by Sharon Everson
December 8, 2017
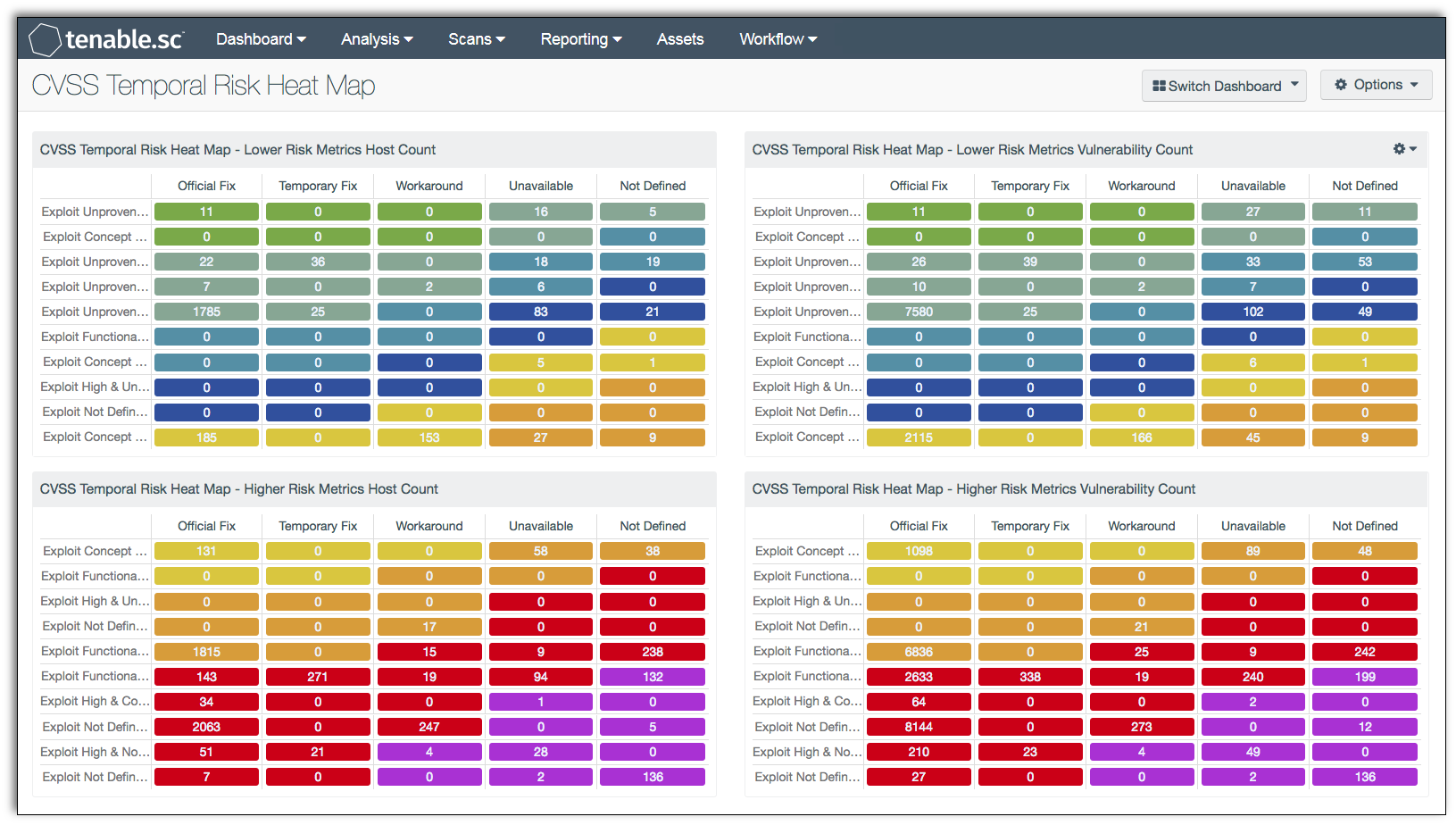
The use of Common Vulnerability Scoring System (CVSS) risk metrics is often considered best practice, but may be difficult to visualize and understand the risk analysis presented. The use of heat maps is common for a simplified visual representation of all types of risk. Information presented within this dashboard uses CVSS temporal metrics to display risk levels for systems and their respective vulnerabilities.
