Are you sure you don’t have a control system on your network?
This blog entry describes many of the recent advances Tenable has made with active and passive detection of supervisory control and data acquisition (SCADA) and industrial control system (ICS) devices on networks.
There has been a dramatic increase in devices and applications that control power, industrial processes, and even our homes. With almost 600 public SCADA vulnerabilities, 214 of them disclosed in 2012, Tenable has kept pace with these advances by developing new forms of detection for Nessus and the Passive Vulnerability Scanner.
A Short Review of Active and Passive ICS Discovery
Nessus finds SCADA and ICS devices through network scanning. It can discover basic services associated with control systems, such as ICCP or Modbus, and can also identify many different types of control systems such as WellinTech KingView or Ecava IntegraXor software. Nessus also finds vulnerabilities in these systems and can highlight exploitable control system devices.
Nessus can also be used to audit the configuration of Unix or Windows systems running common control system software. Digital Bond’s Bandolier project currently offers more than 35 different audit files for major control system vendors.
Tenable’s Passive Vulnerability Scanner (PVS) can identify ICS, SCADA, and control system software through continuous network traffic monitoring. Many types of control system solutions leverage broadcast protocols, proprietary services, or have readily detected banners. As control systems are managed over the network, PVS tracks these devices, ports, and applications. When I hear from customers that they’ve discovered unknown control system devices on their network, it's usually with PVS.
Since PVS is 100% passive, there is no chance of having a SYN packet or a UDP packet taking down a control system. More importantly, PVS sees everything, including communications that happen infrequently. This allows greater discovery and analysis of your ICS network with no impact to production.
Nessus currently has 132 plugins in its SCADA family, and PVS supports 139 plugins. Although there is some commonality, these plugins don’t overlap much. Some ICS devices are readily discoverable with a scan, while others can only be identified with credentialed Windows or Unix local checks. Some devices have broadcasted protocols that are ideal for PVS to discover. For 100% coverage of a network, Tenable recommends a combined active and passive approach.
RuggedOS Telnet Backdoor
A recent SCADA vulnerability that was widely publicized was the announcement of CVE-2012-1803. This vulnerability was a backdoor account placed in RuggedCOM operating systems. Nessus implemented a check for this (plugin ID #58991), and an example output is shown below:
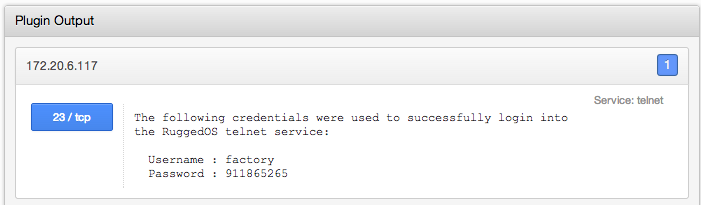
This vulnerability is very critical and easy to exploit.
RuggedOS has had its share of security issues on different protocols. As of now, the following active Nessus checks are available from Tenable for this device:
Johnson Control Scan Example
I’ve been lucky enough to get invited to a wide variety of “SCADA Labs,” “Control Systems Test Rigs,” or here in Washington, DC, “Cyber Critical Infrastructure Test Ranges,” to determine what Nessus is capable of detecting in these environments. These visits are very useful to Tenable because most control system vendors have unique and different types of protocols, operating systems, and user interfaces.
If you start scanning control systems devices, you may be very surprised what you find. I visited a lab recently and found a device that scanned like Windows:
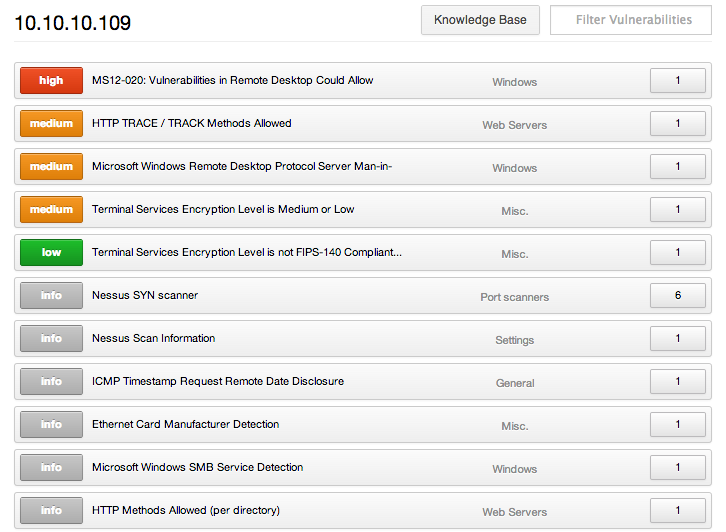
However, this device didn't look anything at all like a laptop, a Dell rack, or anything that resembled a computer. It had embedded Windows in it and lots of Coax cables and serial ports.
