Identifying the Weakest Links in Cyber Kill Chains®
In today’s security environment, with highly motivated cyber attackers employing increasingly sophisticated techniques to break through commonly deployed defenses, just one skillful intruder can infiltrate your systems with one carefully crafted attack path to a relatively unimportant asset. Last week on our blog, Marcus Ranum explained the “cyber kill chain®”1 framework, originally created by Lockheed Martin as a methodology for describing the process and exploitation of advanced persistent threats to information systems. Based on the military concept of a “kill chain,” the model details each step of a cybercriminal’s operation, from reconnaissance through delivery, to command and control and ultimately action. The idea is that by understanding the intruder’s intent and methodology, CISOs can intercept and disrupt the attacker at the earliest possible stage of intrusion, thwarting the attack before actual exploitation. If you can eliminate a link in the chain, the path is destroyed.
Attack paths
Attack paths – paths that intruders take to penetrate information systems over time to execute attacks on a target – are increasingly more complex. Think of attack paths like the classic traveling salesman problem. The salesman has to visit 10 cities in 4 days; what is the most efficient route to travel? Network security faces a similar challenge. What is the most efficient path that a cybercriminal may plot to infiltrate your systems?
Identify the weakest exploitable links and prioritize the critical vulnerabilities to be plugged, patched, and mitigated
For example, a typical multiple-hop attack path might involve a hack into a mail server that then accesses a client on the same network as the email server. Even though the client may not be active on the Internet, an intruder can follow an attack path/chain to access the vulnerable client.
The weakest link
If the goal of the cyber kill chain model is to disrupt or break the chain before major damage occurs, then the method is to divide and conquer: stop the intruder as early in the chain as possible to break his path of destruction. There are many tools in your security arsenal to combat attack chains. Front-line defenses include antivirus software, firewalls, patch management, logging, continuous network monitoring, file tampering monitoring, and configuration management. All of these tools are important, but what is the most effective point in the chain to break attack paths? Which vulnerability do you plug first to minimize attack path intrusions?
Scanning network systems for vulnerabilities is relatively easy to do when looking for one-hop attack vectors. Running regular or continuous scans on all assets will reveal weaknesses that are open to hacking. But when you start tracing multiple-hop paths or chains on a complex network configuration, ranking vulnerabilities and prioritizing fixes, the possible attack paths seem endless. Disrupting cyber kill chains is certainly more challenging but not daunting.
