Cloud Security Posture Management (CSPM)
Prioritize cloud misconfigurations with identity-driven insights
A single misconfiguration or mismanagement of your cloud services could result in fines and lawsuits that might cost your organization hundreds of millions of dollars. Get iron-clad cloud identity security to accurately detect, prioritize and remediate your greatest configuration and permissions risks.
Request a demo
What is Cloud Security Posture Management (CSPM)?
CSPM is a market segment for IT security tools designed to identify misconfiguration issues and compliance risks in the cloud. A CSPM tool validates security policies that define a desired cloud state and ensures they are executed in production. It checks policies against multi-cloud environments, so you can view and prioritize discovered misconfigurations, report on compliance status and remediate found risks.
Get CSPM integrated into a single, holistic cloud security solution
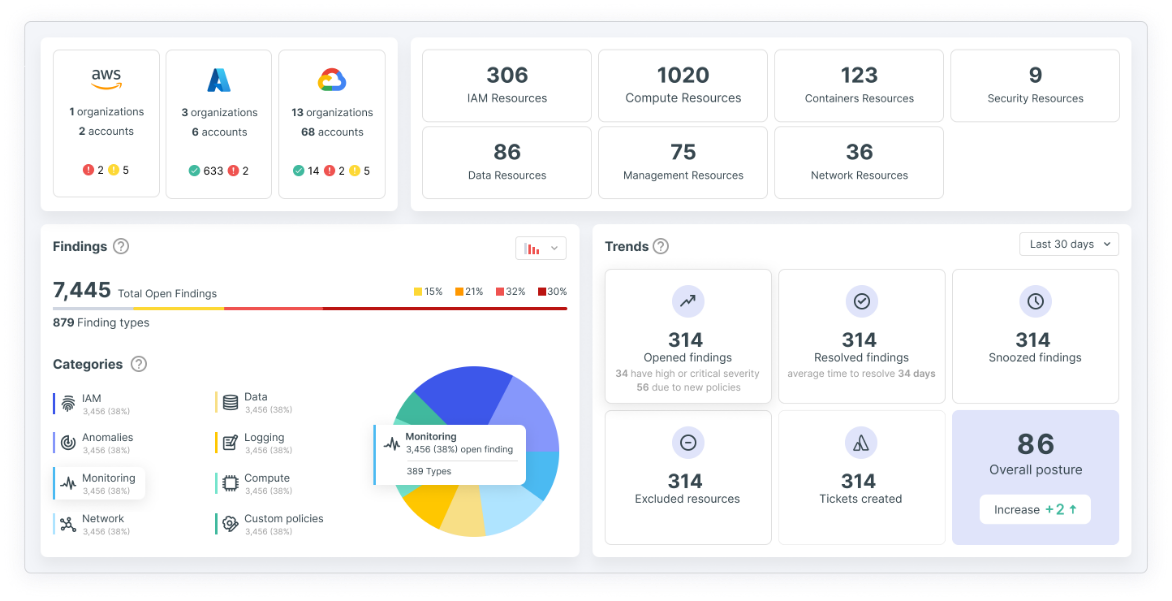
With Tenable Cloud Security, you get more than alerts that simply point to risk. You get actionable and easy-to-understand findings that help you make decisions quickly. You can even automate your response or choose guided remediation. No more wasting time on manual analysis or sorting through siloed alerts from multiple tools. Tenable enables you to set precise policies that address risk and compliance and create organizational-wide least privilege to reduce exposure.
Reduce cloud infrastructure misconfigurations and risks
You can be compliant but not secure. Even one small, misconfigured setting can expose sensitive assets to bad actors. To avoid attacks, you must remove risk and enforce security best practices, including least privilege — but manually doing so at scale is nearly impossible.
Tenable helps by automatically checking your cloud configurations, security settings and compliance against common frameworks, regulatory requirements and enterprise policies to determine where you have excessive risk. This minimizes alert noise and helps you accurately prioritize risk, proactively manage non-compliance and auto-remediate faulty configurations, violations and risks, including identity-based ones.

"Security audits in the cloud are no trivial matter. By enabling us to jump through audit hoops, Ermetic [now Tenable Cloud Security] proved itself a capable technology and time saver."
Etienne SmithCTO, Kikapay
Achieve cloud compliance with continuous scanning and 1-click reporting
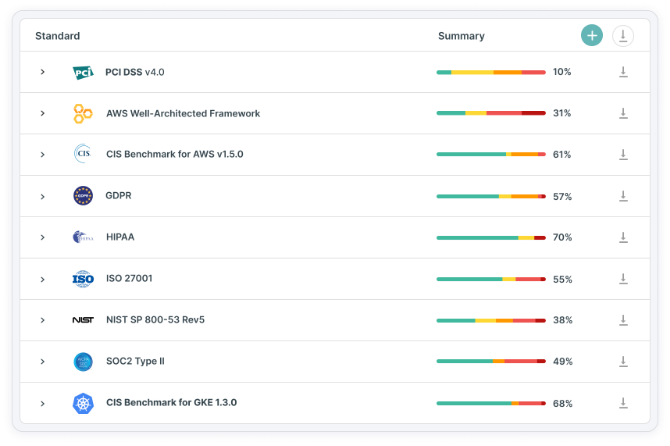
Tenable Cloud Security simplifies cloud compliance. You get a single solution for continuous configuration and resource scanning across multiple cloud environments — to prevent violations and ensure adherence to security policies.
With Tenable, you can audit multi-cloud environments against industry standards such as CIS, AWS Well Architected, GDPR, HIPAA, ISO, NIST, PCI-DSS, SOC2, CIS for Kubernetes and create custom checks. Tenable also quickly generates in-depth reports for internal compliance, external audits and daily security operations (asset inventory, misconfigurations, network configurations, etc.) so you can reduce manual effort and save time.
Automate security and compliance for K8S environments
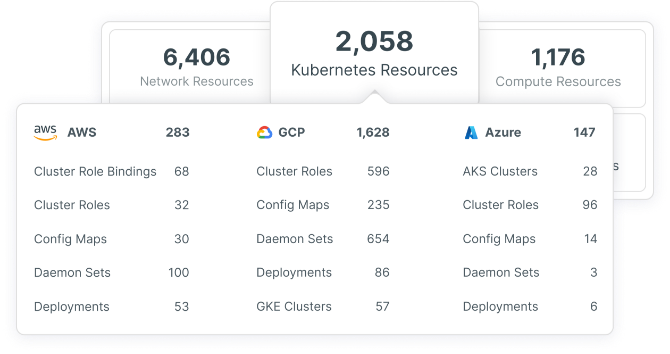
As part of Tenable Cloud Security, you also get a powerful Kubernetes Security Posture Management (KSPM) solution that scans Kubernetes — on-prem or in the public cloud. Gain full, contextual visibility into Kubernetes resources, including nodes, namespaces, deployments, servers and service accounts. You can also control and secure new resources created in a Kubernetes cluster with a built-in and customizable Kubernetes admission controller.
Get comprehensive cloud security with tenable's unified CNAPP
Tenable offers a comprehensive cloud-native application protection platform for AWS, Azure and GCP as Tenable Cloud Security. With market-leading cloud infrastructure entitlement management (CIEM) at the core, it dramatically reduces your cloud attack surface and enforces least privilege at scale.
"Using Tenable Cloud Security automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish."
Larry VivianoDirector of Information Security, IntelyCare
Learn more about Tenable Cloud Security
Using [Tenable Cloud Security] automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish.
- Tenable Cloud Security