Tenable
Cloud Security
The actionable cloud security platform
Reduce risk by rapidly exposing and closing priority security gaps caused by misconfigurations, risky entitlements and vulnerabilities–in one powerful cloud native application protection platform (CNAPP).

Eradicate your exposures with visibility across multi-cloud environments
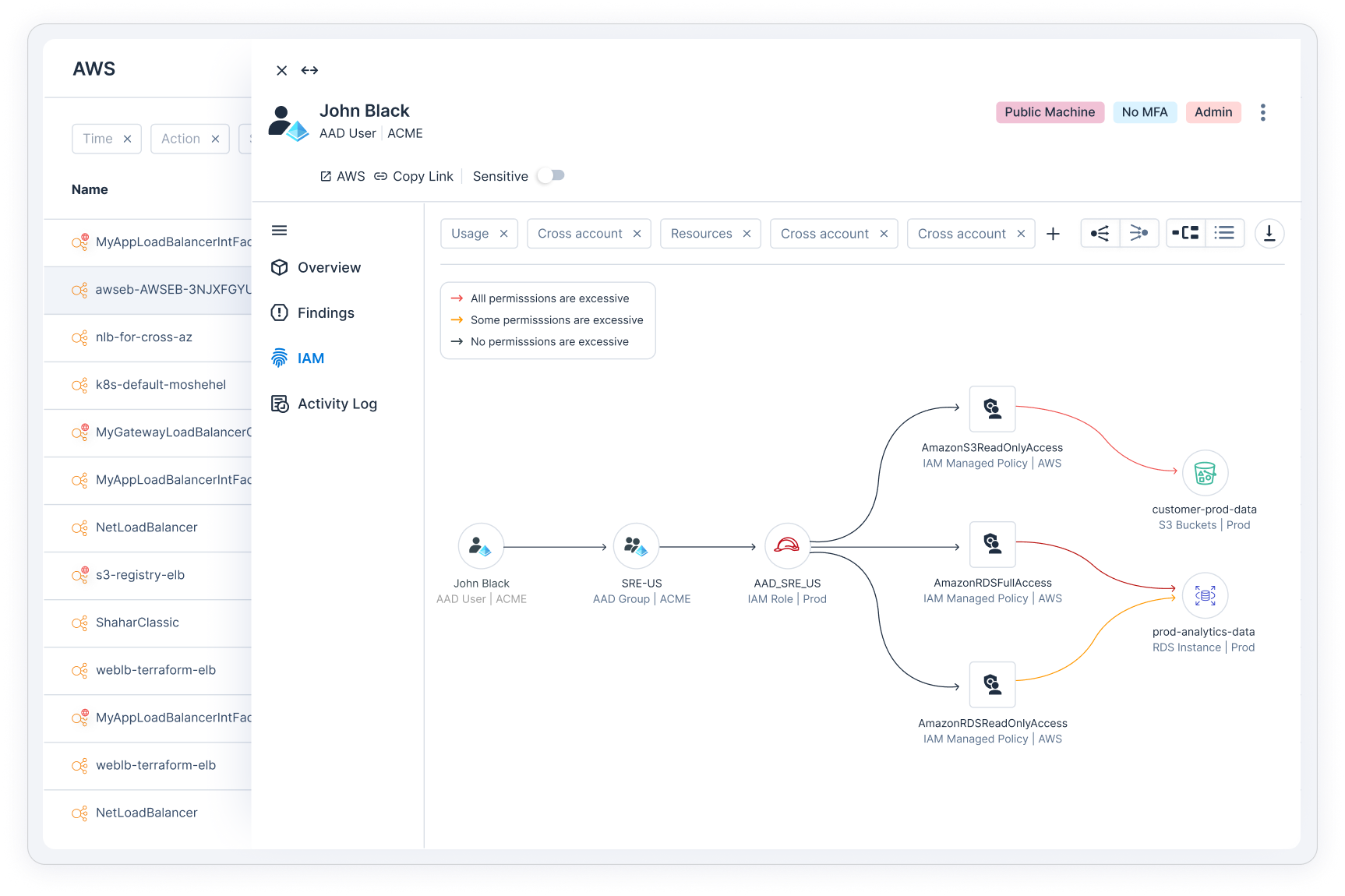
Know your cloud resources
Discover the compute, identity and data resources in your cloud and get contextualized visibility into how critical resources are accessed.
