Tenable
Security Center
Expose and close your cyber weaknesses with the world’s #1 vulnerability management solution—managed on-prem.
Reduce risk across your IT infrastructure. The solution that created the category continues to raise the bar to protect enterprises from critical cyber exposures that increase business risk.
Request a demo
The world’s #1 vulnerability management solution managed on-prem
Know your IT vulnerabilities
Take full advantage of active scanning, agents, passive monitoring, external attack surface management and CMDB integrations to gain the visibility you need to reveal impactful vulnerabilities across your environment.
Expose priority IT gaps
Use the industry’s most extensive CVE coverage to quickly and confidently spot priority exposures with a high likelihood of attack and business impact.
Close critical exposures
Take rapid, decisive action with Tenable Predictive Prioritization technology–with vulnerability data, threat intelligence and data science–to close critical exposures and execute remediations.
The Tenable Security Center suite
Customized to meet your needs, the Tenable Security Center suite of products gives you the visibility and context you need to understand your risk and fix vulnerabilities fast.
Tenable Security Center
- Risk-based vulnerability management, on-prem
- Immediate visibility into your network with unlimited Nessus scanners
- Clear, actionable insight into data with highly customizable dashboards, reports and workflows
- Instantly identify and prioritize vulnerabilities using built-in risk scores and contextualized threat intelligence
- Speed up incident response with customizable configuration alerts, notification and ticketing
- Free API access for customer integrations, data acquisition and data enrichment
- Discover unknown assets on your external attack surface
Tenable Security Center Plus
Includes all Tenable Security Center benefits as well as:
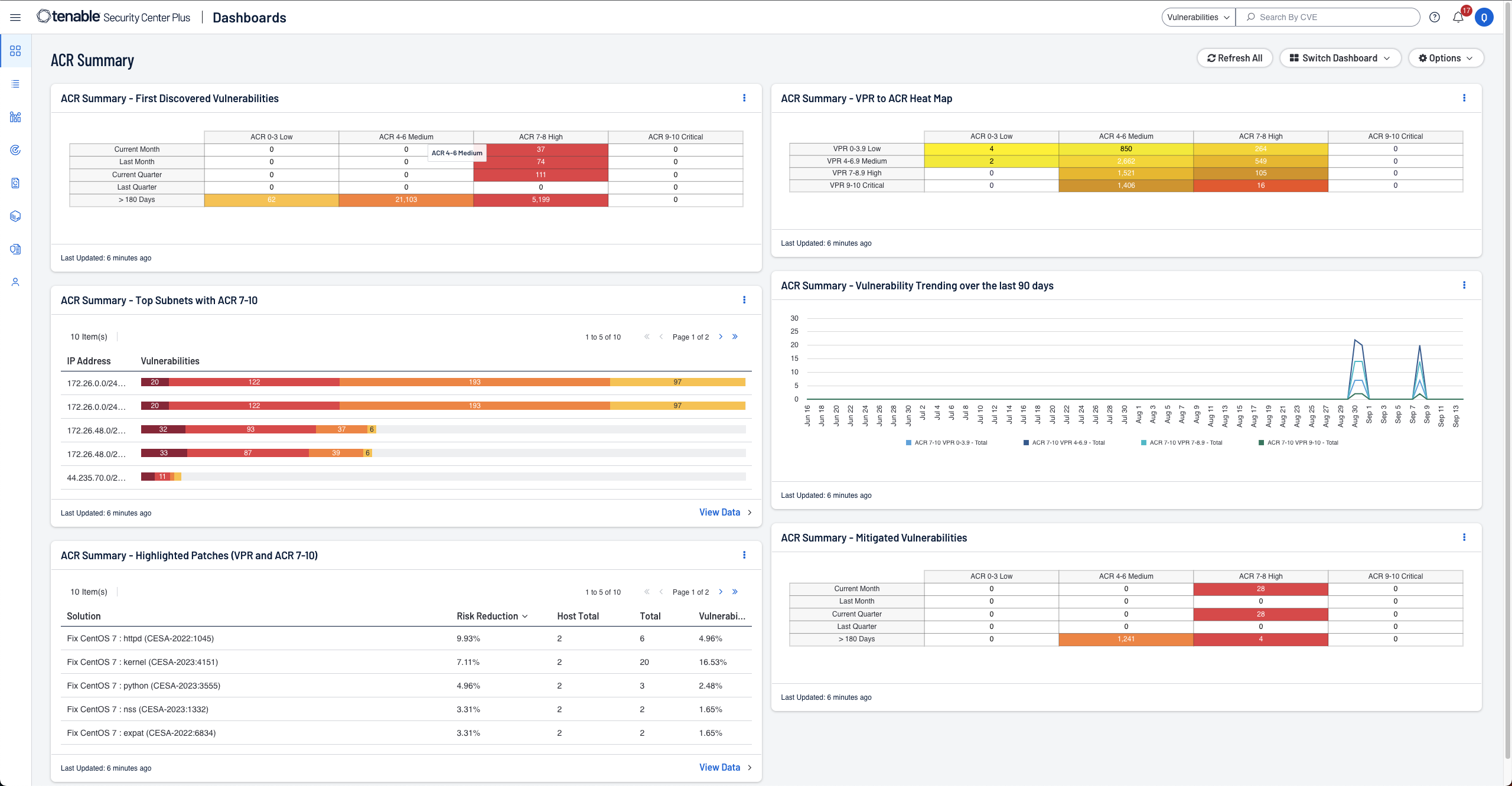
- Gain a deeper understanding and context of your assets using Asset Criticality Rating (ACR)
- Real-time asset and vulnerability discovery and continuous monitoring for the highest level of visibility
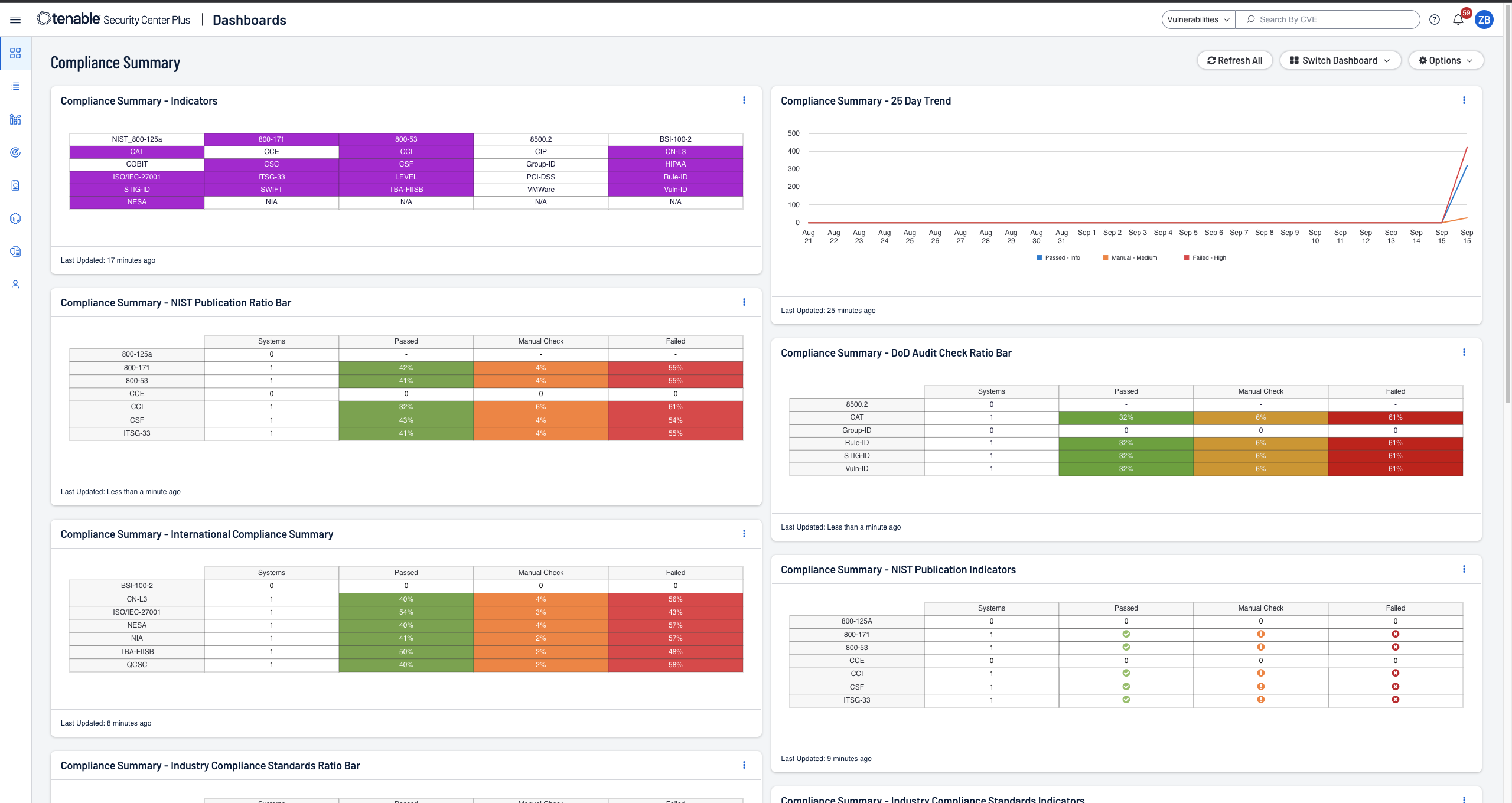
- Streamlined compliance reporting with real-time metrics and proactive alerts on violations
- Real-time detection of botnets and command and control traffic
- Identification of previously unknown resources, changes in behavior and new application usage
Tenable Security Center Director
For customers with multiple Tenable Security Center consoles, Tenable Security Center Director is available as an add-on to Tenable Security Center or Tenable Security Center Plus.
