Solutions for Security Frameworks
Take control. Propel improvement. Secure the business.
Network security is a key challenge for organizations of all sizes. Increasingly, IT teams are using security frameworks to guide their efforts to protect their critical systems and data.
Watch the Video
A variety of security frameworks are available to help users meet due care standards, continuously identify security gaps, comply with multiple compliance requirements and communicate business risk to executives.
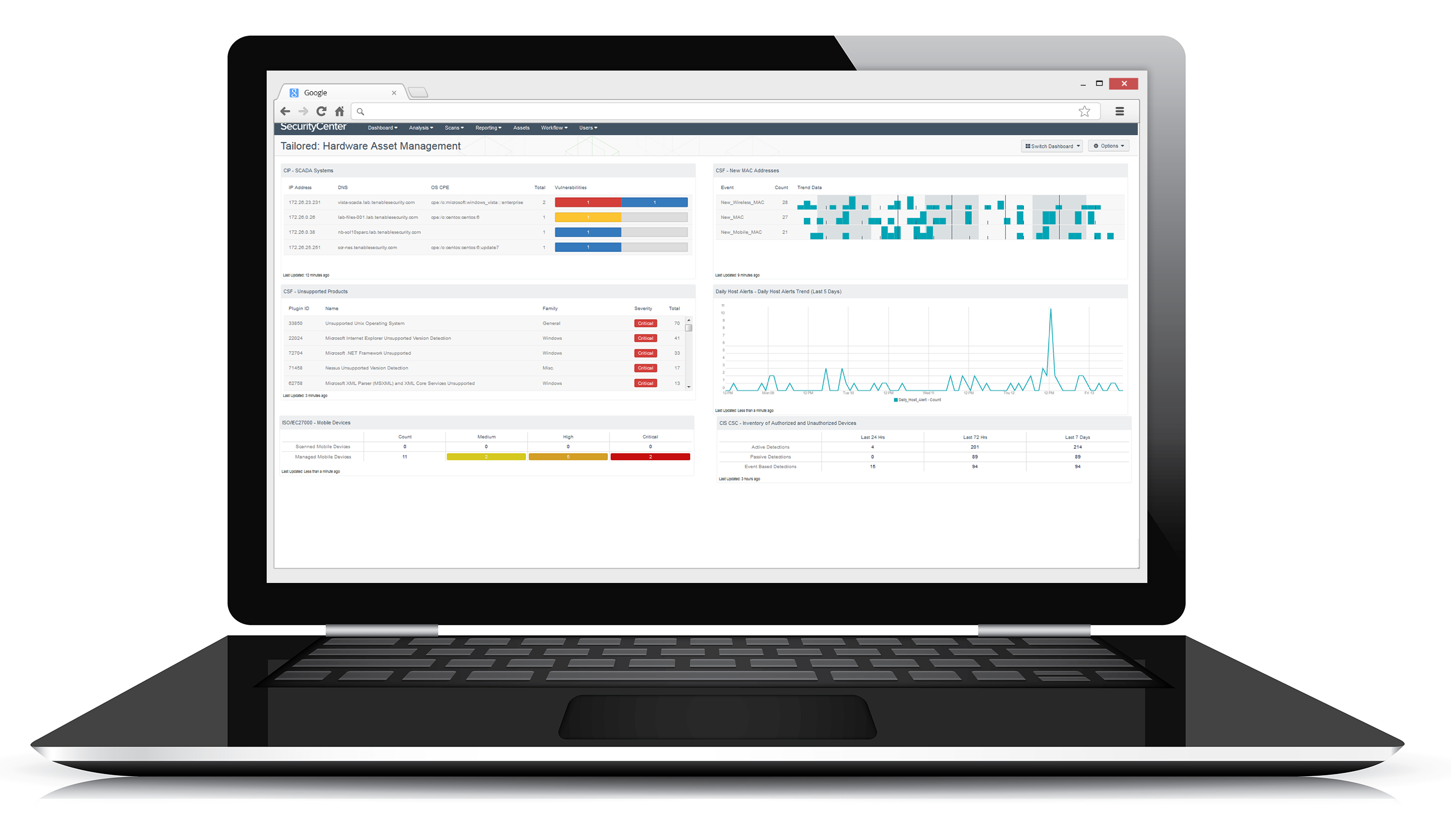
To create a tailored solution, many organizations are selecting controls from different frameworks to suit their specific risk profile, requirements and resources. For example, they may use the NIST Cybersecurity Framework or ISO/IEC 27001/2 for administrative controls and the CIS Critical Security Controls for technical controls.
Get the Solution Story
Learn how Tenable Security Center automates and continuously monitors technical controls.
Read NowExplore Security Frameworks
A Next-Generation Approach to Security
Tenable Security Center supports the flexibility of frameworks, with report, dashboard and Assurance Report Card® (ARC) templates that can easily be tailored to meet business needs.
Tenable Security Center collects data from multiple sensors to provide advanced analysis of vulnerability, threat, network traffic and event information and delivers a continuous view of IT security across your environment.
Broadest Coverage
Supports most technical controls prescribed in the NIST CSF, ISO/IEC 27002 and CIS CSC frameworks, and builds them into an automated control foundation for managing risk and securing the business.
Continuous Visibility
Use active scanning combined with continuous listening to obtain a complete view of control conformance across your environment.
Analyze Third-Party Security Products
Audit configurations of many third-party products and analyze events generated by them to identify control weaknesses.
Dynamic Asset Grouping
Focus dashboards to display a complete security and compliance view for services in your industrial control system and IT networks, including physical and virtual infrastructure, cloud and mobile environments.
Measure, Visualize and Communicate Adherence to Controls
Easily measure, visualize and understand your technical control conformance status by using dashboard templates, and identify gaps between where you are and where you want to be.
Map Technical Control Status to Business Objectives
Use Tenable Security Center Assurance Report Cards® to compare your current security status to the desired status and help you build a roadmap for demonstrating a defensible security program.
Survey Report
Cybersecurity Frameworks and Foundational Security Controls – a Survey of IT Professionals
"Today’s security teams are looking for all the help they can get to do an increasingly difficult job. Frameworks have become a common place to look for guidance, with most companies, 80%, saying they use a cybersecurity framework."Dimensional Research, November 2016