Auditing Microsoft Office Configurations Using Nessus
Hardening Microsoft Office
Microsoft® Office® is ubiquitous in today’s work environment. MS Office applications offer many security configuration options that can reduce the likelihood of exploitation. However, the default configuration settings typically don’t provide a strong security posture. The requirements and recommendations documented in common regulations and security guides are a great start to securing your Office installations. Tenable customers can also measure and evaluate the security of their Microsoft Office Suite environment using Nessus® and Tenable SecurityCenter™ audit compliance policy files.
Securing Microsoft Office Templates
Users can download Microsoft Office templates from the web, some of which may introduce vulnerabilities. For instance, there are vulnerabilities in Microsoft Active Template Library (ATL) Active X controls for Office that could allow for remote code execution if a user loaded a specific malicious template. For more information on this vulnerability, please review MS09-060.
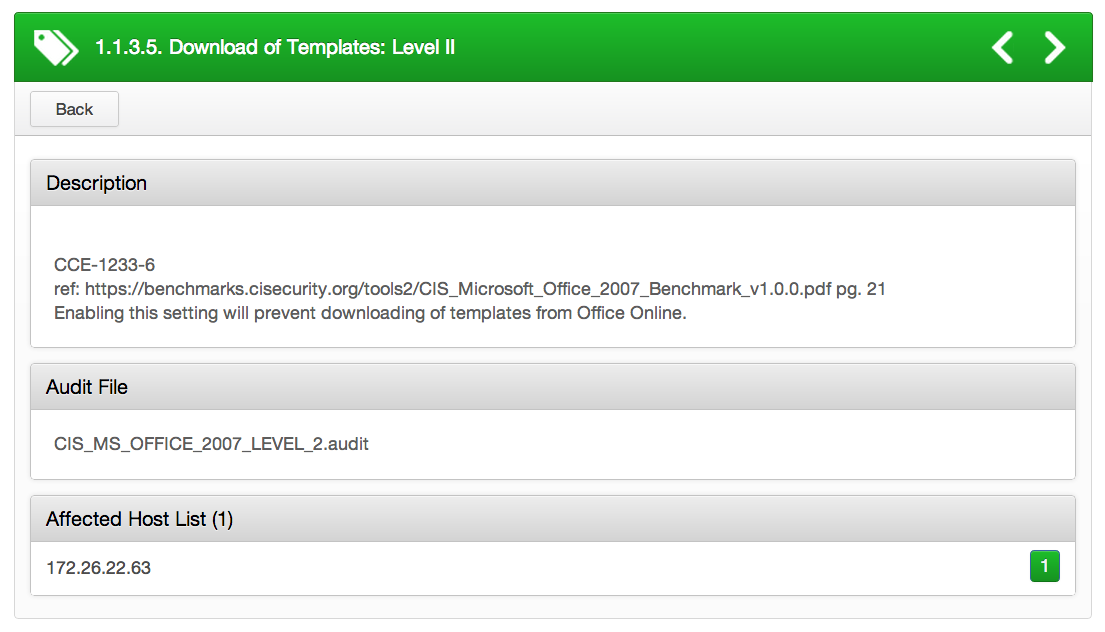
This is a common misconfiguration in the application’s default settings. Configuring "Disable template downloads" in the Microsoft Office Group Policy template setting prevents users from downloading Office templates. By using Nessus compliance auditing, customers can validate this setting if configured correctly:
<custom_item>
type : REGISTRY_SETTING
description : "1.1.3.5. Download of Templates: Level II"
value_type : POLICY_DWORD
reg_key : "HKU\Software\Policies\Microsoft\Office\12.0\Common\Internet"
reg_item : "DisableTemplateDownload"
value_data : 1
reg_ignore_hku_users : "S-1-5-18,S-1-5-19,S-1-5-20"
reg_option : CAN_NOT_BE_NULL
info : "CCE-1233-6"
info : "ref:https://benchmarks.cisecurity.org/tools2/CIS_Microsoft_Office_2007_Benchmark_v1.0.0.pdf pg. 21"
info : "Enabling this setting will prevent downloading of templates from Office Online."