- Single pane of glass to view and manage your network across all Tenable Security Center consoles
- Easily view scans for each Tenable Security Center console from one central location
- Centralized insight to facilitate reporting and uptime of multiple consoles, scanners and assets
- Centralized reporting across multiple Tenable Security Center consoles to easily measure your cyber risk
Quickly measure and analyze security and compliance risk
-
Manage your data, your way
Discover Tenable Security Center, the leading on-premises solution for vulnerability management. Take charge of your data management with flexible on-premises or hybrid deployment options, all while reducing risk for your organization. -
Understand asset criticality
Tenable Security Center Plus introduces Asset Criticality Rating (ACR), enriching your understanding of asset importance. Equip yourself with the knowledge needed to make informed decisions in mitigating risks for your organization. -
Proactively contextualize threats
Search, contextualize and respond to vulnerabilities based on rich sources of data and intelligence backed by Tenable Research. See how -
Get instantaneous data insight
Leverage more than 350 pre-built, highly customizable dashboards and reports to get clear, actionable insight into the data you need to easily identify threats. -
Tailor reports with ease
Craft different reports designed for specific audiences, ensuring that critical threats receive immediate attention. Generate reports on-demand or schedule them and automatically share with the appropriate recipients. -
Simplify compliance reporting
Stay compliant with immediate visibility into your compliance posture. Easily demonstrate adherence with predefined checks against industry standards and regulatory mandates. -
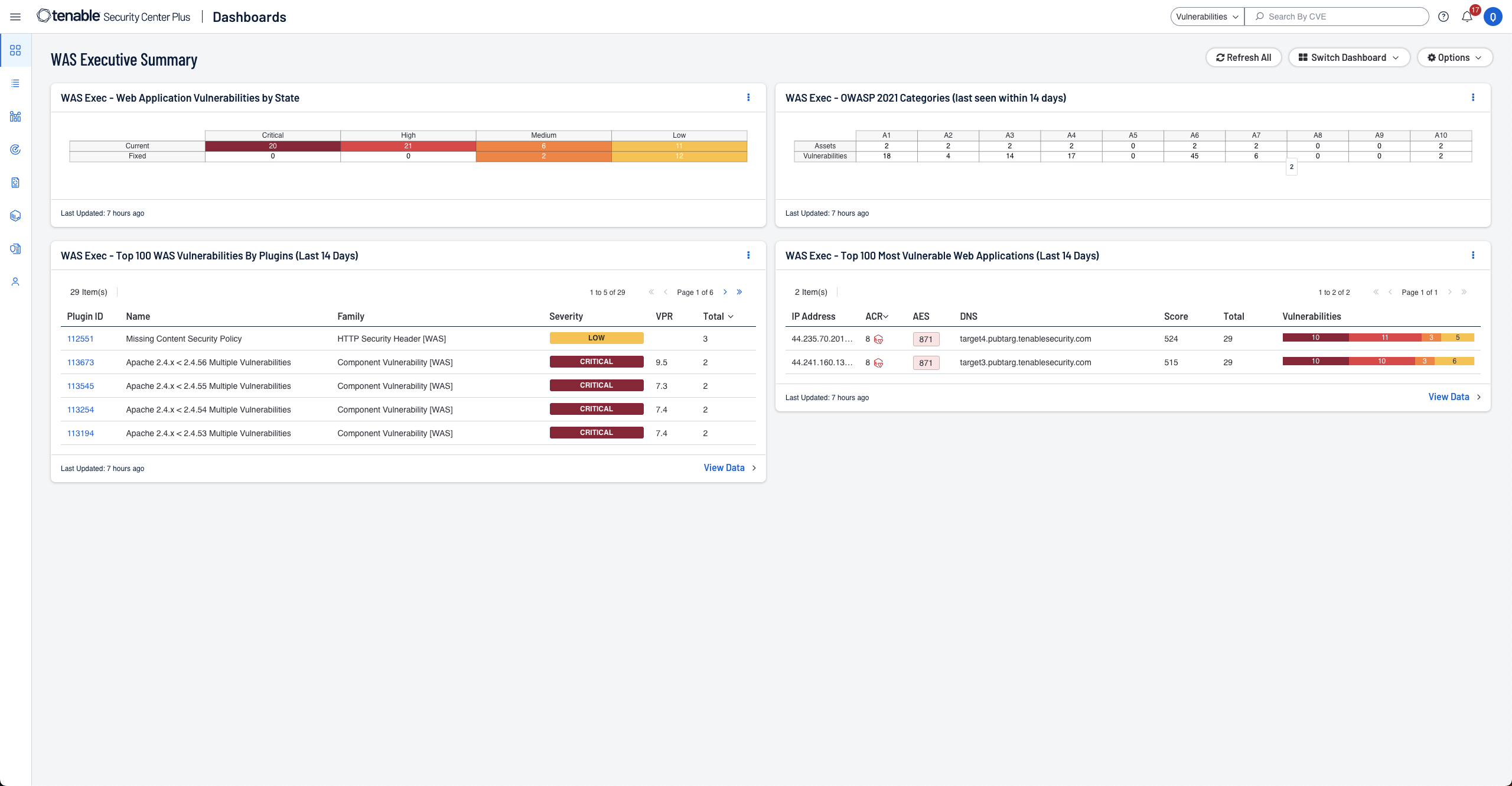
On-prem web app scanning
Integrate on-prem Tenable Web App Scanning within your Tenable Security Center UI. Automate scans, assess web app vulnerabilities and streamline assessments with user-friendly, modern web app vulnerability scanning. -
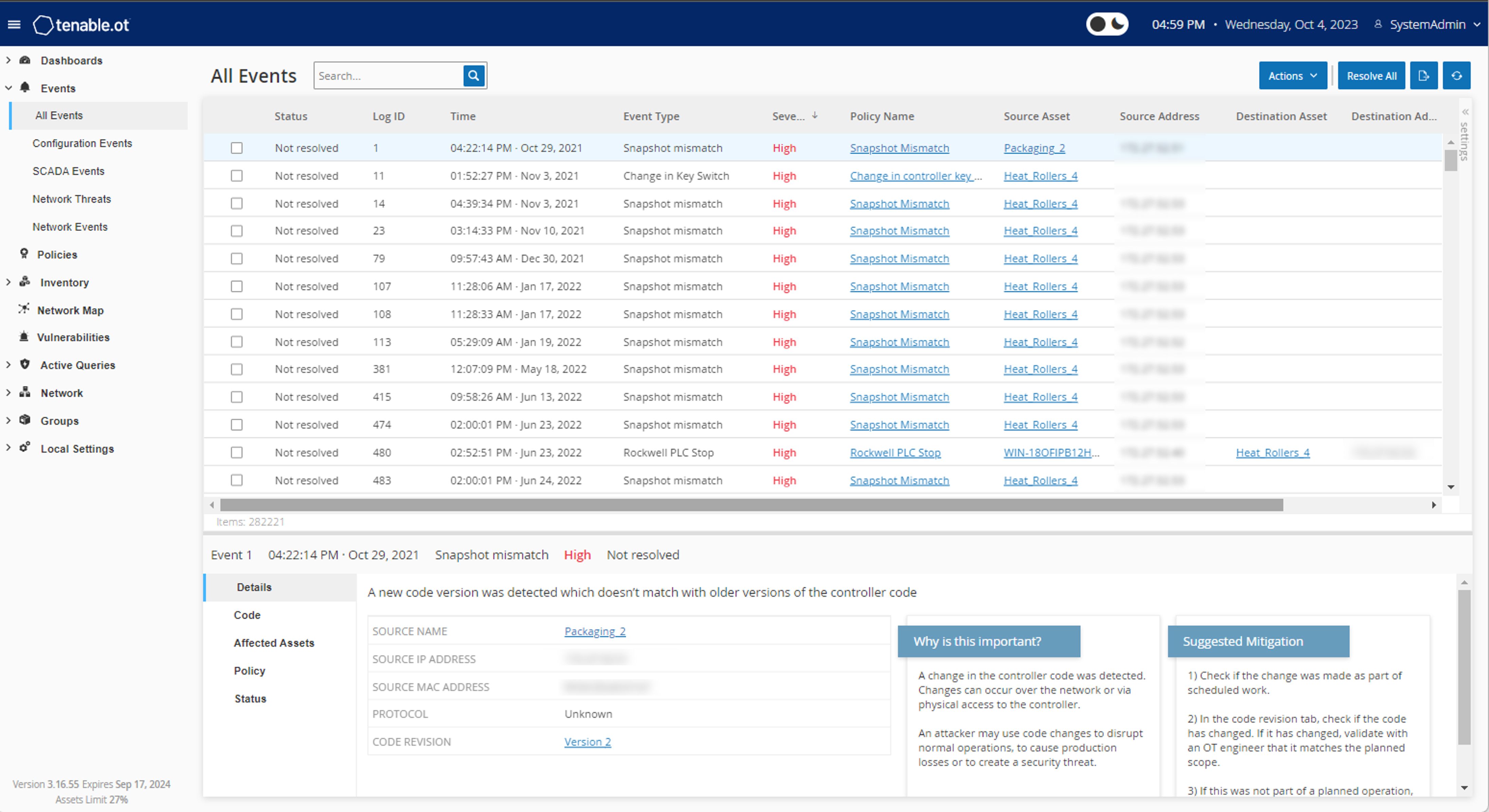
Enhance Operation Technology (OT) visibility
Gain complete visibility, security and control over the OT threats that put your organization at risk with the Tenable OT Security integration. -
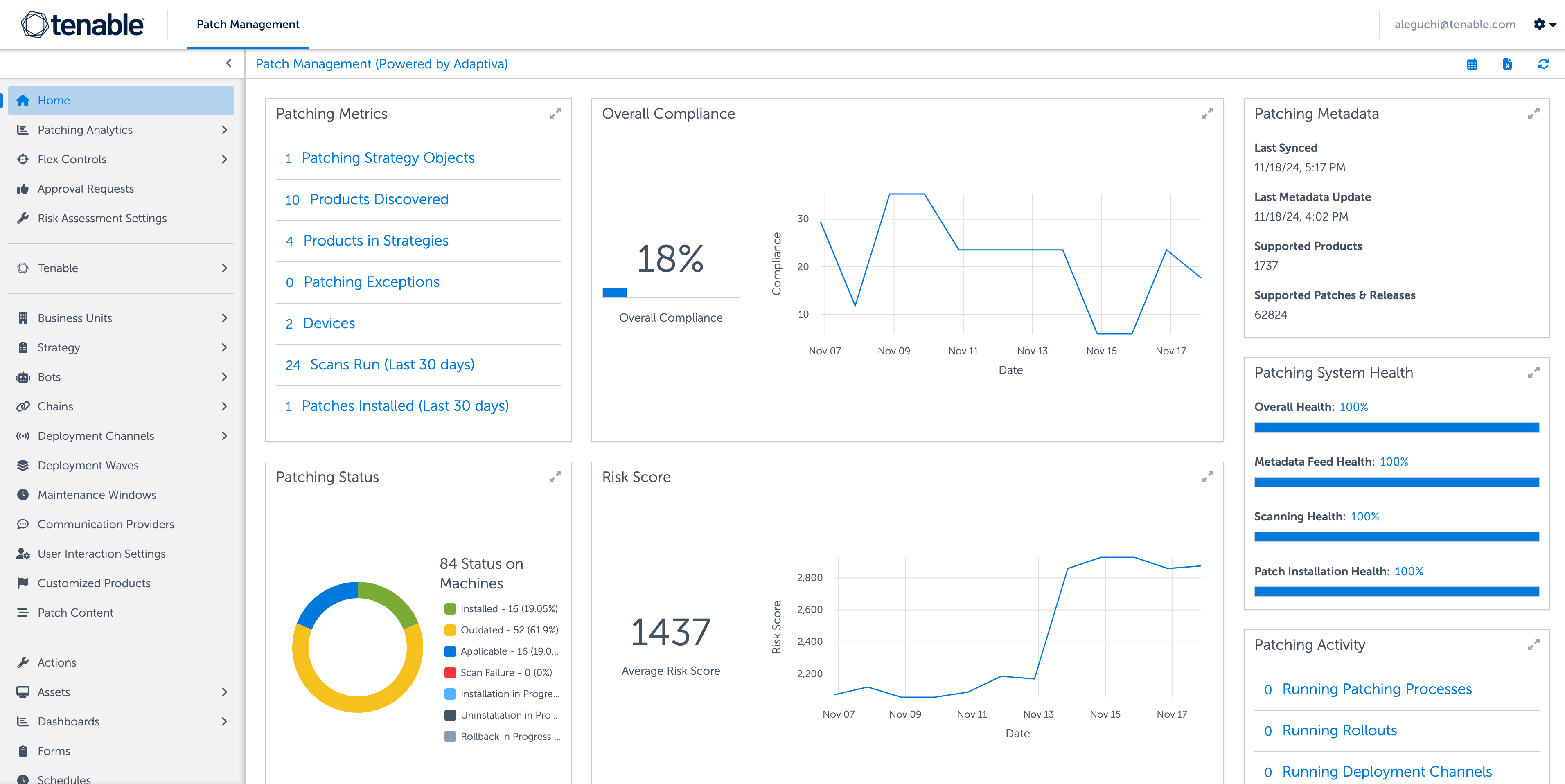
Close your vulnerability exposure