Expose critical cloud risks
Gain the context you need to focus on the priority risks caused by the toxic combination of misconfigurations, excessive entitlements, vulnerabilities and sensitive data.
Close cloud exposures
Reduce cloud risk by closing priority exposures with top speed and surgical precision–even if you only have five minutes to spare.
Deploy the unified Tenable CNAPP at scale
CNAPP solutions replace a patchwork of siloed products that often cause more problems than they solve, such as multiple false positives and excessive alerts. Those products usually provide only partial coverage and often create overhead and friction with the products they’re supposed to work with. Most importantly, CNAPPs allow businesses to monitor the health of cloud native applications as a whole rather than individually monitoring cloud infrastructure and application security.
CWP
Vulnerability management across all running cloud workloads
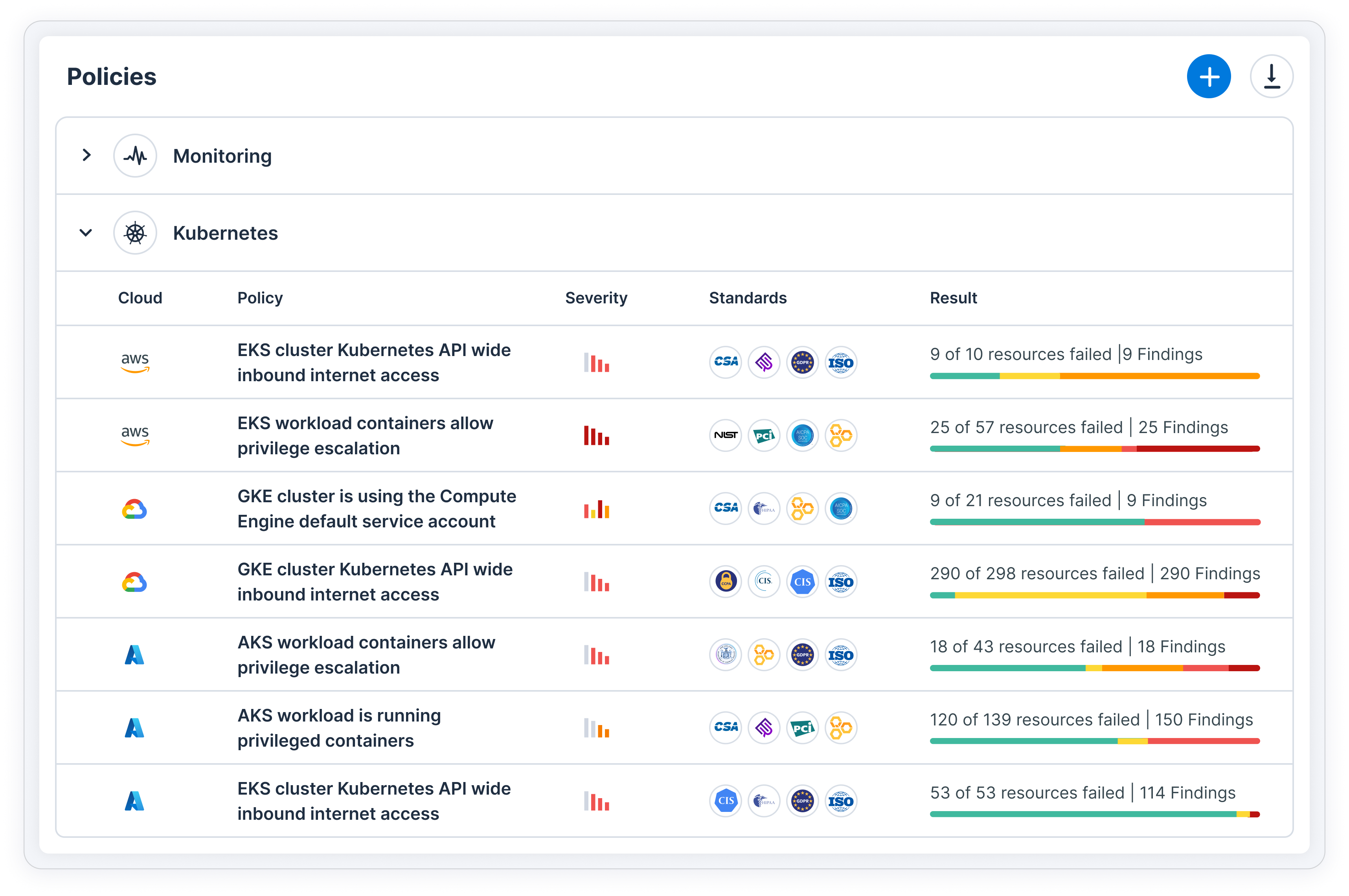
CSPM
Compliance and governance for the full cloud stack
CIEM
Least-privilege access and zero trust
DSPM
Discovery and classification of data and risk prioritization
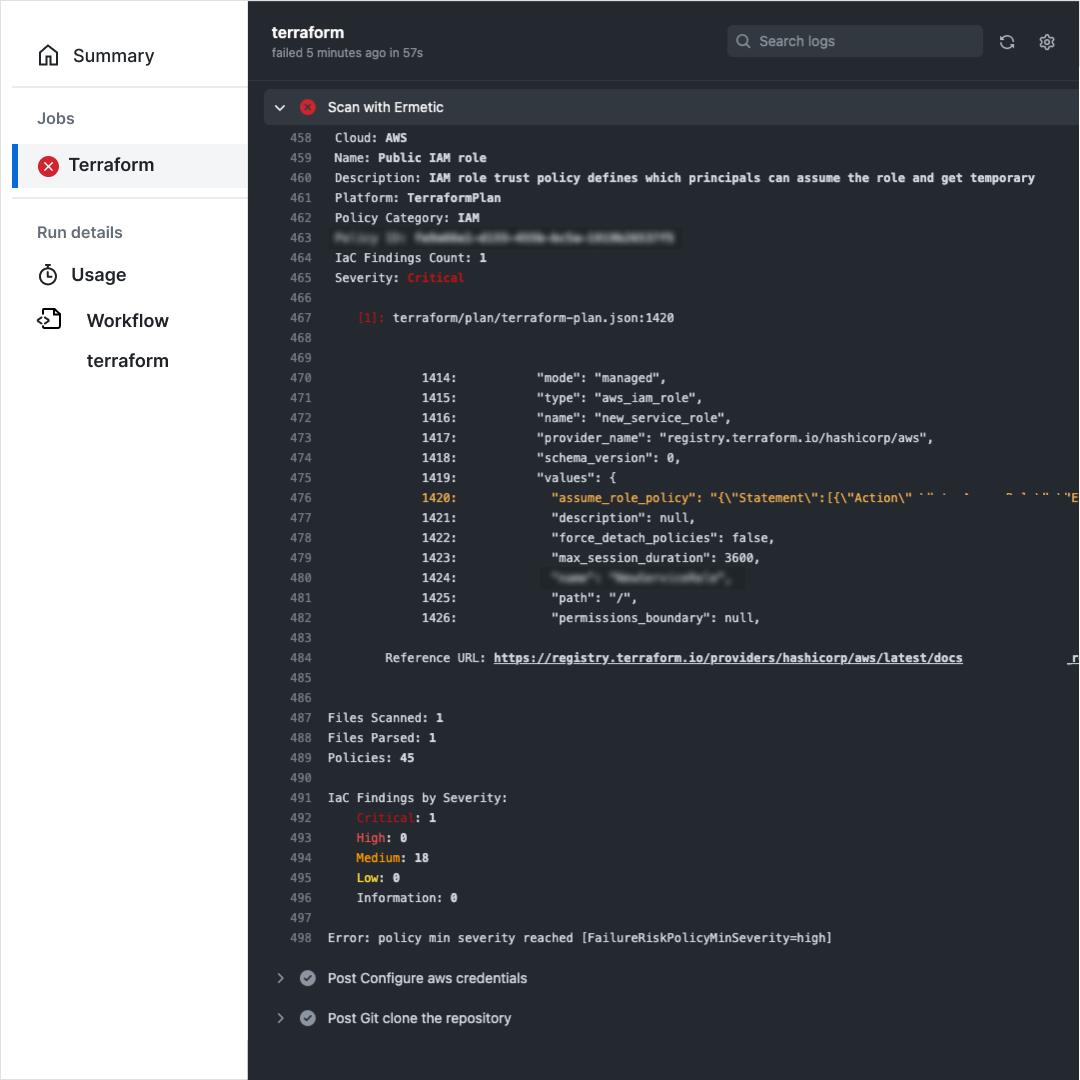
IAC
Infrastructure as Code security and DevOps workflow support
AI-SPM
Visibility and security for AI workloads, services and data used in training and inference
CDR
Service and host activity analysis
KSPM
Container security and compliance in the cloud and on-prem
Secure your entire cloud stack
From development to runtime, Tenable Cloud Security continuously analyzes your cloud resources to find the most important risks, spot unknown threats and toxic combinations of security issues and deliver actionable insights within minutes.