Bandolier Configuration Audit of Telvent OASyS
As previously mentioned, Digital Bond has authored and tested a wide variety of Nessus audit policies for leading control system applications. These applications run on Windows or Unix systems. In some cases, Digital Bond has worked with the vendors of these systems to help write Nessus audits in much the same spirit as the Center for Internet Security does to establish best practices.
Below is a screen shot of a partial configuration audit of Telvent OASyS control system application that runs on Windows:
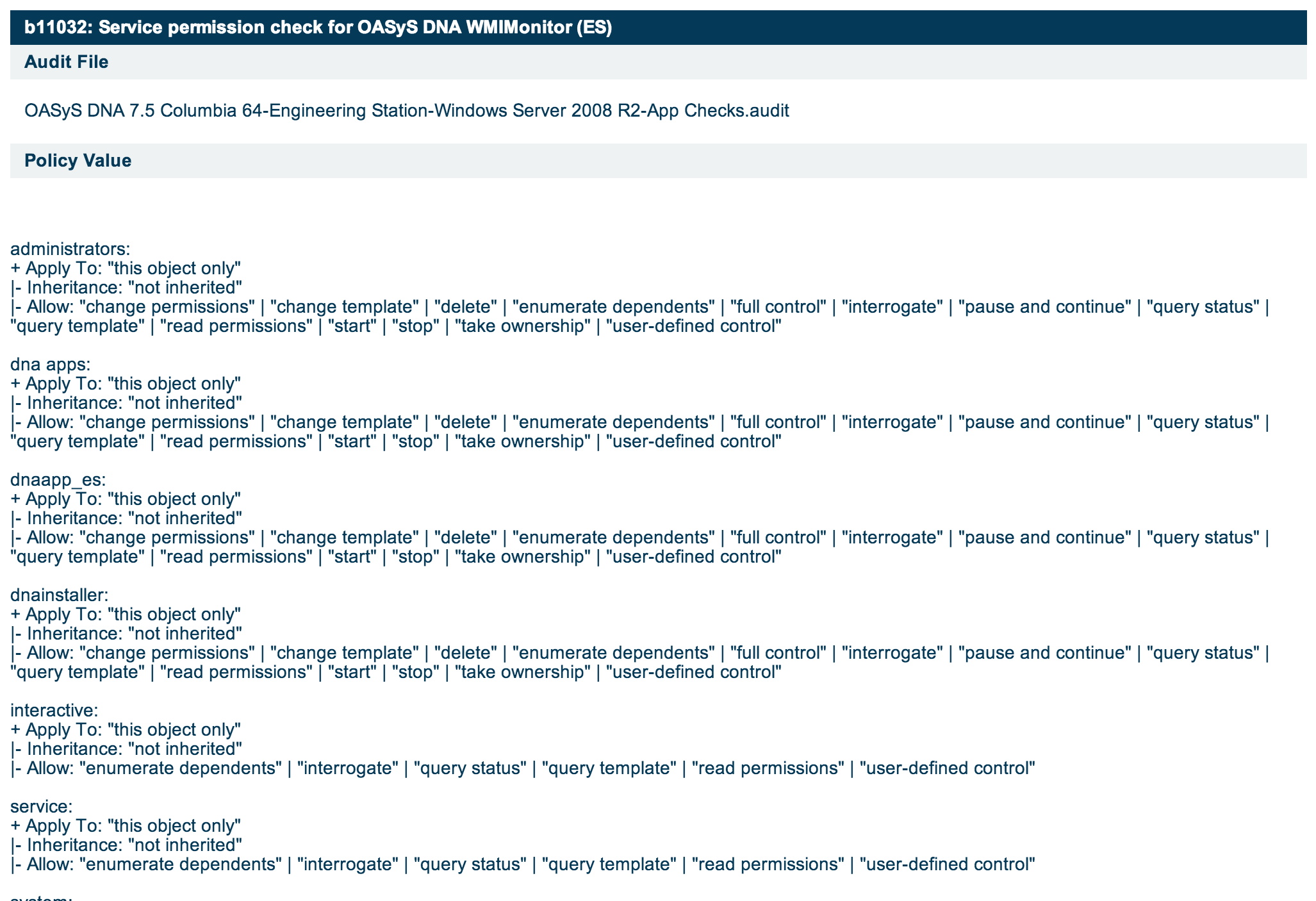
In this case, the audit is testing specific Windows security policy settings that are relevant to the secure operation of the application. Not all control system applications are deployed insecurely, but Digital Bond has encountered many applications that were deployed “out of the box” and not had basic or advanced security hardening.