Pair autonomous patch functionality with Tenable’s leading vulnerability coverage, built-in prioritization, threat intelligence and real-time insight to shorten the mean time to remediate (MTTR). See how
Tenable Security Center reviews
Tenable is the only vendor to be named a Customers’ Choice in the 2025 Gartner® Peer Insights™ Voice of the Customer for Vulnerability Assessment

Available through Tenable One: The world’s only AI-powered exposure management platform
Tenable One solves the central challenge of modern security: a deeply divided approach to seeing and doing battle against cyber risk. We remove risk by unifying security visibility, insight and action across the attack surface to rapidly expose and close gaps. Customers use Tenable One to eradicate priority cyber weaknesses and protect against attacks—from IT infrastructure to cloud environments to critical infrastructure and everywhere in between.
Learn more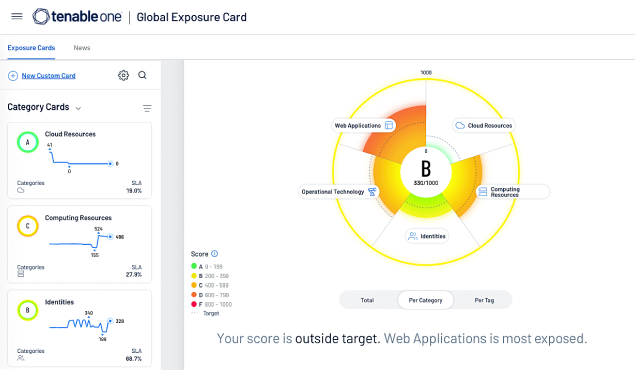
Tenable Security Center has become the voice of truth for our network, providing an additional layer of insight to hold ourselves accountable and to validate the success of our security program to our board of directors.
