by Cesar Navas
February 16, 2016
Administrators and analysts routinely use SSH for remote administration within an organization. SSH server versions in an organization may not be the same, or may be outdated which creates potential vulnerabilities. This dashboard can assist analysts in identifying SSH servers and versions within an organization to assist in efforts to secure and harden the environment.
Secure Shell (SSH) provides a secure, command line interface for remote administration of UNIX based systems. Most UNIX based systems come with SSH installed by default when the system was built. Some organizations are using systems with SSH that are outdated, and have vulnerabilities that could compromise network assets. Using Nessus credentialed scans, analysts can detect current and outdated versions of SSH on systems, and alert to any potential vulnerabilities that could increase risk for an organization.
This dashboard can assist analysts in identifying SSH server versions within the organization. Once analysts identify the different versions of SSH installed on hosts, they can update vulnerable SSH servers and clients. SSH based attacks are still used by attackers to circumvent defenses to gain entrance into a network and/or move laterally. Hosts that use SSH include network and storage devices, which attackers can exploit depending on the use of SSH in the environment.
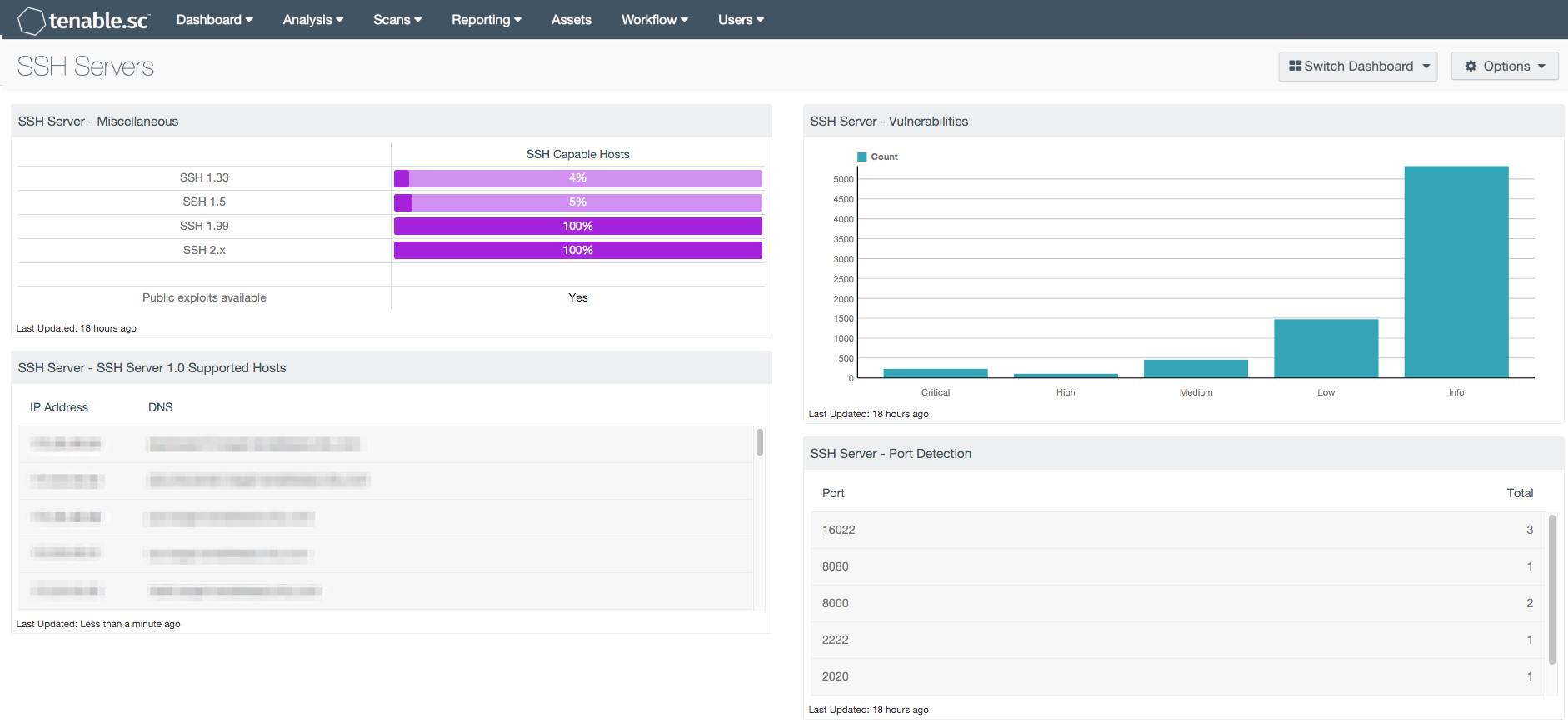
The components within this dashboard use several Nessus plugins that detect an SSH service in use, version, and vulnerabilities associated with SSH. This can help to identify systems that have outdated SSH versions such as 1.33 and 1.5, which typically have vulnerabilities associated with them. Detecting outdated versions of SSH can assist organizations in identifying hosts with exploitable vulnerabilities. Another component will help determine if SSH is installed, and the associated ports. Although most versions of SSH listen on TCP port 22, other versions can listen on non-standard ports such as port 16022.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.1
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk and ensure compliance. Our family of products includes Tenable.sc Continuous View (CV), Nessus, Nessus Network Monitor (NNM) and Log Correlation Engine (LCE). Tenable.sc CV provides the most comprehensive and integrated view of network health. Nessus is the global standard in detecting and assessing network data.
This dashboard contains the following components:
- SSH Server - Miscellaneous: This matrix component displays the count of different versions of SSH detected within the organization
- SSH Server - SSH Server 1.0 Supported Hosts: This table component displays the hosts detected in the organization supporting SSH protocol 1.x versions
- SSH Server - Vulnerabilities: This bar chart component displays counts of the vulnerability severities relating to TCP port 22
- SSH Server - Port Detection: This table component displays instances of network ports that are listening with the SSH protocol