Three metrics for breaking kill chains
You can simplify the work of isolating and stopping kill chains by first prioritizing and tracking three critical metrics. These metrics identify the most vulnerable points in attack chains. Scan for these key metrics and you will address the most serious attack path vulnerabilities:
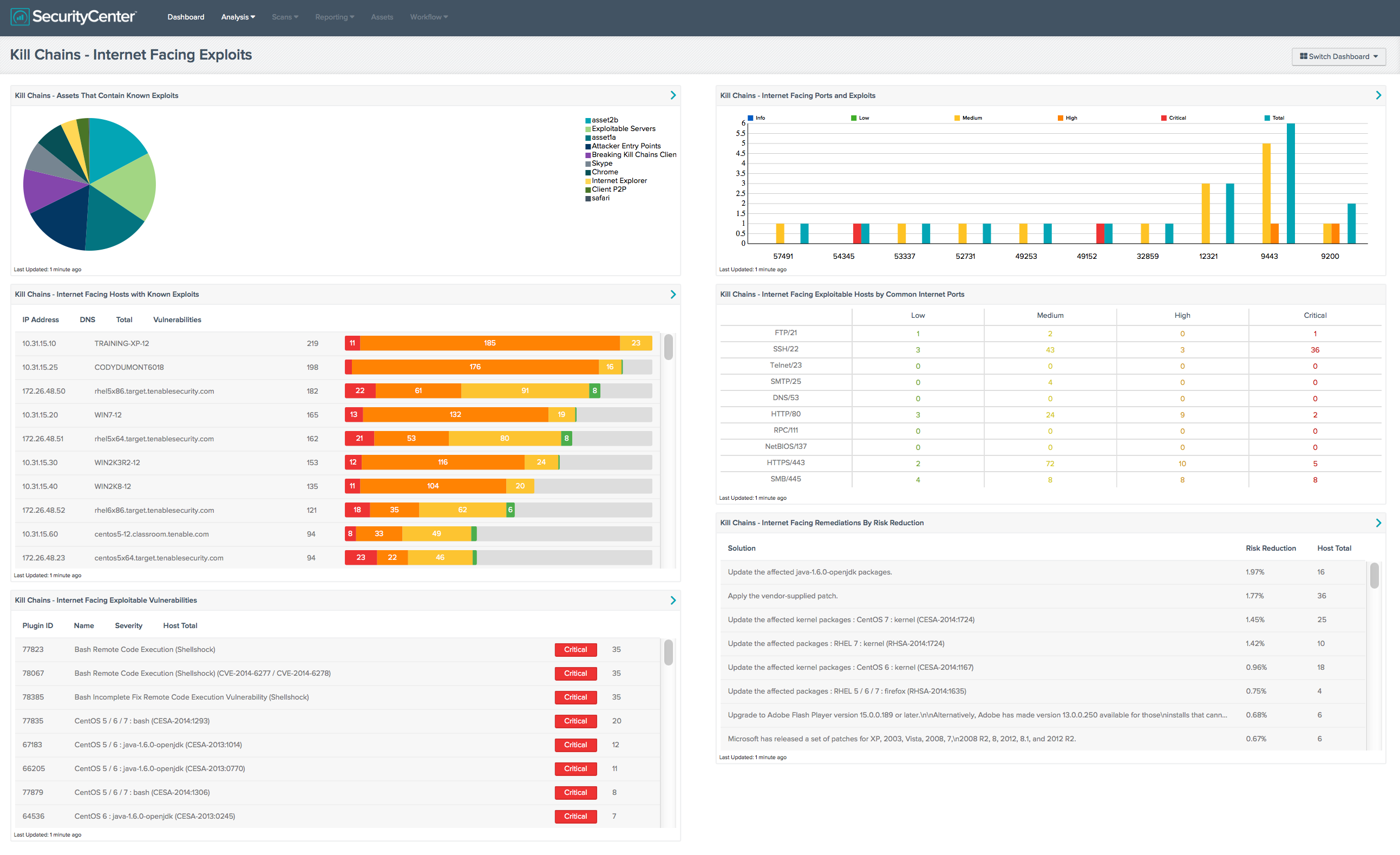
- The number of Internet facing computers/servers that are exploitable – Identify servers on the network perimeter, in the DMZ, or deployed deep in your network and Internet addressable. Audit for services that are exposed to the Internet via open ports where an attack path could jump into your internal network.
- The number of Internet browsing computers with exploitable clients – Identify all assets that connect externally to the Internet and the ports that are used. Identify specific client side applications such as Skype, Facebook, YouTube, etc. Alert on devices that browse the Internet with unsupported or outdated software.
- The number of internal trusted systems that have exploitable services – Detect clients that are trusted by specific servers or ports to identify the most important clients on your network. Then determine which of these trusted systems have exploitable security issues (e.g., publicly known exploits, critical vulnerabilities, outdated applications, unpatched clients, old antivirus software) and which connect to the Internet.
Focusing on these three metrics adds assurance to your security management plan by identifying points of vulnerability in your networks. These metrics do not reveal actual attack chains; they isolate single hop vectors that may be used in combination to form deadly kill chains. Armed with this data, you can identify the weakest exploitable links and prioritize the critical vulnerabilities to be plugged, patched, and mitigated. Breaking just one link in a chain kills the attack.
Tenable tools and resources
A good scanner such as Tenable’s Nessus can discover and gather data on systems that share common properties (such as Internet browsing) via credentialed audits. Tenable’s SecurityCenter Continuous View can be leveraged to follow up on the assets discovered by Nessus, classify the vulnerabilities, filter data from Nessus, report and alert on the weakest points, and correlate log and event data for analyzing potential attack paths. The Tenable paper on Predicting Attack Paths provides details on using Nessus and SecurityCenter Continuous View Attack Paths Dashboard to identify, prioritize, and mitigate attack chain weaknesses. You can also use several new SecurityCenter dashboards to monitor these three metrics.
See Breaking Kill Chains Dashboards and Breaking Kill Chains How To Guide for complete implementation details.
Kill chains can be defeated link by link. By identifying and repairing the weakest link in a potential chain, you can stop intruders in their tracks.
1 CYBER KILL CHAIN is a registered trademark of Lockheed Martin Corporation.
Related Articles
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning