by David Schwalenberg
March 7, 2016
The North American Electric Reliability Corporation (NERC) is a not-for-profit international regulatory authority whose mission is to assure the reliability of the bulk power system in North America. NERC Reliability Standards define the reliability requirements for planning and operating the North American bulk power system, which serves more than 334 million people. NERC is committed to protecting the bulk power system against cyber security compromises that could lead to misoperation or instability. The NERC Critical Infrastructure Protection (CIP) Standards provide a cyber security framework for the identification and protection of Bulk Electric System (BES) Cyber Systems, to support the reliable operation of the North American bulk power system.
The purpose of CIP-002 (BES Cyber System Categorization) is "to identify and categorize BES Cyber Systems and their associated BES Cyber Assets for the application of cyber security requirements commensurate with the adverse impact that loss, compromise, or misuse of those BES Cyber Systems could have on the reliable operation of the BES." Utility networks rely on Supervisory Control and Data Acquisition (SCADA) systems, but because of reliability and real-time operational requirements, these systems are often not replaced, upgraded, or patched in a timely manner. Thus, SCADA systems are often critically vulnerable and without even basic modern security controls. Increasingly, these systems are also being connected to the Internet, which increases the danger of compromise and malicious attacks.
For organizations that are required to be CIP compliant, Tenable.sc Continuous View (CV) can lead the way to compliance. This dashboard can assist in identifying SCADA systems, active ports, and events. SCADA vulnerabilities are also displayed. Using the Nessus Network Monitor (NNM) and the Log Correlation Engine (LCE), Tenable.sc CV can track network protocol usage, allowing for easy identification of SCADA systems and ports. PVS uses a non-intrusive approach to passively identify vulnerabilities on sensitive systems. Nessus can add more in-depth vulnerability discovery using active credentialed scans. This dashboard can assist an organization in understanding the SCADA systems and activity on the network, which will aid in meeting the CIP-002 requirements and measures. Analysts can also use this dashboard to easily drill down and gain more detailed information.
The CIP standards recommend categorizing BES Cyber Assets into different impact categories. An asset's impact category is based on the adverse impact to BES reliability that would occur if the asset was unavailable, degraded, or misused. Once the impact categories of systems have been determined, asset groups in Tenable.sc CV can be used to group together machines in each impact category. Asset groups can then be applied to this dashboard to narrow the focus and enable more accurate reporting on systems in specific impact categories. For more information on using assets with dashboards, see How to Add Assets in SecurityCenter and How to Use Assets with Dashboards. Alternatively, if the assets are in separate subnets, then subnet filters can be easily applied to narrow the focus of this dashboard.
This dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- SecurityCenter 5.2.0
- Nessus 8.4.0
- NNM 5.8.1
- Industrial Security 1.3.2
- LCE 6.0.0
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution. For Supervisory Control and Data Acquisition (SCADA) systems, where reliability and not interfering with normal operations is a concern, Tenable.sc CV includes passive vulnerability detection with Tenable’s Nessus Network Monitor (NNM), as well as log correlation with Tenable’s Log Correlation Engine (LCE). Where possible, active vulnerability detection and compliance scanning with Nessus can also be done. Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its SCADA network.
