Tenable Cloud Security
Unified Cloud Native Application Protection Platform (CNAPP)

With Tenable Cloud Security you can easily ramp up security across all your AWS, Azure and GCP environments. From full asset discovery and deep risk analysis to runtime threat detection and compliance, you can reduce complexity, minimize your cloud exposure and enforce least privilege at scale. Tenable's comprehensive approach accurately visualizes and prioritizes security gaps, and gives you the built-in expertise and tools you need to remediate risks that matter most.
Request a Demo
Global Leaders Choose Tenable Cloud Security
Tenable Cloud Security brings immediate value as an exceptionally user-friendly CNAPP multi-cloud solution that simplifies cloud complexity and, through precise contextual analysis, enables teams to efficiently identify and address accurately prioritized security gaps. As a leader in securing cloud identity, Tenable also helps you achieve a least privilege and zero trust strategy. It accelerates the adoption of DevSecOps through accurate security findings and detailed remediation steps that developers trust.
White Paper: Holistic Security for AWS, Azure and GCP
Comprehensive CNAPP: Secure Your Cloud and Cloud Identities
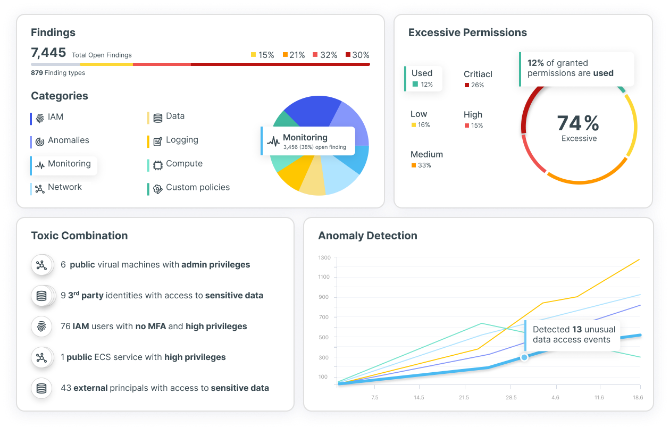
As a full CNAPP solution, Tenable Cloud Security enables you to secure your cloud infrastructure from development to runtime. It continuously analyzes all your cloud resources — across infrastructure, workloads, data, identities and applications — to single out the most important risks, spot unknown threats and deliver actionable insights within hours. The solution also addresses a key risk to your cloud infrastructure — identities — by detecting, prioritizing and remediating risky entitlements and misconfigurations at scale.
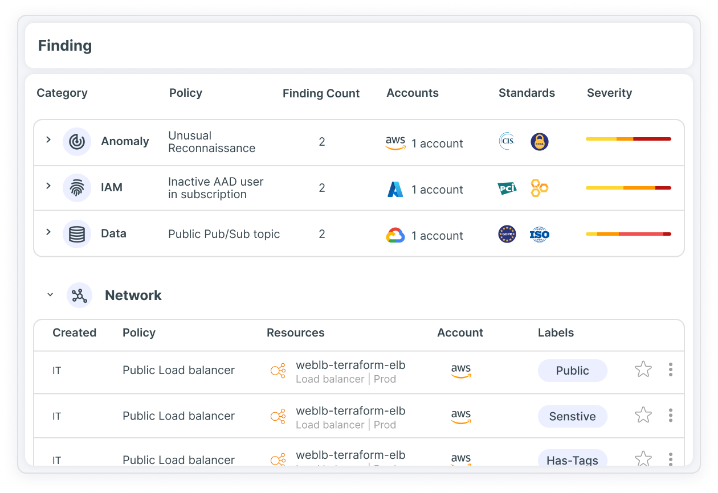
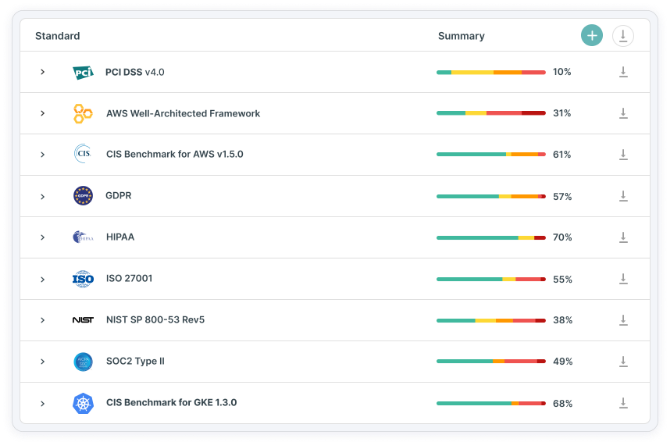
Cloud Security Posture Management (CSPM) and Compliance
Monitor risk by continuously reviewing and assessing cloud environment settings and configurations. By mapping discovered risks against security standards and policies, you can attain and maintain compliance and regulation management across multi-cloud environments.
