by Steve Tilson
July 18, 2014
Exploited (Secure Shell) SSH vulnerability attacks can be damaging to an organization if hosts are accessed and manipulated maliciously. SSH protocol is one of the most common protocols for device control and management. This dashboard provides information on all hosts with SSH vulnerabilities and trending SSH activity.
The SSH protocol provides a secure connection by utilizing encryption to secure the connection between two hosts, such as a client and server. Unix, Linux, Mac OS, and Windows 10 all include a built in SSH client. As security concerns and awareness grow for secure management of hosts in all industries, organizations are turning to SSH as an effective way to protect their networks against attacks with encryption. Tenable.sc CV™ assist those organizations embracing SSH protocol to quickly find vulnerabilities that may be exploited if not properly mitigated. Many of these vulnerabilities are linked to open source software that lead to catastrophic exploitation such as the Heartbleed bug.
This dashboard provides several components that track SSH traffic and log interaction with devices. Tracking and logging SSH traffic can assist analysts in finding unauthorized/malicious scanners and observe SSH usage across the network for normal and abnormal usage. Analysts can use this dashboard for a look at the vulnerabilities associated with SSH and their severity. This dashboard provides detailed information identifying critical and high device vulnerabilities for administrators to mitigate and secure before management of a device is compromised.
The dashboard and components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection.
The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.4.0
- NNM 5.9.0
- LCE 6.0.0
Tenable's Tenable.sc Continuous View® (Tenable.sc CV™) provides continuous network monitoring, vulnerability identification and security monitoring. Tenable.sc CV™ is continuously updated with information about advanced threats, zero-day vulnerabilities and new types of regulatory compliance configuration audit files. Tenable constantly analyzes information from unique sensors, delivering continuous visibility and critical context, and enabling decisive action that transforms a security program from reactive to proactive. Active scanning periodically examines the applications on the systems, the running processes and services, web applications and configuration settings. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Tenable.sc CV™ provides an organization with the most comprehensive view of the network and actionable information to support mitigation efforts and reduce cyber risk. Managers can better monitor and asses SSH usage across the network with Tenable.sc CV™. Tenable enables powerful, yet non-disruptive, continuous monitoring that will provide organizations with the information needed to reduce risk within the enterprise.
This dashboard contains the following components:
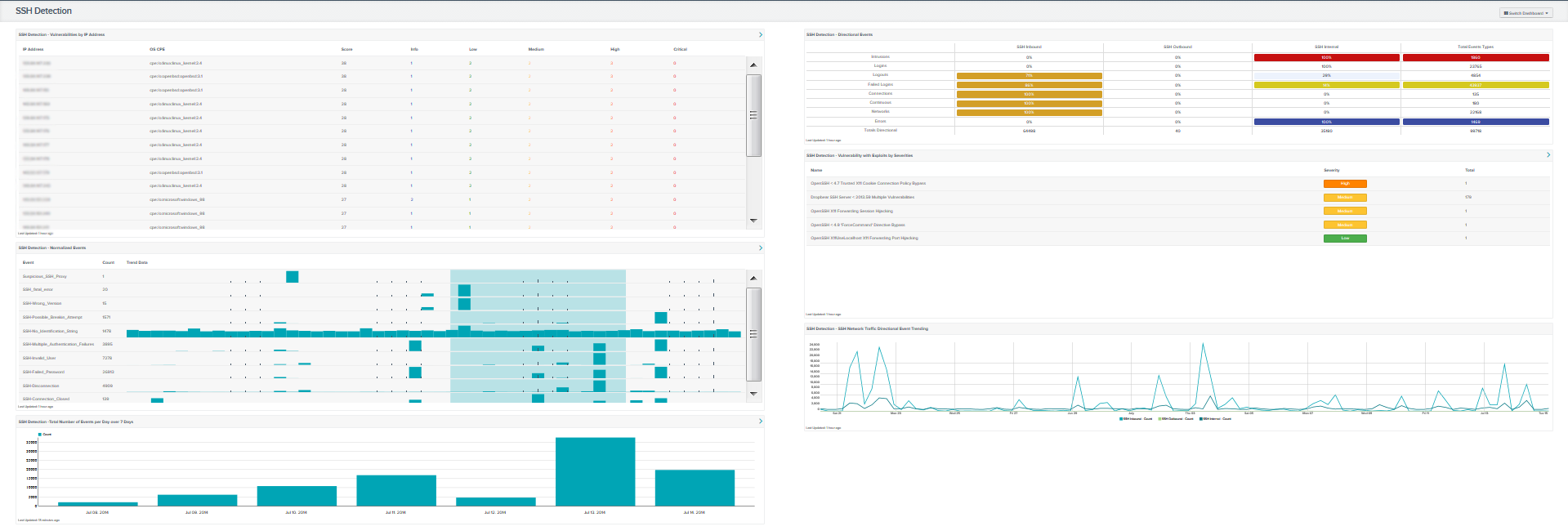
- SSH Detection - Vulnerabilities by IP Address: This component provides a table of the top 20 SSH vulnerable systems. The table is sorted by vulnerability weight score. The columns displayed are IP Address, OS, Score, and by each vulnerability severity (info, low, medium, high, and critical). The severity columns will have total vulnerability count in each severity cell.
- SSH Detection - Directional Events: This component provides a table of SSH network traffic directional flow by 8 event types. The event types used are Intrusion, Login, Logout, Failed Login, Connection, Continuous, Networks, and Errors. Tenable.sc defines network traffic flow as internal, inbound and outbound. Understanding SSH traffic patterns allows IT security teams to have a better view of SSH usage within the network. The Total Event Types column displays a count of all of the respective events, while the remaining three columns show the percentage of events according to directional flow.
- SSH Detection - Normalized Events: This component displays normalized events from Tenable.sc over the past seven days. The fields displayed are: normalized events names, total events, and a trend graph for events collected over the past 7 days.
- SSH Detection - Vulnerability with Exploits by Severities: This component displays the top exploitable SSH vulnerabilities for both servers and clients. The table columns are: vulnerability name, family, severity, and total vulnerabilities, which are sorted by severity level.
- SSH Detection -Total Number of Events per Day over 7 Days: This component displays the total number of SSH events per day over a 7 day period. Any increase or decrease of SSH events indicates a change in the normal SSH activity.
- SSH Detection - SSH Network Traffic Directional Event Trending: This component displays SSH network traffic directional event trending flow over 25 days. The traffic flow is represented using the directional filters internal, inbound, and outbound. Monitoring for inbound and outbound SSH traffic will vary based on the network configuration. Network administrators should review network traffic trends to determine if traffic is following normal usage patterns.