</custom_item>
Require Signed Application Add-ins
Add-ins can enhance a user’s productivity by adding various types of new or updated features to Microsoft Office applications, such as Word® or Excel®. However, it’s possible that a malicious person may use unsigned add-ins to gain code execution on a user’s machine. For instance, vulnerabilities could allow for remote code execution in the case of opening a specially-crafted Office file in the same network directory of a library file. The attacker could gain the same user rights as the logged-on user if exploited correctly (see MS11-073).
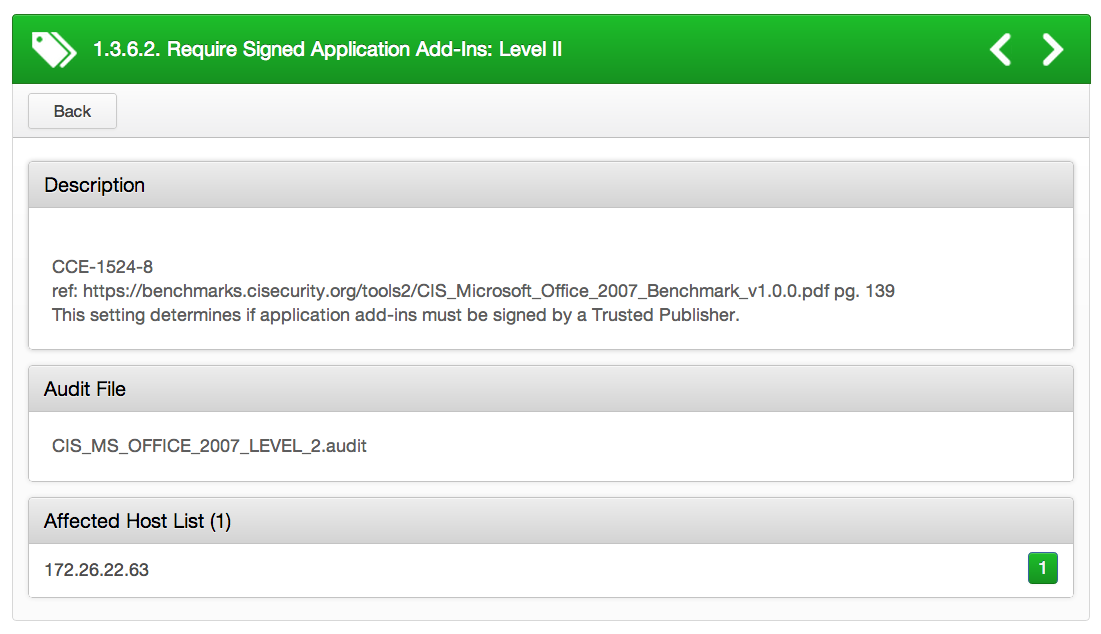
By configuring the "Require that application add-ins are signed by Trusted Publisher" setting, it forces all executed add-ins to be signed by a Trusted Publisher. See the following .audit check as an example:
<custom_item>
type : REGISTRY_SETTING
description : "1.3.6.2. Require Signed Application Add-Ins: Level II"
value_type : POLICY_DWORD
reg_key : "HKU\Software\Policies\Microsoft\Office\12.0\Excel\Security"
reg_item : "RequireAddinSig"
value_data : 1
reg_ignore_hku_users : "S-1-5-18,S-1-5-19,S-1-5-20"
reg_option : CAN_NOT_BE_NULL
info : "CCE-1524-8"
info : "ref:https://benchmarks.cisecurity.org/tools2/CIS_Microsoft_Office_2007_Benchmark_v1.0.0.pdfpg. 139"
info : "This setting determines if application add-ins must be signed by a Trusted Publisher."