Hardening control system applications by tightening their security controls offers defense in depth, which makes them resistant to compromise and exploitation. These audits are often accompanied by traditional hardening of Windows and Unix systems through the use of other audit standards such as CIS and the US government’s SCAP content.
Niagara Tridium Detection on an Enterprise Network
Nessus will collect as much information about a scanned IP as possible. As Tenable’s Research team adds support for direct detection of various SCADA devices, detecting control system devices with Nessus becomes easier.
For example, in this screen shot below, Nessus has found a web server running on port 3011 with a web banner of a Niagara Tridium device.
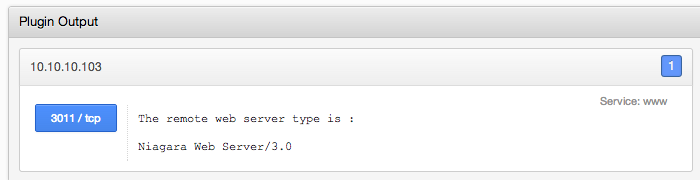
This sort of information can be consumed by Nessus to specifically identify these devices. (Note: When I gathered the data and screen shots for this blog entry in 2012, plugins 67142, 67143, and 67144 to detect Niagara web servers didn’t exist yet.)
At a different site, monitored by Nessus, PVS, and Tenable’s SecurityCenter, a search for any vulnerability text containing the word “Niagara” showed a variety of results:
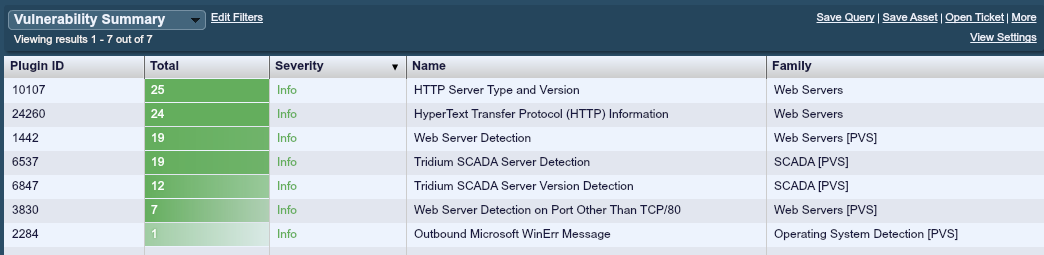
The first two are Nessus plugins (10107 and 24260) that found Niagara web servers running on ports 80 and 3011. The remaining plugins are from the Passive Vulnerability Scanner. PVS includes a variety of checks specifically for Tridium (Niagara) devices.
It also inadvertently caught a Windows Error message from a system running the niagarad.exe software.
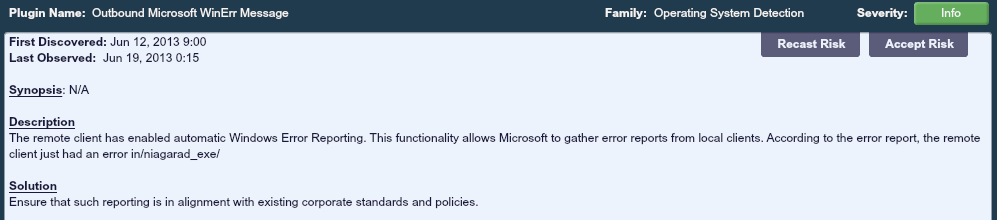
I find this error worth investigating because it indicates a crash in a Windows system that is running Niagara control software. Since this network is also covered by Tenable’s Log Correlation Engine, I ran a query for all events occurring during the past 15 days for the IP address in question.