FAQs
What is Tenable Security Center?
-
Tenable Security Center and Tenable Security Center Plus are Tenable’s on-premises vulnerability management solutions. Built on industry-leading Nessus technology, the Tenable Security Center family of products identifies, investigates and prioritizes vulnerabilities, providing you with a risk-based view of your security and compliance posture. For more information on these solutions, please see the Tenable Security Center Data Sheet and Tenable Security Center Plus Data Sheet.
What is the difference between Tenable Security Center and Tenable Security Center Plus?
-
Tenable Security Center Plus is a vulnerability management platform that builds off of the functionality in Tenable Security Center and includes additional risk metrics, such as Asset Criticality Rating (ACR), for an additional layer of context for your assets and vulnerabilities. These metrics provide a more tailored approach to your vulnerability management program, all calculated on your Tenable Security Center Plus instance, so your data remains on-premises. Additionally, Tenable Security Center Plus can integrate with Tenable’s Exposure Management platform, Tenable One, to increase the value of the insights provided by Security Center Plus.
Does Tenable Security Center work with Tenable One?
-
Yes! Tenable Security Center Plus integrates with Tenable One to provide hybrid vulnerability management deployments and allow on-premises customers to take advantage of an exposure management platform.
What is Tenable One?
-
Tenable One is an exposure management platform to help organizations gain visibility across the modern attack surface, focus efforts to prevent likely attacks and accurately communicate cyber risk to support optimal business performance. The platform combines the broadest vulnerability coverage spanning IT assets, cloud resources, containers, web apps and identity systems, builds on the speed and breadth of vulnerability coverage from Tenable Research and adds comprehensive analytics to prioritize actions and communicate cyber risk. Tenable One allows organizations to:
- Gain comprehensive visibility across the modern attack surface
- Anticipate threats and prioritize efforts to prevent attacks
- Communicate cyber risk to make better decisions
What is Tenable Security Center Director?
-
Tenable Security Center Director is an add-on to Tenable Security Center. It provides enterprise customers with a unified view across their large and often dispersed network spanning multiple Tenable Security Center consoles. Tenable Security Center Director gives complete visibility and management of your instances so you can focus on vulnerability management and reduce overhead on administrative tasks.
Does Tenable Security Center work with Tenable Web App Scanning?
-
With Tenable Security Center, Tenable enhances your defenses by adding on-premises web application security. Seamlessly integrated into the Security Center UI, Tenable Web App Scanning empowers you to identify and address vulnerabilities across your network and web applications, bolstering your security posture.
Tenable Web App Scanning is a dynamic application security testing (DAST) tool which thoroughly assesses web applications. It crawls the web app to create a site map, then scans the front end to detect vulnerabilities in custom code and third-party components.
What is Predictive Prioritization and how does it help prioritize vulnerabilities?
-
Predictive Prioritization combines Tenable-collected vulnerability data with third-party vulnerability and threat data and analyzes them together with the advanced data science algorithm Tenable Research developed. Each vulnerability receives a Vulnerability Priority Rating (VPR) that represents the likelihood an attacker may exploit a given vulnerability in the next 28 days along with its severity. You can use VPR to understand actual cyber risk of vulnerabilities in their unique environments so you can prioritize remediation efforts on vulnerabilities with the greatest impact.
How does Tenable Security Center find assets and vulnerabilities?
-
Using a diverse array of sensors, Tenable Security Center ensures continuous discovery and assessment of your network, assets and vulnerabilities in real-time.
Tenable Security Center gathers security data from across your organization using sources such as:
- Passive monitoring: Monitoring network traffic and events in real-time provides information on which assets are connected to the internet and how they communicate. It identifies new or never-before-seen devices or applications and detects suspicious behavior as it happens.
- Active scanning: Thoroughly analyzes asset state to identify vulnerabilities, misconfigurations, malware and other weaknesses.
- Host data: Actively monitors host activities and events, including insight into access and changes.
- Intelligent connectors: Leveraging your other security investments, Tenable Security Center can integrate additional security data to improve context and analysis. Both will analyze information from a wide range of data sources including Active Directory (AD), configuration management databases (CMDBs), patch management systems, mobile device management (MDM) systems, cloud platforms, web applications and more.
- Agent scanning: Instantly audit transient or hard-to-scan assets that intermittently connect to the internet without credentials. Once installed, agents can run credentialed scans without ongoing host credentials.
What are Nessus Agents? How do they work with Tenable Security Center?
-
Nessus Agents are lightweight programs installed locally on a host — a laptop, virtual system, desktop and/or server. Agents receive scanning instructions from a central Nessus Manager server, perform scans locally, and report vulnerability, compliance and system results back to the central server. Nessus Agents are available with Tenable Vulnerability Management and Tenable Security Center.
Nessus Agents with Tenable Security Center increase scan coverage and remove blind spots by making it easier to scan problematic assets such as those needing ongoing host credentials and offline assets. Agents also enable large-scale concurrent scanning with little network impact.
