by David Schwalenberg
February 19, 2014
Many successful network attacks and data breaches can be traced back to weak authentication practices. Accounts with well-known default passwords – or even worse, no passwords – can be easily exploited by a network intruder. Poor configuration settings allow weak credentials or weak authentication practices that can enable an attacker to easily compromise the network. Failure to monitor suspicious account activity can result in intruders or insiders accessing sensitive data. Critical systems can be compromised and information can be destroyed or exfiltrated. These issues can lead to devastating consequences for an organization, potentially jeopardizing the organization's competitiveness and long-term survival.
This dashboard will enable an organization to recognize account and authentication weaknesses. Components on this dashboard present vulnerabilities related to accounts and credentials, such as default accounts, blank passwords, vulnerabilities that allow bypassing authentication, and detected insecure accounts. Non-compliant account and password settings are also presented. Potentially suspicious login activity is also noted to bring attention to accounts that are more threatened and require greater protection. Using the information on this dashboard, the organization can reduce the chance of a data breach by eliminating weak passwords, default accounts, and lax policies. Analysts can use this dashboard to easily drill down into the data presented and gain more detailed information.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- Tenable.sc 5.4
- Nessus 8.5.1
- NNM 5.9.0
- LCE 6.0.0
- Compliance data
Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in securing and controlling access. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find account and credentials vulnerabilities and enumerate system information. Audit files can be used to assess compliance with authentication policies. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security investments is analyzed to monitor user activity across the network. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure user authentication, control access, and safeguard sensitive information.
This dashboard contains the following components:
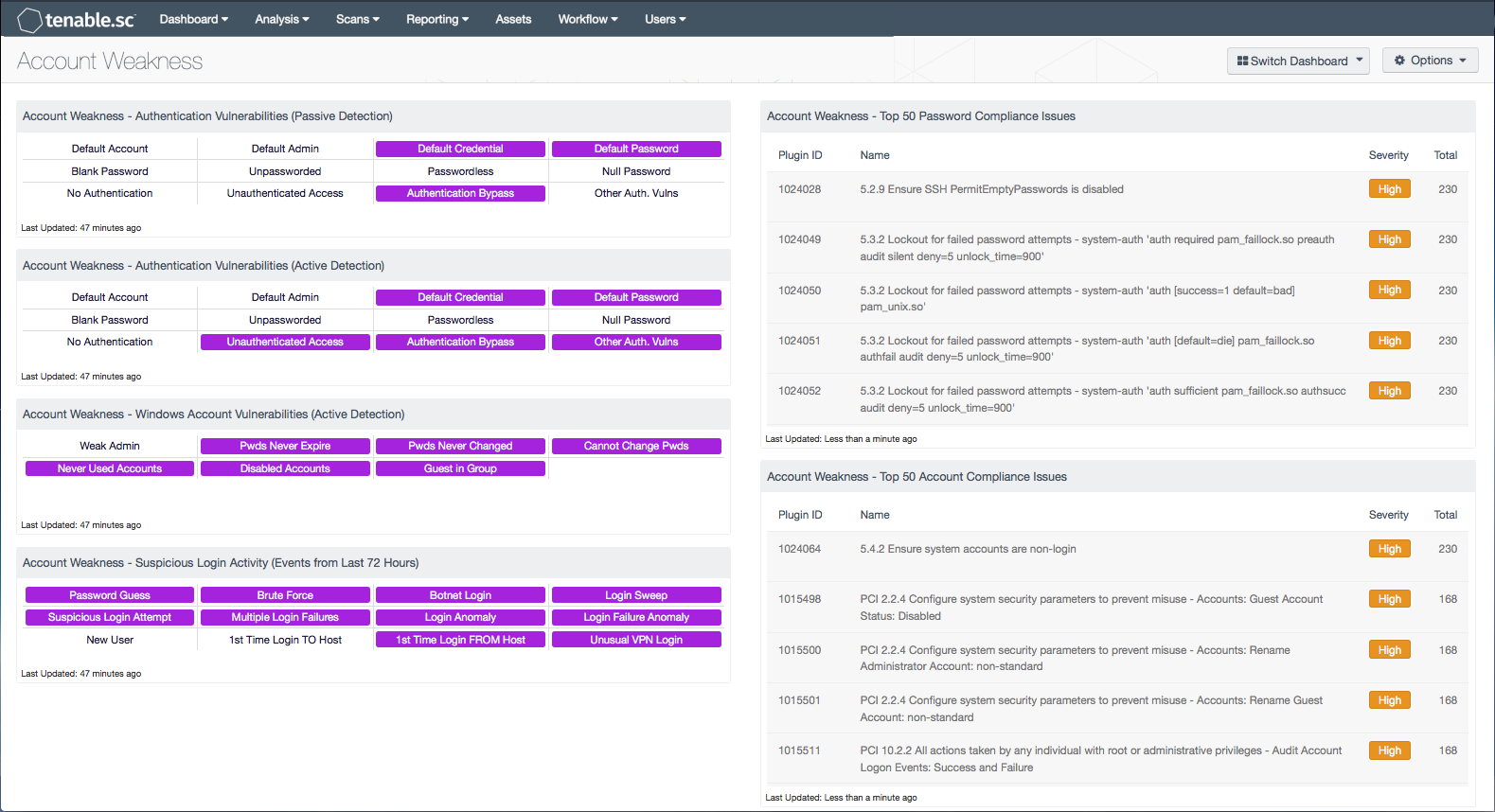
- Account Weakness – Authentication Vulnerabilities (Passive Detection)
This matrix shows passive detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name. - Account Weakness – Authentication Vulnerabilities (Active Detection)
This matrix shows active detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name. - Account Weakness – Windows Account Vulnerabilities (Active Detection)
This matrix shows active detections of Windows account vulnerabilities. - Account Weakness – Suspicious Login Activity (Events from Last 72 Hours)
This matrix shows potentially suspicious login activity. This activity can bring attention to accounts that are more threatened and require greater protection. - Account Weakness – Top 50 Password Compliance Issues
This table displays the top 50 compliance issues with “password” in their name. Note that in order for data to appear in this table, appropriate audit/compliance scans must first be run on the network. - Account Weakness – Top 50 Account Compliance Issues
This table displays the top 50 compliance issues with “account” in their name. Note that in order for data to appear in this table, appropriate audit/compliance scans must first be run on the network.