The CVSS provides a framework for assessing the risk of discovered vulnerabilities. CVSS is broken down into three metric types:
- Base
- Temporal
- Environmental
This report focuses on Temporal Metrics, which contain characteristics of a vulnerability that may evolve over the lifetime of the vulnerability. Each of the three Temporal metrics holds the following set of values:
- Exploitability (E) - The exploitability metric represents the current state of exploit techniques and availability of code. Exploitable code can increase the number of potential attackers, as well as the severity of the vulnerability. The exploitability metric has the following values:
- Unproven (U) - No exploit code is available, or an exploit is entirely theoretical.
- Proof-of- Concept (POC) - The code or technique is not functional in all situations and may require modification by an attacker.
- Functional (F) - The code works in most situations where the vulnerability exists.
- High (H) - The code works in every situation, or is actively being delivered via an autonomous agent (such as a worm or virus).
- Not Defined (ND) - Assigning this value to the metric does not influence the score and should be skipped.
Remediation Level (RL) - The remediation level of a vulnerability is an important factor in prioritizing remediation efforts. When a vulnerability is initially published, the vulnerability is often unpatched. During the life cycle of the vulnerability, the remediation level changes throughout the respective stages. A higher risk is in direct proportion to the degree that a fix is considered official and permanent. The remediation level metric has the following values:
- Official Fix (OF) - A complete vendor solution is available.
- Temporary Fix (TF) - There is an official but temporary fix available.
- Workaround (W) - There is an unofficial, non-vendor solution available.
- Unavailable (U) - No solution is available or is impossible to apply.
- Not Defined (ND) - Assigning this value to the metric not influence the score and should be skipped.
Report Confidence (RC) - Details may be limited when a vulnerability is first published. However, as a vulnerability is confirmed by other researchers or by the vendor, details may become more publicized. The urgency to mitigate is higher when more details or proofs of concept are publicized. Attackers can use this new information to exploit, therefore increasing the risk significantly to an organization as details become publicly available and validated by reputable sources. The report confidence metric has the following values:
- Unconfirmed (UC) - There is a single unconfirmed source or possibly multiple conflicting reports.
- Uncorroborated (UR) - There are multiple non-official sources, possibly including independent security companies or research organizations.
- Confirmed (C) - The vulnerability has been acknowledged by the vendor or author of the affected technology.
- Not Defined (ND) - Assigning this value to the metric does not influence the score and should be skipped.
The "Not Defined" metric is included in the heat map as many vulnerabilities have this designation. As a general security concern, Tenable.sc CV™ does not remove data in a risk assessment. However, if an organization does not use this metric, then an analyst can delete the bottom row. The indicators in this chart vary in color according to severity for quick and easy reference. The indicator color starts with white on green (signifying the least risk) and progressing to white on purple with the highest risk level.
This report provides security analysts and managers a quick visual reference of the organizations overall temporal risk. Further detailed information on the vulnerabilities discovered can be obtained by drilling down through each cell block referenced. As temporal metrics evolve over time and mitigation efforts are completed, this information updates to reflect those changes.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the Security Industry Trends category.
The dashboard requirements are:
- Tenable.sc 5.5.2
- Nessus 8.6.0
- LCE 6.0.0
- NNM 5.9.0
Tenable's Tenable.sc Continuous View® (Tenable.sc CV™) provides continuous network monitoring, vulnerability identification and security monitoring. Tenable.sc CV™ is continuously updated with information about advanced threats, zero-day vulnerabilities and new types of regulatory compliance configuration audit files. Tenable constantly analyzes information from unique sensors, delivering continuous visibility and critical context, and enabling decisive action that transforms a security program from reactive to proactive. Active scanning periodically examines the applications on the systems, the running processes and services, web applications and configuration settings. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Tenable.sc CV™ provides an organization with the most comprehensive view of the network and actionable information to support mitigation efforts and reduce cyber risk. Analysts can quickly assess the level of temporal risk with Tenable.sc CV™. Tenable enables powerful, yet non-disruptive, continuous monitoring that will provide organizations with the information needed to reduce risk within the enterprise.