by Cody Dumont
December 5, 2016
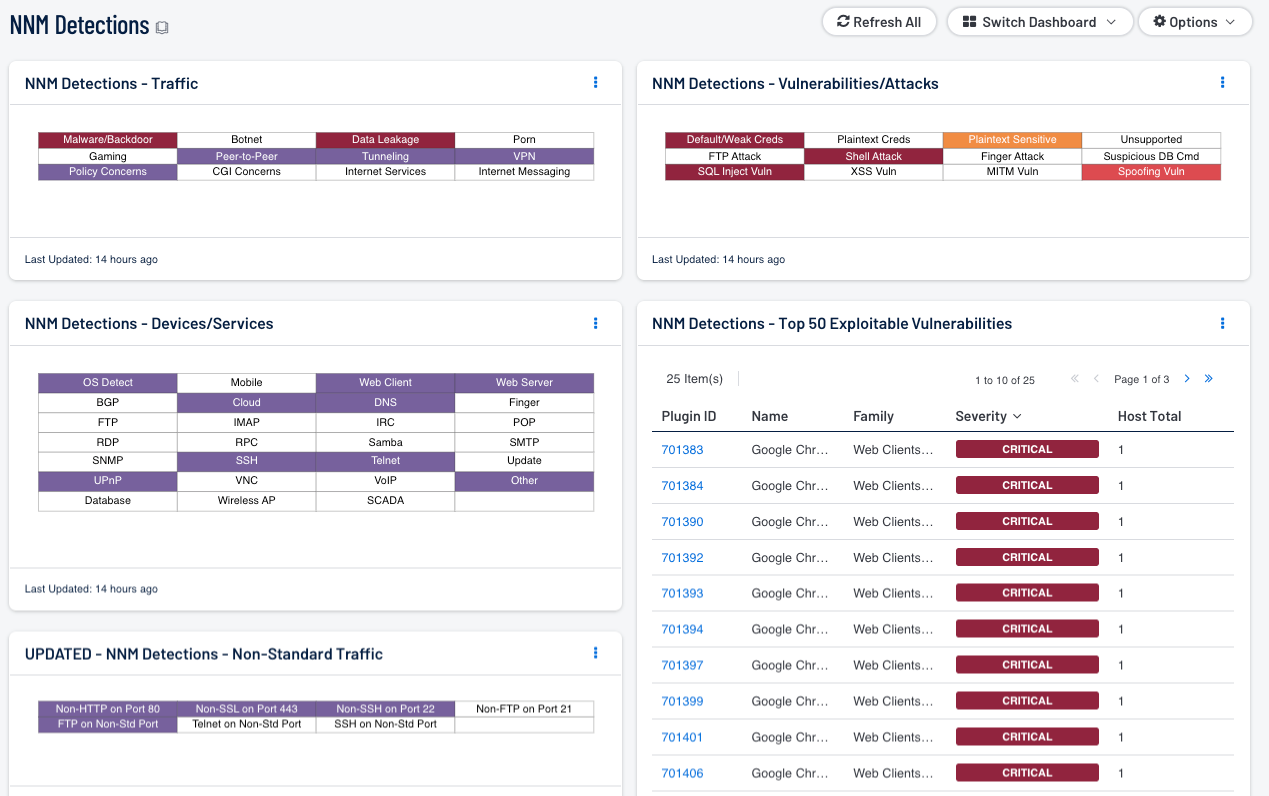
An organization collects vast amounts of log and event data on a daily basis, which must be sifted through in search of potential vulnerabilities. Given the size of the data, the passively detected vulnerability data can be difficult to manage. The NNM Detections Dashboard provides a complete look at passively detected vulnerabilities and events, which can allow an analyst to better manage and address vulnerabilities detected on the network.
With increasing mobile and transient network devices, analysts need to have a system in place that continuously monitors traffic, devices, and applications across environments. Using Nessus Network Monitor (NNM) enables powerful, yet non-disruptive, continuous monitoring of a network. Through continuous monitoring and deep packet analysis of an organization’s network traffic, NNM is able to detect potentially suspicious activity within the network. This information will provide organizations with actionable data by knowing what and when hosts come online.
The NNM Detections Dashboard presents organizations with an overview of vulnerabilities, events, and information detected by NNM in a clear and organized manner. The data presented in the dashboard represents areas of a network that are most prone to being exploited as well as indicators of suspicious network activity. The indicators are determined using various methods, such as filtering by passive plugin families, filtering by normalized events, and filtering by keywords in the plugin output text. By forming the indicators using these methods, the indicators can alert an analyst to a wide range of potential security threats.
In addition to highlighting network vulnerabilities, the indicators promote awareness and a clearer understanding of the network traffic. Through analysis of the network traffic, an analyst can more closely monitor the communication between devices for any anomalies and better identify suspicious activity. Using this information the analyst can more effectively discover and prevent potentially malicious activities within the network.
The dashboard and its components are available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Security Center Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- Security Center 5.4.1
- NNM 5.1.0
Through real-time, continuous monitoring, NNM performs automatic discovery of users, infrastructure, and vulnerabilities across more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. Tenable Security Center allows hosts to play a part in their own security hygiene, reporting on changes in their state and security posture. Using a unique combination of detection, reporting, and pattern recognition, Security Center is able to identify the biggest risks across an organization’s entire enterprise, enabling an organization to react to advanced threats, zero-day vulnerabilities, and new forms of regulatory compliance. Security Center allows for the most comprehensive and integrated view of network health.
The following components are included in this dashboard:
- NNM Detections - Traffic: This matrix presents indicators for network traffic detected by NNM.
- NNM Detections - Devices/Services: This matrix displays indicators for devices and services detected by NNM.
- NNM Detections - Non-Standard Traffic: This matrix displays indicators for non-standard traffic detected by NNM.
- NNM Detections - Vulnerabilities/Attacks: This matrix displays indicators for vulnerabilities and attacks detected by NNM.
- NNM Detections - Top 50 Exploitable Vulnerabilities: This table displays the top 50 exploitable vulnerabilities detected by NNM.