Remediation Prioritization with Curated Vulnerabilities using Nessus (aka #CaughtWithPantsDown)

Almost every day we face the constant challenge of choosing from things that need our urgent attention and ones that are important. How we classify and prioritize these items largely reflects our true character. Procrastinate enough, and it doesn't take long for important items to become urgent. Fail to distinguish urgent items from the important, and it could lead to catastrophic failure. In short, identifying our priorities and executing them in our daily workflow is the key to success in any walk of life. And when it comes to vulnerability management, it’s no different.
Identifying our priorities and executing them in our daily workflow is the key to success in any walk of life
Not a day goes by when we don’t hear about a new breach affecting another major corporation. In fact it has become so common these days that we aren’t far from the day when it would be newsworthy to have no breaches. IBM even mocked this concept in their latest ad. And when that eventual breach does happen, the usual scapegoats (admins/CISOs/CIOs) get rounded up by the media, pundits and anyone who wants to publicly humiliate these people—who in most cases are just trying to do the best job they possibly can do.
Assigning blame to scapegoats and embarrassing them is easy. I routinely hear comments such as “oh, these guys were so lame they had default accounts all over the place” or “we could break into the network with a year old code execution flaw.” One thing that rarely gets mentioned is maybe—just maybe—the security teams were overwhelmed with the data that came out of all the sensors they bought, or the security team was short staffed and couldn't possibly deal with the avalanche of data that was reported.
How you patch, what you patch and how you prioritize the use of your resources is very important
To give you an example, if you assume a typical 5,000 host Nessus® scan, and a conservative hit rate of 0.0025% for approximately 90k Nessus plugins, you still end up with a million results. And even if you patched 99.99% of those vulnerabilities, and missed just one really critical flaw, it could be game over. So how you patch, what you patch and how you prioritize the use of your resources is very important.
With the release of Nessus 6.5, we are adding several more filters to help you make those decisions, and to make them quickly. Our engineers brought this feature to life by curating vulnerabilities that we deemed to be critical.
Curated vulnerabilities
So what are curated vulnerabilities? These are the choicest of vulnerabilities, plucked from your organization’s garden, ripe for hackers to plunder.
Internally, we refer to this feature as #CaughtWithPantsDown. Why? Well, if your organization gets breached, is investigated post-breach and these vulnerabilities show up on your report, then you will be caught with your pants down—at least figuratively. There is just no excuse.
New criteria
So what are some of the new filters/criteria that you can use to prioritize your remediation workflow?
Exploited By Nessus
Frequently when Nessus is trying to verify a vulnerability, it will actively try to exploit the flaw and show the results in a report. For example, run a command such as ipconfig or id or grab the contents of /etc/passwd or boot.ini and display it in the plugin output. If Nessus can exploit it, then anyone with a free HomeFeed® Nessus subscription or above can, and most likely will, review the plugin source and take it to the next level. Therefore, such vulnerabilities should be patched immediately.
Default/ Known Accounts
This one is self-explanatory. There is no reason to have default or known accounts with default passwords on the network. They should either be disabled or updated with non-default passwords.
Malware/Suspicious IPs
Over the past few years Nessus has made major strides in the area of malware detection and reporting. For example, Nessus can tell if a scanned host is on a known botnet list, is communicating with a known botnet IP, is hosting malicious content associated with botnet propagation, has some malicious process running or even checks against some custom malware MD5 hash list. And if you get a hit for any of those plugins, you should take care of them right away.
In the News
For folks who work at Tenable or other security-focused companies, our world revolves around vulnerabilities and compliance. But that’s not the case if you are, say, an oil company. Given today’s oil prices, whether your organization has patched CVE-2014-0160 or not is probably the least of your problems. The point I am trying to make is that keeping your network secure is not why you are in business, so it’s possible you might not be up on the latest vulnerabilities. That’s why we have a new filter called In the News. These are vulnerabilities that have received a lot of media coverage in the recent past. For example: Heartbleed, Shellshock, Conficker, etc. These should be patched right away.
Unsupported By Vendor
And finally we come to unsupported software.
I once heard a story about a customer who, for some reason, thought Windows 98 was a more secure OS than the modern OSs. And I was curious to find out why. It turns out that Nessus only reported one critical flaw for Windows 98 and hundreds for others. Can you blame him for thinking that Windows 98 was better?
Don’t get tricked into believing that a low severity count for unsupported software applications means that they are better in any way. They are sleepers waiting to be exploited, and should be eradicated from your network as soon as possible.
These are just some of the new filters we have added. You can combine them with existing filters such as Exploit Available, Severity, Vulnerability Publication Date etc. to come up with your own criteria for remediation prioritization.
Sample filter
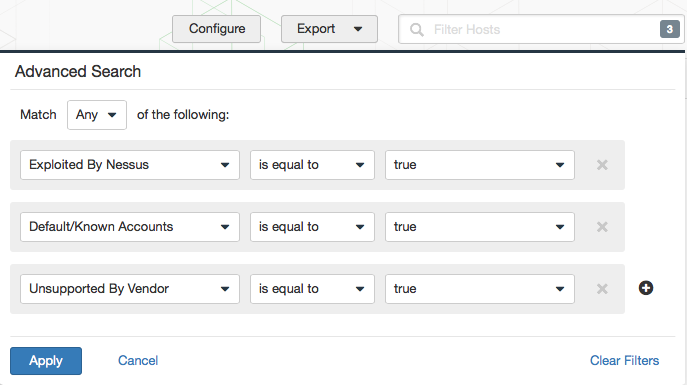
Post-scan action items and other use cases
With the addition of these new filters, it’s easy to create post scan action items to share with your internal security teams to lower risk and better prepare for an external pentest. All you have to do is apply the filter, and then click Export. The resulting report will be much smaller than your usual scan reports and is almost guaranteed to lower the risk to your organization since it’s most likely that 10 urgent items will be fixed quicker than 100 important ones.
With the addition of these new filters, it’s easy to create post scan action items to share with your internal security teams to lower risk and better prepare for an external pentest.
If you are consultant or a pentester who uses Nessus for vulnerability assessments, you can now share these reports in addition to the regular scan reports to provide extra value for your services.
Conclusion
Like most Nessus features, this feature arose from the sense of purpose we share at Tenable: if we care about something deeply enough and want to see it in our products, then there is a good chance that others would want to see it too.
This feature was also born out of Tenable’s recent Init15 hackathon. Not surprisingly, customers like you voted it as the winner, and now we are delivering on it.
Going forward, we will keep making refinements to this concept, but that shouldn’t stop you from using it right away—or should I say, keeping your pants up!
- Nessus
- Vulnerability Management
- Vulnerability Scanning