The following components are included in this dashboard:
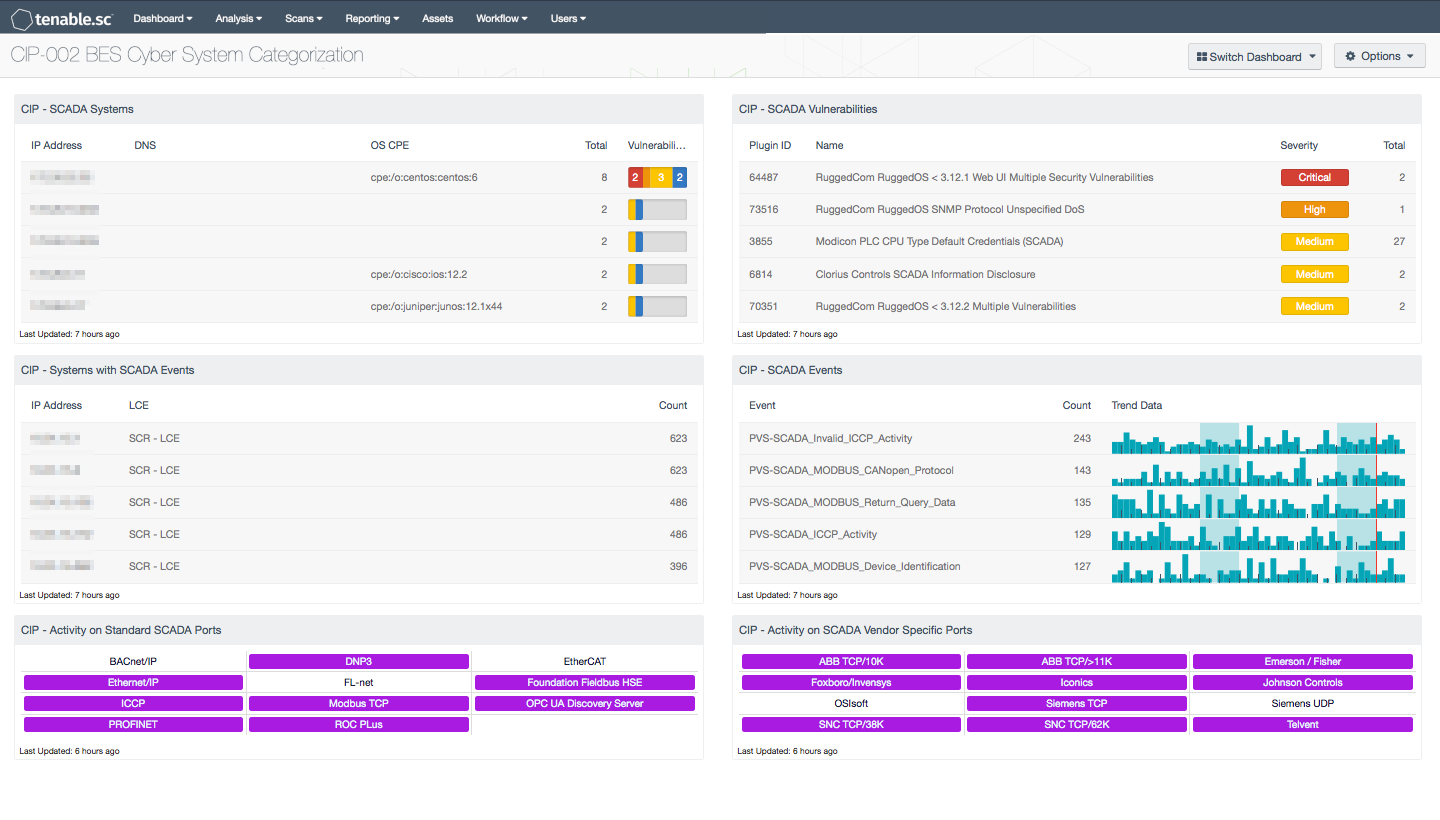
- CIP – SCADA Systems: This table presents the IP addresses of actively and passively detected SCADA systems, and provides a vulnerability summary for each.
- CIP – Systems with SCADA Events: This table presents the IP addresses of systems on which SCADA events were collected and normalized by the LCE within the past 15 days.
- CIP – Activity on Standard SCADA Ports: This matrix component presents indicators of detected network activity on standard ports used by SCADA protocols.
- CIP – SCADA Vulnerabilities: This table presents the current actively and passively detected SCADA vulnerabilities.
- CIP – SCADA Events: This table presents the SCADA events collected and normalized by the LCE within the last 15 days.
- CIP – Activity on SCADA Vendor Specific Ports: This matrix component presents indicators of detected network activity on ports used by specific SCADA vendors.