Learn More: CSPM Continuous Cloud Security
Cloud Infrastructure Entitlement Management (CIEM)
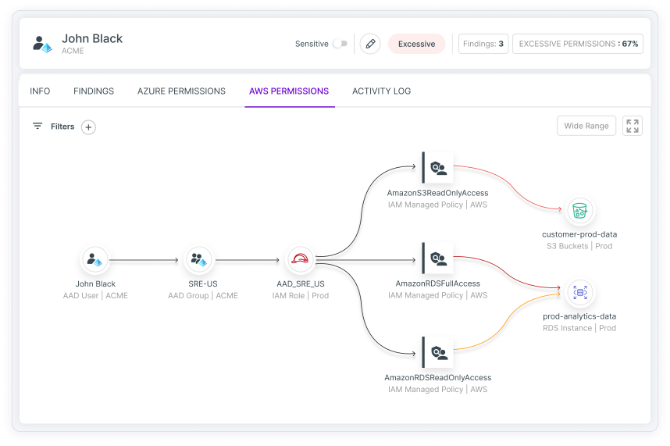
Gain actionable visibility into all identities and entitlements, and full risk context that reveals and prioritizes hidden dangers like toxic combinations and privilege escalation. Control your access entitlements with auto-remediation of excessive permissions and unused entitlements. Tenable CIEM is the most comprehensive and accurate solution for managing human and service identities in cloud infrastructure environments and achieving least privilege at scale.
White Paper: Why Managing Cloud Entitlements is Nearly Impossible
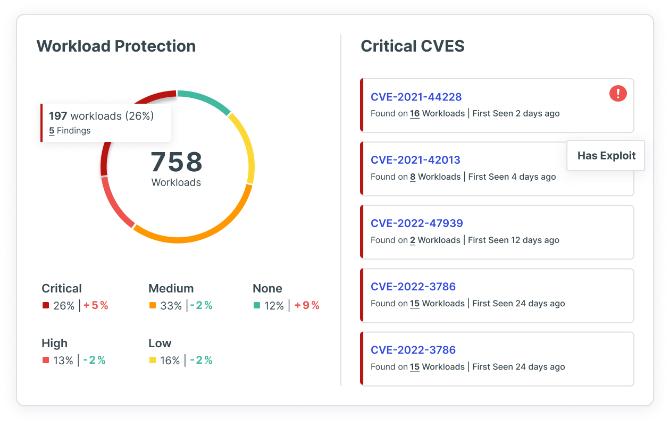
Cloud Workload Protection (CWPP)
Continuously scan, detect and visualize your most critical workload risks, including vulnerabilities, sensitive data, malware and misconfigurations, across virtual machines, containers and serverless functions.
Blog: Cloud Workload Protection (CWPP) Best Practice – Focus on Impact, Not Volume
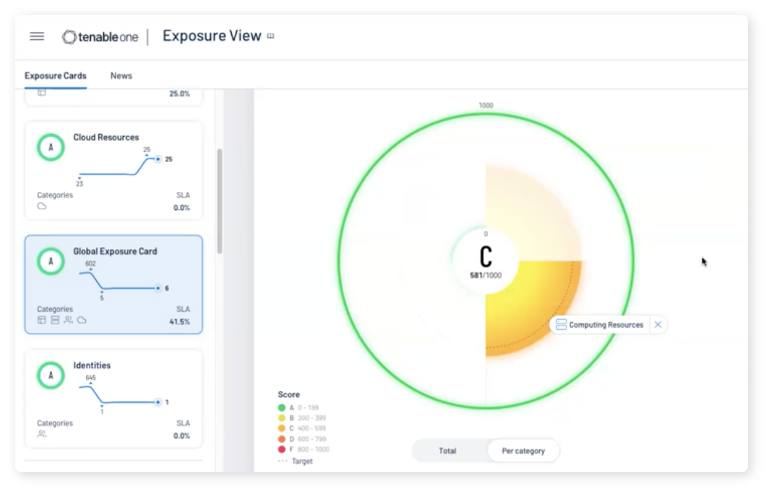
Available Through Tenable One Exposure Management Platform
Tenable One is an exposure management platform designed to help your organization gain visibility across your modern attack surface, focus efforts to prevent likely attacks, and accurately communicate cyber risk to support optimal business performance. The Tenable One platform offers broad vulnerability coverage spanning IT assets, cloud resources, containers, web apps and identity systems.
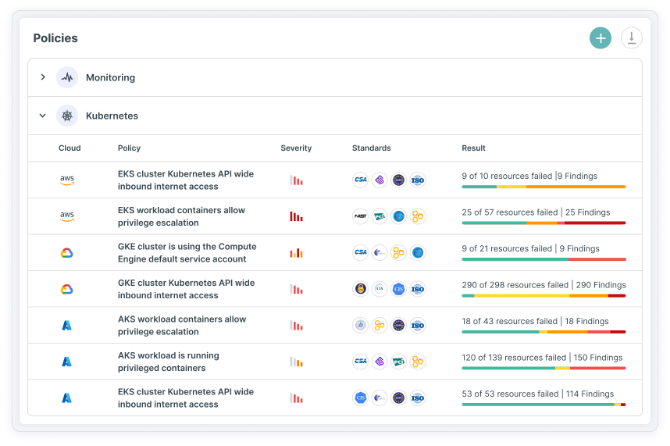
Learn MoreKubernetes Security Posture Management (KSPM)
Reveal, prioritize and remediate security gaps and automate compliance for Kubernetes clusters across your cloud infrastructure. Using Tenable Cloud Security you can unify visibility into Kubernetes container configurations and empower stakeholders with steps to mitigate misconfigurations.