Read white paperFind misconfigurations, ensure compliance
CSPM monitors risk by continuously assessing settings and configurations in cloud environments. Discover risks and deviations from security standards and policies so you can stay compliant in multi-cloud environments.
Learn moreProtect identities and right-size access to cloud resources
Our industry-leading CIEM gives you control over access entitlements so you can eradicate exposures caused by human and service identities in your cloud and achieve least-privilege access to cloud resources and data at scale.
Read moreSafeguard critical operations
Tenable Cloud Security protects cloud workloads by continuously scanning, detecting and visualizing your most critical risks across VMs, containers and serverless functions, including vulnerabilities, sensitive data, malware and misconfigurations.
Read moreSimplify Kubernetes Security
Tenable Cloud Security reveals, prioritizes and remediates security gaps while automating compliance for Kubernetes clusters in your cloud. With unified visibility into configurations, you’ll be able to fix misconfigurations.
Learn moreProactively reduce runtime alert noise
Embed security in DevOps tooling workflows, including HashiCorp Terraform and AWS CloudFormation, so you can scan, detect and fix misconfigurations in your native Infrastructure as Code environment.
Learn moreDetect and respond to threats
Tenable Cloud Security examines enriched cloud provider logs to give you context around each risk, enabling your SecOps teams to rapidly investigate and remediate cloud threats.
Learn moreGrant just-in-time access
Avoid long-standing access privileges to cloud resources and reduce your cloud attack surface. You can assign temporarily elevated access while enforcing fine-grained least privilege policies, while minimizing risks.
Learn moreEnsure cloud data security
Use data security posture management (DSPM) to understand the types and location of sensitive data that exist in your cloud, including PII, PHI and company secrets. Understand the risks to this data, including excessive access. Then better prioritize your most critical cloud risks.
Learn moreProtect AI workloads, services and data
Identify and classify sensitive AI training data, e.g., company secrets and personally identifiable information (PII), across multi-cloud environments, and reduce the risk of misuse or exposure. Secure AI training data by protecting resource configurations with built-in AI configuration policies.
Learn more
Available through Tenable One: The world’s only AI-powered exposure management platform
Tenable One solves the central challenge of modern security: a deeply divided approach to seeing and doing battle against cyber risk. We remove risk by unifying security visibility, insight and action across the attack surface to rapidly expose and close gaps. Customers use Tenable One to eradicate priority cyber weaknesses and protect against attacks—from IT infrastructure to cloud environments to critical infrastructure and everywhere in between.
Learn more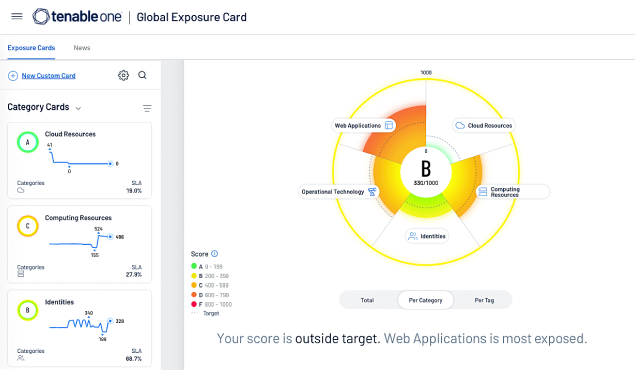
FAQs
- What is Tenable Cloud Security?