</custom_item>
Block Opening of Converters
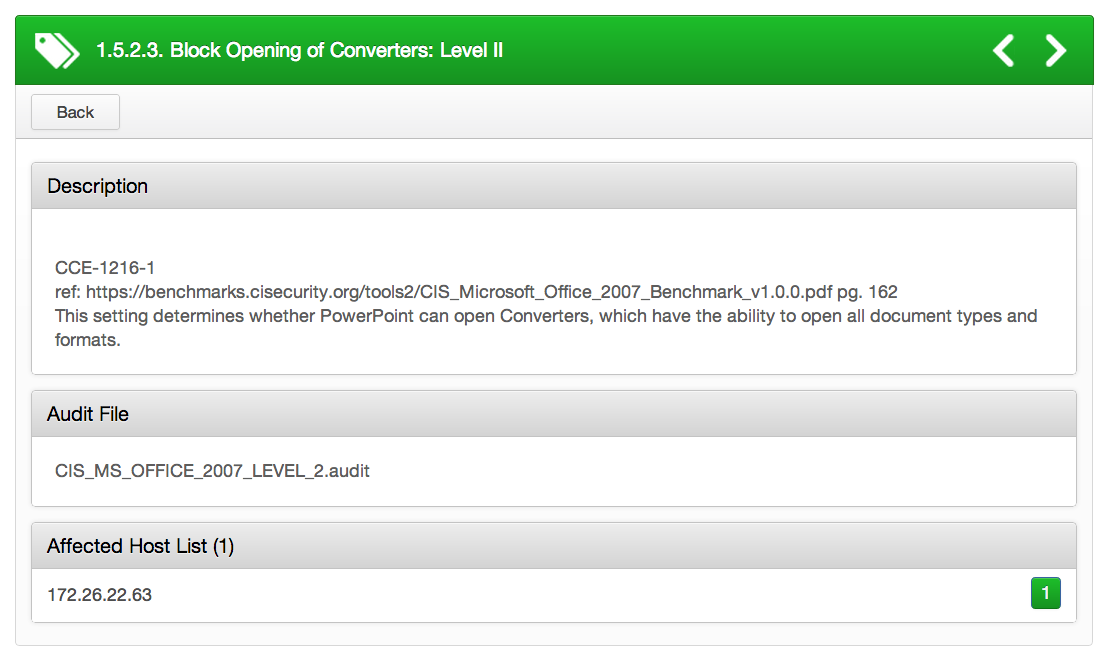
By default, Microsoft Office applications have built-in text converters that enhance a user’s productivity by converting non-Microsoft Office documents into documents that can be read by the Office application. However, this may pose a security risk if the file the user is trying to open is malicious. For instance, the vulnerability could allow remote code execution if a specific file is opened in Office. An attacker who successfully exploits this vulnerability could gain the same privileges as the currently logged-on user. Configuring the “Block opening of converters” setting to ‘enable’ will prevent users from opening foreign documents and formats. See the following .audit check as an example:
<custom_item>
type : REGISTRY_SETTING
description : "1.5.2.3. Block Opening of Converters: Level II"
value_type : POLICY_DWORD
reg_key : "HKU\Software\Policies\Microsoft\Office\12.0\PowerPoint\Security\FileOpenBlock"
reg_item : "Converters"
value_data : 1
reg_ignore_hku_users : "S-1-5-18,S-1-5-19,S-1-5-20"
reg_option : CAN_NOT_BE_NULL
info : "CCE-1216-1"
info : "ref:https://benchmarks.cisecurity.org/tools2/CIS_Microsoft_Office_2007_Benchmark_v1.0.0.pdfpg. 162"
info : "This setting determines whether PowerPoint can open Converters, which have the ability to open all document types and formats."
</custom_item>
Securing Web Access
While web-access and connectivity features built into Office, such as InfoPath solutions, can offer users a wealth of services, malicious InfoPath solutions on the Internet can lure users into inadvertently leaking sensitive data. Vulnerabilities have been reported within Outlook Web Access (OWA) that could allow an attacker to gain access to an individual OWA client’s session data.
