by Andrew Freeborn
August 19, 2016
An important part of most organizations is the “secret sauce” or data used to keep the business competitive in their market. Organizations place a lot of value both monetarily and intrinsically on this specific data, which is necessary to keep them successful. Competitors are always looking for ways to acquire the data for a competitive edge or even put the other organization out of business. With this constant threat, organizations need to ensure appropriate controls are in place to protect their data.
Network devices set boundaries that help defend an organization from attacks and protect confidential data. Analysts can configure network devices to control authorized inbound and outbound data transfer, and also ensure controls are working as expected. Depending on the needs of the organization, data may flow in and/or out of the organization to meet regulatory and/or partner requirements. Specific network controls need to be in place to correctly allow data to flow in and/or out of the network.
When specific network traffic flows are configured, analysts need to ensure that only what is required is allowed to flow in or out of the network. Boundaries, such as network destination, need to be defined along with the protocol, such as SMB. Once administrators have implemented appropriate network rules, analysts should ensure the Tenable Passive Vulnerability Scanner (PVS) is appropriately inline with the same network devices. PVS detects patterns in the network traffic to alert analysts to malicious activity along with analyzing expected network activity.
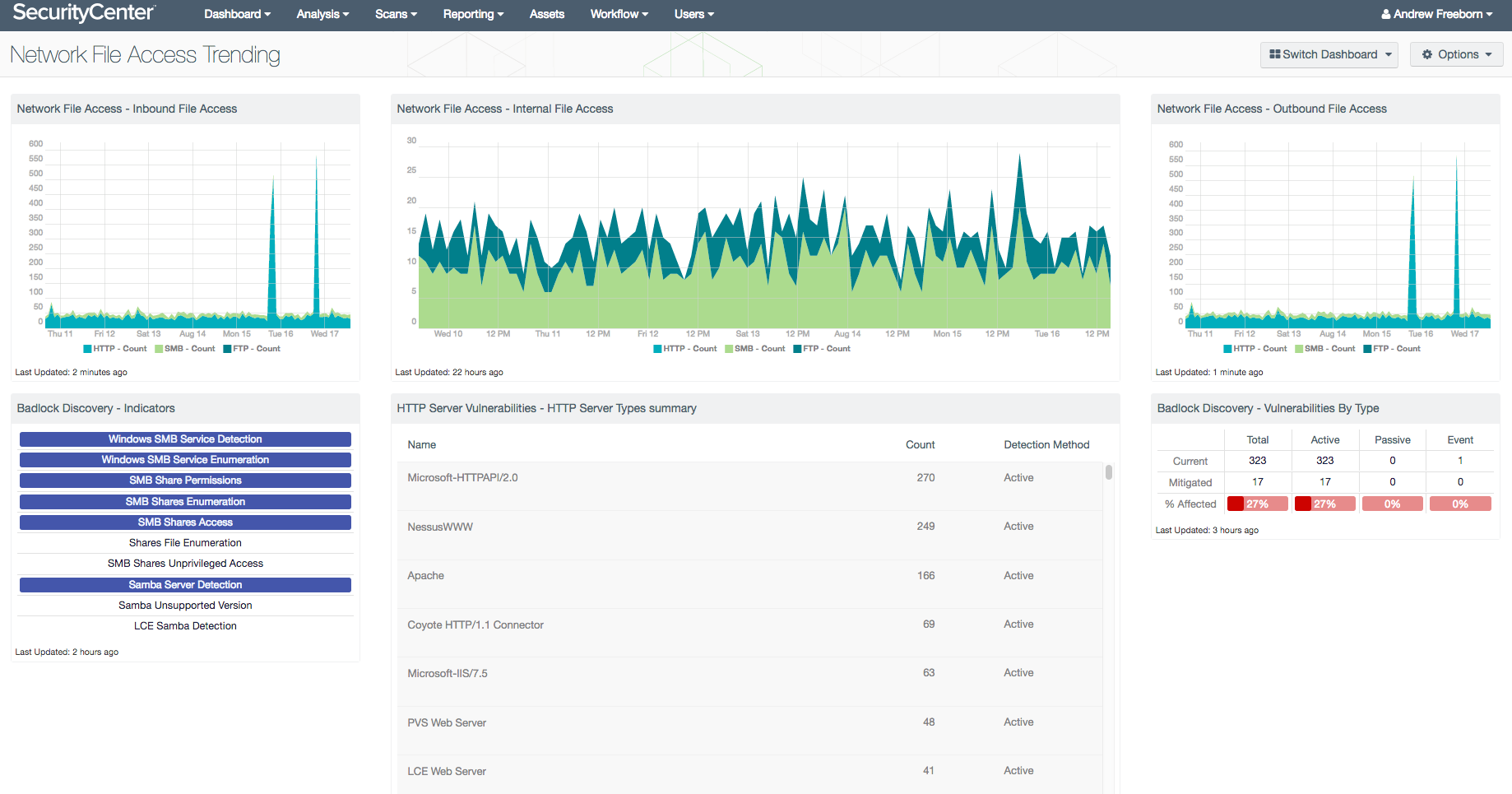
Within this dashboard, analysts can ensure that approved file access protocol activity is operating as expected. Analysts can monitor the network traffic leaving, entering, and moving within the organization at the protocol level, such as HTTP, FTP, and SMB. With a view of these protocols moving in different network directions, analysts can determine if unintentional data leakage is occurring within the network. Expected network activity could include inbound HTTP activity, but outbound SMB activity may be a sign of malicious activity.
SMB activity on a network within the internal network space is usually a common occurrence. However, when SMB activity leaves or enters external network devices, analysts should ensure this activity is warranted. The dashboard provides insight into this specific activity when PVS is set at appropriate network locations within the organization. Components within the dashboard are focused on SMB, HTTP, and FTP, but analysts can quickly modify the components to focus only on SMB. With the recent SMB vulnerability known as “Badlock” causing concern, additional components focus on SMB and HTTP vulnerabilities. Additionally, analysts can add protocols such as Remote Desktop Protocol (RDP) to monitor and see if this activity is detected crossing the network boundary. Analysts using PVS along with Tenable Nessus and Tenable Log Correlation Engine (LCE) can monitor for vulnerabilities around these protocols and ensure data flows in appropriate and expected network directions.