CIS Critical Security Controls
Simplify CIS Critical Security Controls Implementation
The CIS Controls for Effective Cyber Defense (CSC) is a set of information security control recommendations developed by the Center for Internet Security (CIS).
CSC consists of best practices compiled from a variety of sectors, including power, defense, transportation, finance and more. Many organizations – especially those with multinational operations – utilize CSC to protect their network by focusing on the top security controls – those that provide the best protection against the most dangerous threats.
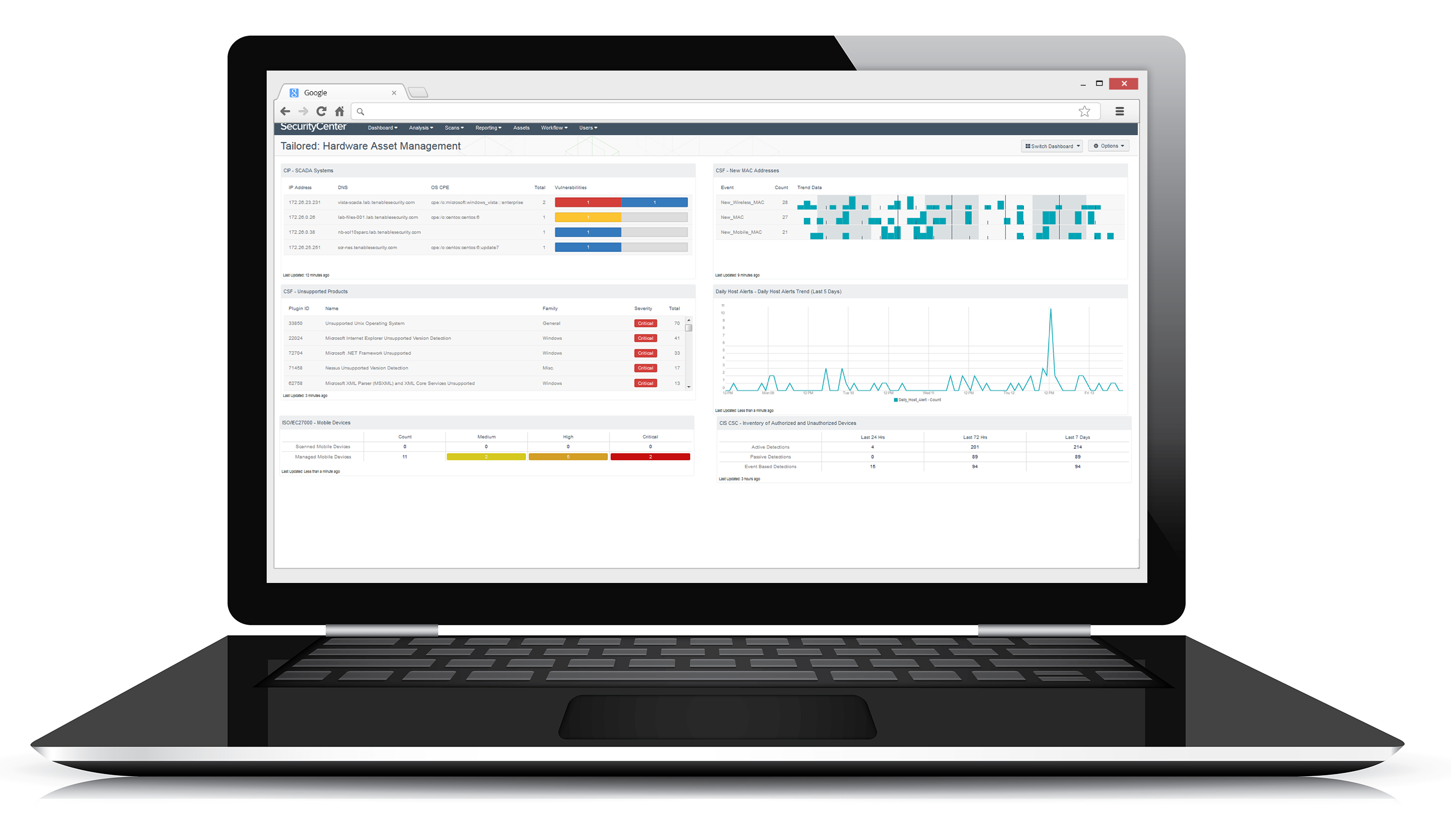
Tenable Security Center provides an automated approach to implementing and monitoring the CIS Critical Security Controls. It delivers continuous monitoring and out-of-the-box reports, dashboards and the industry’s only Assurance Report Cards® (ARCs) to help you address CSC’s five critical tenets: offense informs defense, prioritization, metrics, continuous diagnostics and mitigation, and automation.
Get the Solution Story
Security Frameworks & Tenable
Learn how Tenable Security Center automates and continuously monitors technical controls.
Advanced Security With Tenable
Tenable Security Center collects data from multiple sensors to provide advanced analysis of vulnerability, threat, network traffic and event information and deliver a continuous view of IT security across your environment. It gives you the information you need to continuously adapt and improve your security posture to protect your organization.
Broadest Coverage
Supports most technical controls prescribed in the NIST CSF, ISO/IEC 27002 and CIS CSC frameworks, and builds them into an automated control foundation for managing risk and securing the business.
Continuous Visibility
Use active scanning combined with continuous listening to obtain a complete view of control conformance across your environment.
Analyze Third-Party Security Products
Audit configurations of many third-party products and analyze events generated by them to identify control weaknesses.
Dynamic Asset Grouping
Focus dashboards to display a complete security and compliance view for services in your industrial control system and IT networks, including physical and virtual infrastructure, cloud and mobile environments.
Measure, Visualize and Communicate Adherence to Controls
Easily measure, visualize and understand your technical control conformance status by using dashboard templates, and identify gaps between where you are and where you want to be.
Map Technical Control Status to Business Objectives
Use Tenable Security Center Assurance Report Cards to compare your current security status to the desired status and help you build a roadmap for demonstrating a defensible security program.
Learn More

Introduction to the CIS Critical Security Controls
- Tenable Security Center