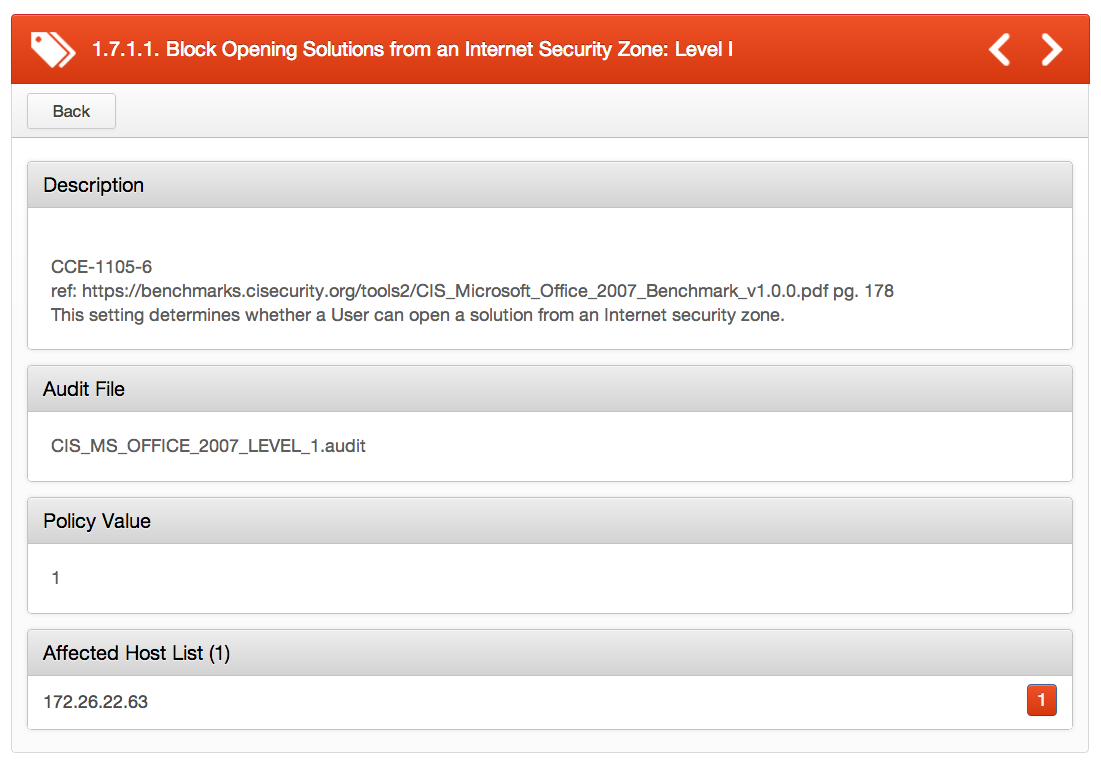
Configuring the “Disable opening of solutions from the Internet security zone” setting to ‘enable’ will prevent users from opening solutions from an Internet security zone.
Please see the following .audit check as an example:
<custom_item>
type : REGISTRY_SETTING
description : "1.7.1.1. Block Opening Solutions from an Internet Security Zone: Level I"
value_type : POLICY_DWORD
reg_key : "HKU\Software\Policies\Microsoft\Office\12.0\InfoPath\Security"
reg_item : "AllowInternetSolutions"
value_data : 1
reg_ignore_hku_users : "S-1-5-18,S-1-5-19,S-1-5-20"
reg_option : CAN_NOT_BE_NULL
info : "CCE-1105-6"
info : "ref:https://benchmarks.cisecurity.org/tools2/CIS_Microsoft_Office_2007_Benchmark_v1.0.0.pdfpg. 178"
info : "This setting determines whether a User can open a solution from an Internet security zone."
</custom_item>
Conclusion
In all, there are 1300+ individual checks spanning several .audit files for Microsoft Office. Audit compliance policies are available for CIS Microsoft Office 2007 Level 1 & 2, DISA STIG Microsoft Office 2010, and MSCM Microsoft Office 2010. Tenable audit compliance policies for Microsoft Office products can be downloaded by logging into the Tenable Support Portal.
*Originally written by Joshua Turpin, Tenable Compliance Auditor
Related Articles
- Nessus