-
Tenable Cloud Security is a fully integrated cloud infrastructure security solution, combining powerful cloud security posture management (CSPM) and cloud security workload protection (CWP) capabilities, with best-in-class cloud infrastructure entitlement management (CIEM), cloud detection and response (CDR) technologies, and highly innovative infrastructure-as-code (IaC) security and Kubernetes security posture management (KSPM) solutions. The cloud native application protection platform (CNAPP) manages your multi-cloud inventory, enforces preventive security policies across the stack (addressing identity, network, data and compute risks), detects and responds to live threats, shifts security left and automatically remediates risks via IaC, CI/CD, or runtime environments. This enables benchmarking against security standards, and drives compliance enforcement across organizations.
- How is Tenable Cloud Security priced and licensed?
-
Tenable Cloud Security includes all CNAPP components and can be purchased as a stand-alone product or as part of Tenable One. Stand-alone pricing is based upon the number of billable resources. Volume discounts are then applied based on the total forecasted monthly usage. Similarly, when priced as part of Tenable One, the base pricing is based on the number of total billable resources. The cloud resources are then priced using a ratio in Tenable One and then volume discounts are applied using the total assets subscribed under the existing Tenable One licensing. Just-in-time (JIT) access is licensed separately and can be added to either the standalone offering or offering priced as part of Tenable One. Contact a Tenable representative for tailored pricing information and questions.
- Where can I find documentation and release notes on Tenable Cloud Security?
-
Technical documentation for Tenable products is at https://docs.tenable.com. You must log in to your Tenable Cloud Security account to view release notes and documentation. Contact a Tenable representative for access to technical documentation and release notes.
- What is the difference between Tenable Cloud Security and Tenable One?
-
Tenable Cloud Security can be purchased as a standalone product or as part of the Tenable One Exposure Management Platform. When combined with Tenable One, Tenable Cloud Security provides a comprehensive view of your entire IT environment, encompassing traditional networks, on-premises servers, operational technology, and public clouds. By purchasing Tenable Cloud Security as part of Tenable One, organizations can consolidate their Tenable purchases into a single contract and access additional features, such as exposure views.
- What clouds and cloud native tooling does Tenable Cloud Security integrate with?
-
Tenable Cloud Security integrates with all major cloud providers (AWS, Azure, GCP) in addition to a number of cloud provider services such as AWS Control Tower and Entra ID. Integrate Tenable Cloud Security with your ticketing, notification, and SIEM tools to support the creation of tickets and the sending of push notifications and utilize standard communication tools such as Jira, Slack, Microsoft Teams and email integration tools to scale the tool within your organization.
- What identity providers does Tenable Cloud Security support?
-
Tenable Cloud Security integrates with numerous IdPs including Entra ID, Google Workspace, Okta, OneLogin and Ping Identity. These IdP integrations reveal a complete inventory of federated users and groups associated with your cloud accounts and provide permission analysis and identity intelligence.
- How does Tenable Cloud Security protect my data?
-
Tenable ensures the safety of your workloads, employing robust encryption and access controls to safeguard sensitive data. It reins in excessive permissions and granting of long-standing access. Tenable protects your sensitive data by reducing the blast radius in the event of a breach. For more information on how Tenable Cloud Security ensures data protection and privacy of your unique cloud environment, please contact your Tenable representative.
- Can I use Tenable Cloud Security without involving third parties?
-
Yes. Tenable Cloud Security users can purchase in-account scanning as an add-on for their environment. This functionality supports onsite scanning of workloads for organizations beholden to narrow data privacy standards and regulations. In-account scanning is performed in your cloud account, and the data never leaves the environment.
- How can I purchase Tenable Cloud Security?
-
To purchase Tenable Cloud Security you can work with your local certified partner or contact your Tenable representative. Click here to request a demo of Tenable Cloud Security.
Related resources
Learn more about Tenable Cloud Security
Using [Tenable Cloud Security] automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish.
- Tenable Cloud Security
 AWS
AWS Azure
Azure Google Cloud
Google Cloud