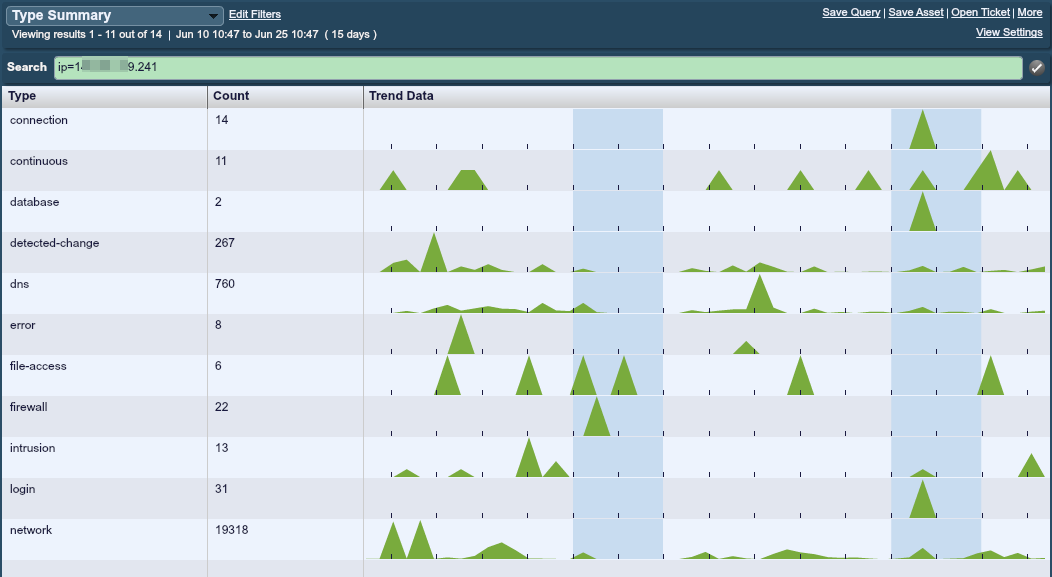
The 8 errors that occurred were all Windows Error crash reports that were sent to Microsoft concerning the niagarad.exe process. Below is an example log produced by PVS as an error reported by the system running the Niagara software:
Jun 12 08:52:26 pvs: AAA.BBB.CCC.DDD:49192|EEE.FFF.GGG.HHH:80|6|2284|Outbound Microsoft WinErr Message|GET{20}/StageOne/niagarad_exe/0_0_0_0/48971f87/niagarad_exe/0_0_0_0/48971f87/c0000005/0000fcaa.htmLCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=Dell%20Inc.&SPN=Precision%20WorkStation%20R5500&BV=A03&MID=8BB44017-C558-4958-ACCD-0AC1BA57950A&Queue=1{20}HTTP/1.1{0d}{0a}Connection:{20}Keep-Alive{0d}{0a}User-Agent:{20}MSDW{0d}{0a}Host:{20}watson.microsoft.com{0d}{0a}{0d}{0a}||NONE
One of the issues with ICS and SCADA devices is the difficulty in getting real-time activity logs. PVS continuous monitoring provides an excellent solution to this problem.
Conclusion
For traditional enterprise monitoring teams, keeping track of desktops, servers, firewalls, printers, and other devices is a constant endeavor. When control systems are found on the network, they are often deployed and managed outside of the realm of traditional enterprise IT staff. Solutions such as Nessus and PVS complement each other on the discovery and testing of ICS devices on your network and can help expose the risks associated with these devices.
Tenable has kept pace with new forms of detection for Nessus and PVS through extensive research, hands-on visits to SCADA labs, and partnerships with ICS Threat Intelligence provider Critical Intelligence and Digital Bond. If you are interested in performing this sort of research, please visit Tenable's careers page.
To learn more about our solutions for continuous monitoring of SCADA systems, visit Tenable’s SCADA security solutions page.
- SCADA

