sized businesses might have considered themselves effectively immune to cyberattacks.
Even the smallest companies that lack full-time cybersecurity staff can stay on top of vulnerabilities with Nessus, customizing comprehensive scans to meet unique business needs.
Read MoreTo learn more about Nessus features and functionality, visit our Nessus documentation page. To learn more about purchasing options, please contact your preferred reseller or visit our online store.
Tens of thousands of Customers worldwide rely on Nessus to keep their business safe and operational.
Get Started with Nessus Expert
Get the world’s most widely deployed vulnerability assessment solution.
With Advanced Support for Nessus Pro, your teams will have access to phone, Community, and chat support 24 hours a day, 365 days a year. This advanced level of technical support helps to ensure faster response times and resolution to your questions and issues.
Advanced Support Plan Features
Phone Support
Phone support 24 hours a day, 365 days a year, available for up to ten (10) named support contacts.
Chat Support
Chat support available to named support contacts, accessible via the Tenable Community is available 24 hours a day, 365 days a year.
Tenable Community Support Portal
All named support contacts can open support cases within the Tenable Community. Users can also access the Knowledge Base, documentation, license information, technical support numbers, etc.; utilize live chat, ask questions to the Community, and learn about tips and tricks from other Community members.
Initial Response Time
P1-Critical: < 2 hr
P2-High: < 4 hr
P3-Medium: < 12 hr
P4-Informational:
< 24 hr
Support Contacts
Support contacts must be reasonably proficient in the use of information technology, the software they have purchased from Tenable, and familiar with the customer resources that are monitored by means of the software. Support contacts must speak English and conduct support requests in English. Support contacts must provide information reasonably requested by Tenable for the purpose of reproducing any Error or otherwise resolving a support request.
Learn More About Nessus
Related Products
With Advanced Support for Nessus Pro, your teams will have access to phone, Community, and chat support 24 hours a day, 365 days a year. This advanced level of technical support helps to ensure faster response times and resolution to your questions and issues.
Advanced Support Plan Features
Phone Support
Phone support 24 hours a day, 365 days a year, available for up to ten (10) named support contacts.
Chat Support
Chat support available to named support contacts, accessible via the Tenable Community is available 24 hours a day, 365 days a year.
Tenable Community Support Portal
All named support contacts can open support cases within the Tenable Community. Users can also access the Knowledge Base, documentation, license information, technical support numbers, etc.; utilize live chat, ask questions to the Community, and learn about tips and tricks from other Community members.
Initial Response Time
P1-Critical: < 2 hr
P2-High: < 4 hr
P3-Medium: < 12 hr
P4-Informational: < 24 hr
Support Contacts
Support contacts must be reasonably proficient in the use of information technology, the software they have purchased from Tenable, and familiar with the customer resources that are monitored by means of the software. Support contacts must speak English and conduct support requests in English. Support contacts must provide information reasonably requested by Tenable for the purpose of reproducing any Error or otherwise resolving a support request.