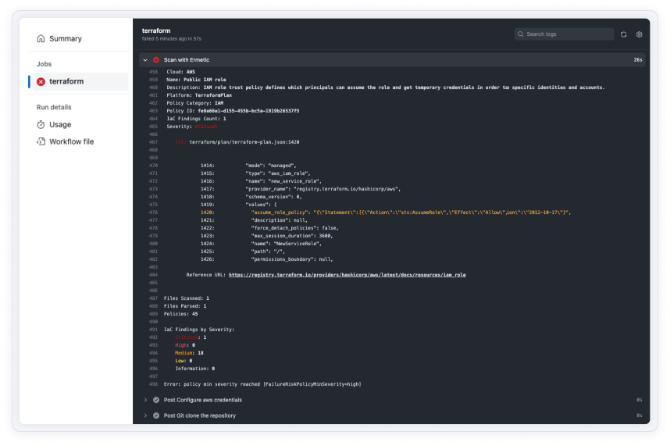
Infrastructure as Code Security (IaC)
Shift left on security by enabling developers to scan, detect and fix misconfigurations and other risks in IaC to harden your cloud infrastructure as part of the CI/CD pipeline. Tenable’s CNAPP solution enables teams to embed security into workflows in DevOps tooling including Hashi Terraform and AWS CloudFormation, and automatically remediate prioritized findings in their native IaC environments.
Learn More: IaC Security
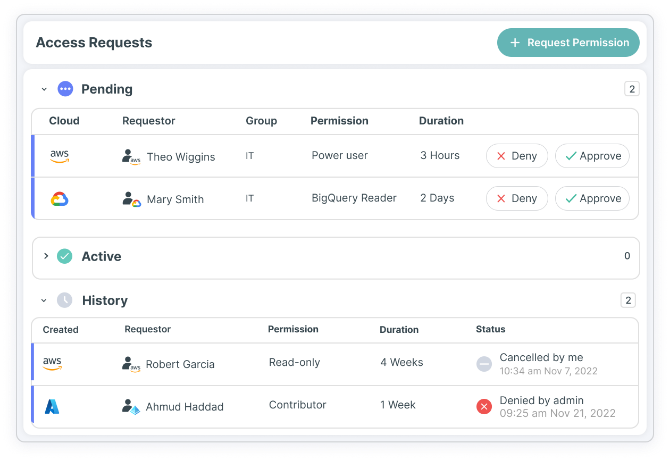
Just-In-Time (JIT) Access
Grant developers speedy approval for as-needed, time-limited access and avoid long-standing privileges, while reducing your cloud attack surface. Tenable’s CNAPP solution offers temporarily elevated access that enforces fine-grained least privilege policies — minimizing risk while addressing business needs.
Learn More: Secure Your Public Cloud with Just-in-Time Access
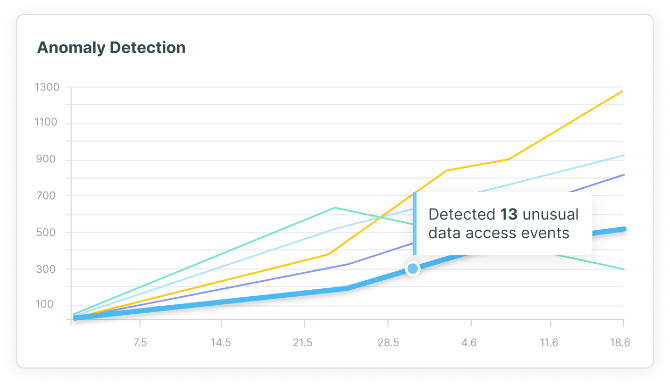
Cloud Detection and Response
Improve your cloud security posture by automating threat detection with continuous behavioral analysis and anomaly detection against built-in and custom policies. Tenable Cloud Security examines enriched cloud provider logs to provide context around each risk, enabling your SecOps teams to rapidly investigate and remediate. You can also query data using intuitive tools and easily integrate with SIEMs (Splunk, IBM QRadar, etc.) and ITSMs (ServiceNow, Jira, etc.) to help you further accelerate response times.
Learn More: Anomaly Detection and Response
“This is one of the few platforms I’ve brought into the cloud that has had actionable efforts in under 30 days. From a return on investment perspective, it was one of the best decisions we made.”
David Christensen, Sr. Information Security Executive, FinTech Enterprise