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. This report can be easily located in the SecurityCenter Feed under the category Discovery & Detection. The dashboard requirements are:
- SecurityCenter 5.4
- Nessus 6.8.1
- PVS 5.1
- LCE 4.8
Tenable SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, and security monitoring. SecurityCenter CV is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audit files. Tenable constantly analyzes information from our unique sensors, delivering continuous visibility and critical context, enabling decisive action that transforms your security program from reactive to proactive. Active scanning examines the protocols available on the systems, running processes and services, detection of vulnerable applications, configuration settings, and additional vulnerabilities. With this information, analysts have greater insight to determine if supported protocols are operating within the organization. Continually monitoring the network with passive sensors for servers, desktops and applications helps prioritize security efforts to mitigate threats and weaknesses. Organizations continue to operate with more mobile and transient network devices and need to have a system in place that continuously monitors traffic, data, devices, applications, and communications across environments. Tenable enables powerful, yet non-disruptive, continuous monitoring of the organization to ensure vulnerability data is available to analysts.
This dashboard contains the following components:
- Network File Access - Inbound File Access: This trend line chart component displays the last seven days of inbound file access activity across the FTP, SMB, and HTTP protocols
- Badlock Discovery - Indicators: The Indicators matrix contains cells that filter for specific Samba and SMB detections
- Network File Access - Internal File Access: This trend line chart component displays the last seven days of internal file access activity across the FTP, SMB, and HTTP protocols
- HTTP Server Vulnerabilities - HTTP Server Types Summary: The “HTTP Server Types summary” table component identifies the various versions of web platforms detected in the organization
- Network File Access - Outbound File Access: This trend line chart component displays the last seven days of outbound file access activity across the FTP, SMB, and HTTP protocols
- Badlock Discovery - Vulnerabilities By Type: The Vulnerabilities by Type matrix displays the counts of current and mitigated Badlock vulnerabilities detected by plugin type