For more information on Nessus Agents, see the following resources:
How many types of vulnerabilities does Tenable Security Center detect?
-
Tenable Research backs Tenable Security Center, delivering world-class cyber threat intelligence, data science insights, alerts and security advisories. Tenable has one of the most extensive vulnerability and intelligence data sets in the industry with the highest CVE coverage of more than 79,000 CVEs and more than 476 Zero Days disclosed since January 2019. Tenable updates its vulnerability database each day, as new vulnerabilities emerge. Tenable Research delivers more than 100 new detections each week.
What happens after Tenable Security Center detects a vulnerability?
-
After Tenable Security Center detects a vulnerability, it provides you with detailed insight for each vulnerability detected, including:
- Vulnerability information: Name and description of the vulnerability, remediation guidance, date of discovery and date of last vulnerability observation, CPE, date patch published, patching status, plugin ID and details
- Host information: Host name, affected hosts, IP address, DNS, Mac address, NetBIOS, repositor
- Risk information: Vulnerability severity, VPR score, CVSS score and vectors, vulnerability age, known exploits, exploit code maturity, product coverage, threat intensity, threat recency, threat sources, percentage risk reduction associated with patching
What are Tenable Security Center reporting capabilities?
-
Tenable Security Center provides extremely flexible reporting capabilities, utilizing more than 350 pre-built templates and a user-friendly report creation interface to easily create customized reports. The HTML5-based reports consolidate data from across your organization so you can measure and analyze your security effectiveness. Working from existing templates, you can completely customize data by deleting or adding certain components or adjusting filters to develop reports to meet your various needs.
You can develop multiple reports, each customized to provide a different view of collected data so you can deliver informative and timely reports to the appropriate teams or decision-makers within your organization. Reports can range from extremely detail-oriented to high-level summaries. Reports are available in standard PDF and CSV formats. You can schedule and automatically email reports, share to one or more specified console users and/or publish to one or more sites upon completion.
You can also use Tenable Security Center to comprehensively and automatically report on your network compliance with complex standards such as PCI and NIST.
Can Tenable Security Center help maintain compliance?
-
Yes. Tenable Security Center can help maintain compliance. It enables you to stay compliant with immediate visibility into your compliance posture. You can easily demonstrate adherence with predefined checks against industry standards and regulatory mandates such as ISO/IEC 27001/27002, PCI, NIST Cybersecurity Framework, NIST SP 800-171 and CIS Critical Controls.
Tenable Security Center provides out-of-the-box, fully customizable reports and dashboards specific to leading security standards and compliance mandates. You can use them “as-is” or easily tailor them to meet your specific security and business needs. For example, you can easily create specific reports and dashboards for individual lines of business.
What is Tenable AI Aware?
-
Tenable AI Aware is a feature within Tenable Vulnerability Management and Tenable Security Center that helps organizations monitor and mitigate the risks associated with the rapid adoption of AI technologies. It leverages advanced detection technologies, including agents, passive network monitoring, dynamic application security testing, and distributed scan engines, to identify unauthorized AI solutions, detect AI vulnerabilities, and illuminate unexpected AI or Large Language Model (LLM) development. AI Aware provides a comprehensive security-first approach to managing AI-related risks by offering deep visibility into AI software, libraries, and browser plugins across an organization’s digital ecosystem. Learn more about Tenable AI Aware here.
What is External Attack Surface Management (EASM)?
-
External Attack Surface Management is a capability offered by Tenable that provides visibility into blind spots outside of your network perimeter. This allows customers to scan their domain to find previously unknown internet-connected assets that can pose high risk to your organization.
Is External Attack Surface Management included in Tenable Security Center?
-
Yes, External Attack Surface Management capabilities are offered with Tenable Security Center. If you require additional domains, frequency and/or metadata in your results you can purchase our Tenable Attack Surface Management add-ons.
What is Tenable Patch Management?
-
Tenable Patch Management is a patch management module pairing Tenable’s industry-leading prioritization capabilities with autonomous patch functionality. Automated correlation between vulnerabilities and the most up-to-date remediation action help your teams overcome the bottleneck that can occur between vulnerability prioritization and remediation. Built to scale up or down to fit any organization, Tenable Patch Management enables your organization to precisely manage settings with granularity around deployments, testing, approvals, applications and more.
To leverage Tenable Patch Management, you need a license for Tenable Security Center, Tenable Vulnerability Management, Tenable One or Tenable Enclave Security. Learn more here.
Does Tenable Security Center integrate with other products?
-
Yes. Tenable Security Center integrates with other products. The suite provides out-of-the-box integrations to leverage Tenable's vulnerability insights with ticketing, patch management, SIEM, SOAR and other third-party products. Visit the Technology Ecosystem page to learn more about available integrations and ecosystem partners. You can also use Tenable Security Center’s API to develop custom integrations.
Additionally, Tenable Security Center has built-in integrations with Tenable OT Security, Tenable Web App Scanning and Tenable Patch Management. Tenable Security Center Plus integrates with Tenable One, which provides hybrid vulnerability management deployments and allows on-premises customers to take advantage of an exposure management platform.
