by Josef Weiss
January 21, 2016
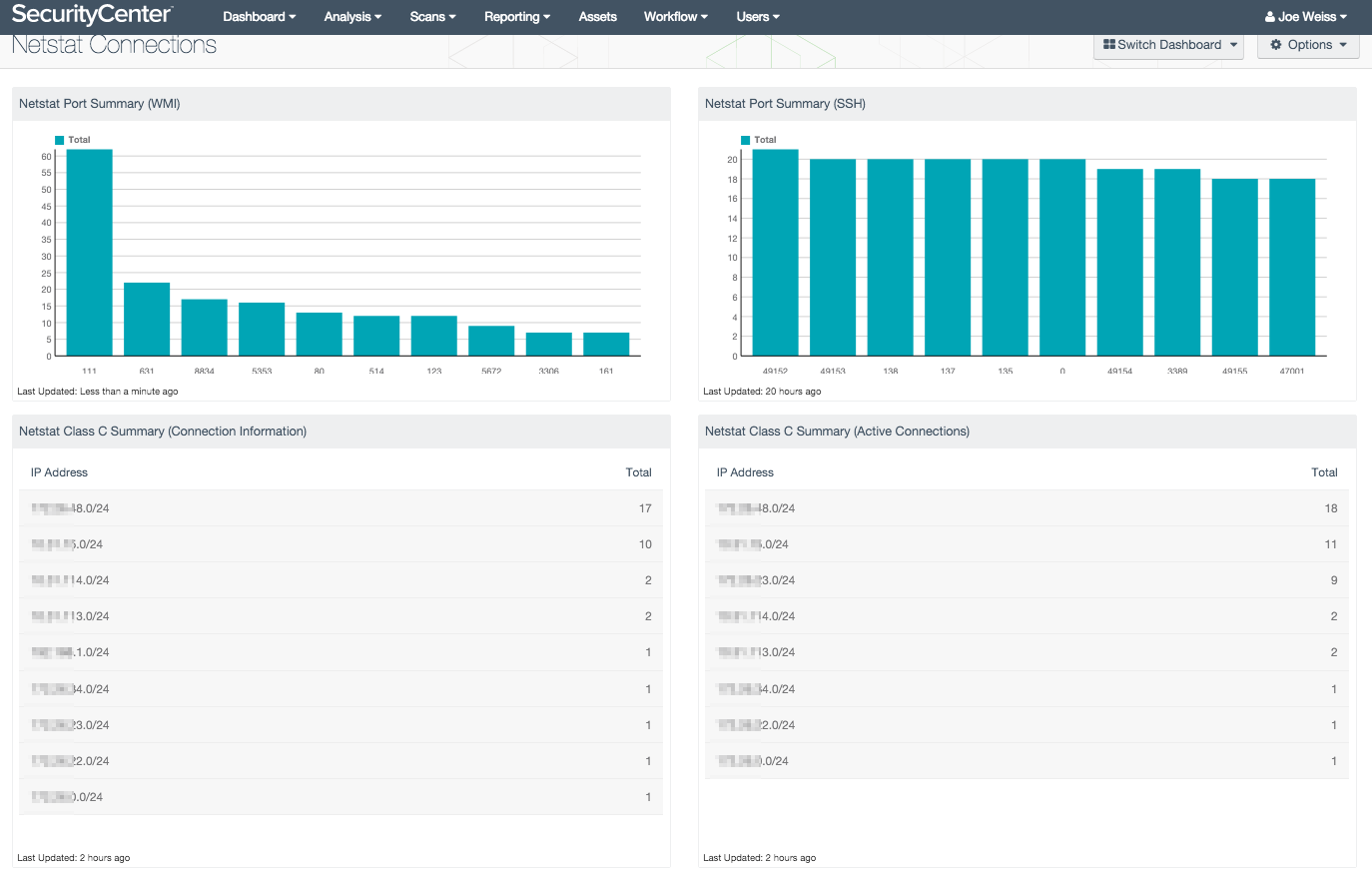
Netstat displays active connections for the Transmission Control Protocol (TCP), and lists the ports on which the computer is listening. Netstat is useful for displaying statistics and enumerating open ports on a given host and across multiple platforms. This dashboard utilizes Nessus netstat plugins to enumerate open ports via SSH and WMI. The top 10 results are displayed for both open ports and networks.
The Netstat Active Connections dashboard utilizes Nessus plugin 14272 Netstat Port Scanner (SSH), 34220 Netstat Port Scanner (WMI), 58651 Netstat Active Connections, and 64582 Netstat Connection Information. The netstat plugins run ‘netstat’ on the remote host to enumerate open ports. Plugin 34220 utilizes the Windows Management Instrumentation (WMI) implementation of netstat to enumerate open ports on Windows devices. Plugin 14272 utilizes Secure Shell (SSH) implementation of netstat to enumerate open ports on Linux/UNIX and Mac OS X based operating systems. Plugins 58651 and 64582 report connection information, displaying established connections to hosts.
An open port summary bar chart is present for both WMI and SSH, displaying the top 10 open ports that have been identified. A network summary table displays which open ports have been identified. Drilling down into the network summary table will present the analyst with an IP summary of individual hosts and the number open ports. Drilling into each host provides details on all ports that have been found to be active.
The Netstat Connections dashboard allows administrators to view netstat results without having to log into and execute the netstat command on each host individually. Added benefits include having the netstat results included into the vulnerability database for future reference or correlation.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring.
The dashboard requirements are:
- SecurityCenter 5.0.0
- Nessus 6.5.4
SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. SecurityCenter CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new types of regulatory compliance configuration audits. SecurityCenter CV allows for the most comprehensive and integrated view of network health.
The dashboard contains the following components:
- Netstat Port Scanner Port Summary (WMI) - This component utilizes Nessus plugin 34220 Netstat Port Scanner (WMI). The chart provides an open port summary displaying the top 10 open ports that have been identified. The chart allows administrators to view netstat results without having to log into and execute the netstat command on each host individually.
- Netstat Port Scanner Port Summary (SSH) – This component utilizes Nessus plugin 14272 Netstat Port Scanner (SSH). The chart provides an open port summary displaying the top 10 open ports that have been identified. The chart is useful allowing administrators to view netstat results for Linux, Unix, and Mac OS X systems without having to log into and execute the netstat command on each host.
- Netstat Class C Summary (Connection Information) – This component utilizes Nessus plugin 64582 Netstat Connection Information. The netstat plugins run ‘netstat’ on the remote host to enumerate open ports. A Class C summary table displays networks which have open ports identified by netstat as listening or established. Drilling into each host provides details on hosts that have listening ports or established connections.
- Netstat Class C Summary (Active Connections) - This component utilizes Nessus plugin 58651 Netstat Active Connections. The netstat plugins run ‘netstat’ on the remote host to enumerate open ports. A Class C summary table displays networks which have open ports identified by netstat as listening or established. Drilling into each host provides details about active established or listening TCP/UDP connections.