How is Tenable Security Center priced and licensed?
-
Tenable Security Center is licensed by annual subscription and priced by IP. Perpetual licensing is also available.
Where can I find Tenable Security Center documentation?
-
You can find technical documentation for Tenable Security Center and all Tenable products at https://docs.tenable.com/.
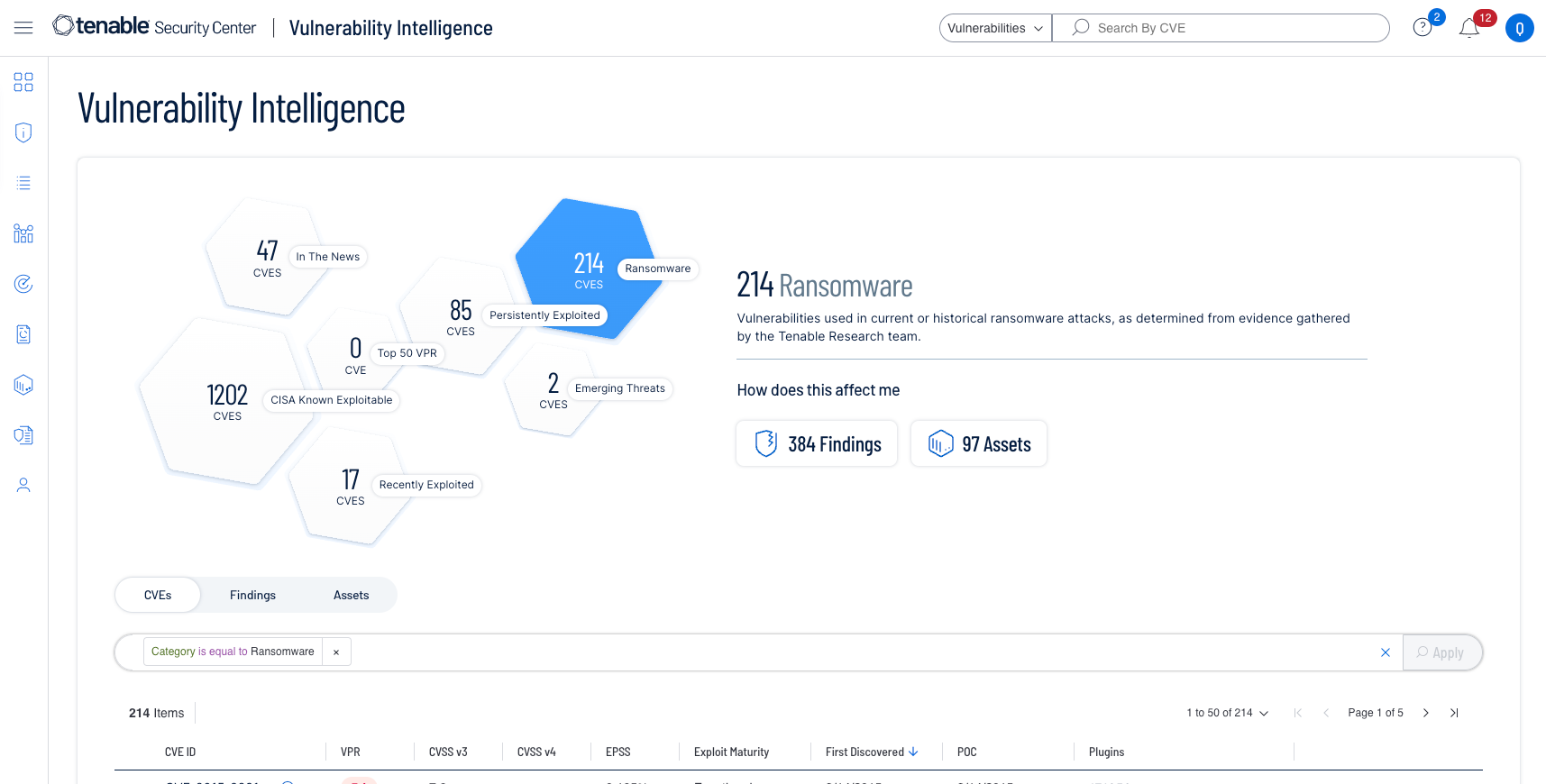
- What is Vulnerability Intelligence?
-
Vulnerability Intelligence provides actionable insights for vulnerability management based on both external data sources and internal vulnerability data. It provides vital context on any given vulnerability to understand how likely it is an attacker may exploit it and a window into the impact on your environment.
Vulnerability Intelligence brings Tenable’s extensive vulnerability research information, data science insights, security response and your vulnerability management data together in one unified place. You can easily search, contextualize and respond to vulnerabilities based on this rich intelligence and report to management the impact which vulnerabilities have on your organization.
Related products
Related resources
Get a demo of Tenable Security Center
Please fill out the form with your contact information and a sales representative will contact you shortly to schedule a demo.
- Tenable Security Center