Fortify your security posture with Tenable OT Security
Vulnerability Management. Scan your IT, OT, and IoT assets for 79,000+ vulnerabilities. Detect cyber threats, malicious insiders, and more.
OT Scanning. Maximize your operational environment’s visibility, security, and control for SCADA systems, PLCs, DCS, IED, HMIs, and other assets across IT, OT, and IoT.
Reporting and Risk Intelligence. Access proven security tools and reporting capabilities for IT and OT teams, providing unmatched visibility into converged IT/OT segments and industrial networks in a single pane of glass.
Request a demo
Get the Operational Technology Security You
Need.
Reduce the Risk You Don't.
Vulnerability Management. Scan your IT, OT, and IoT assets for 79,000+ vulnerabilities. Detect cyber threats, malicious insiders, and more.
OT Scanning. Maximize your operational environment’s visibility, security, and control for SCADA systems, PLCs, DCS, IED, HMIs, and other assets across IT, OT, and IoT.
Reporting and Risk Intelligence. Access proven security tools and reporting capabilities for IT and OT teams, providing unmatched visibility into converged IT/OT segments and industrial networks in a single pane of glass.
Tenable protects over 44,000 clients and 65% of the Fortune 500

$10M+
Cost of downtime in ONE day as it relates to factories shutting down.
<5%
Of OT professionals said they were confident in their company's ability to secure IIoT devices and systems.
Why choose Tenable OT Security?
Access market-leading OT vulnerability management capabilities,
purpose-built to help
secure your operations

Get complete visibility across your entire attack surface
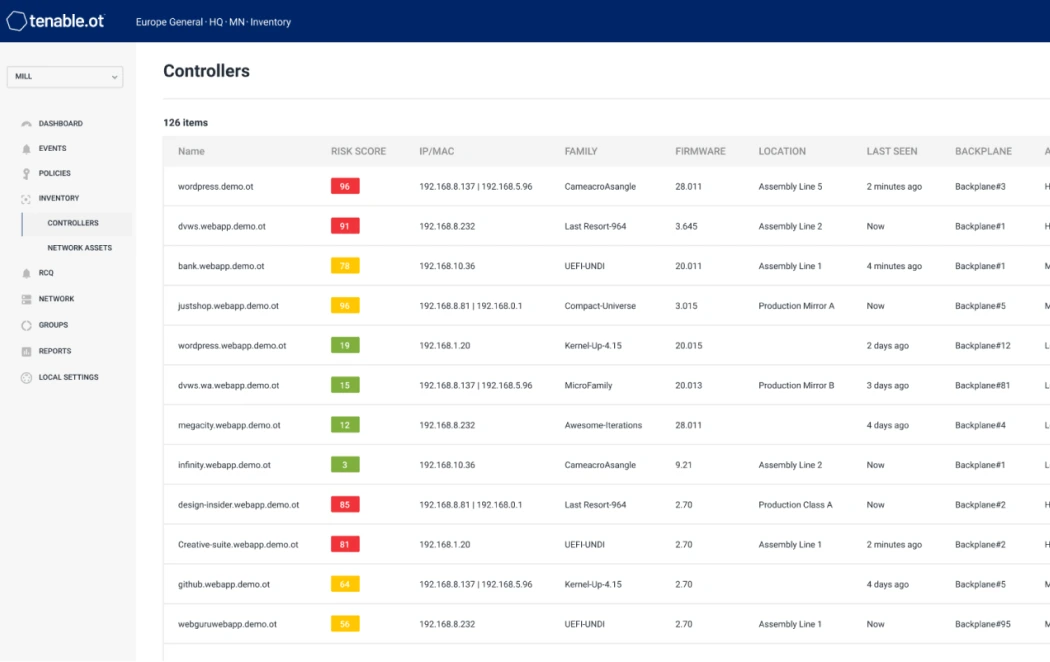

Automation
Ecosystem integration
Tenable OT Security integrates with leading Access Control Systems, SIEM, SOAR, next generation firewalls and diode based firewalls in order to provide insights to personnel outside of OT specific titles. Tenable OT Security also works in cooperation with the larger Tenable product portfolio including Tenable Security Center, Tenable Vulnerability Management and Tenable Identity Exposure.


Tenable OT Security also works in cooperation with the broader Tenable One portfolio, including Tenable Security Center, Tenable Vulnerability Management, and Tenable Identity Exposure.
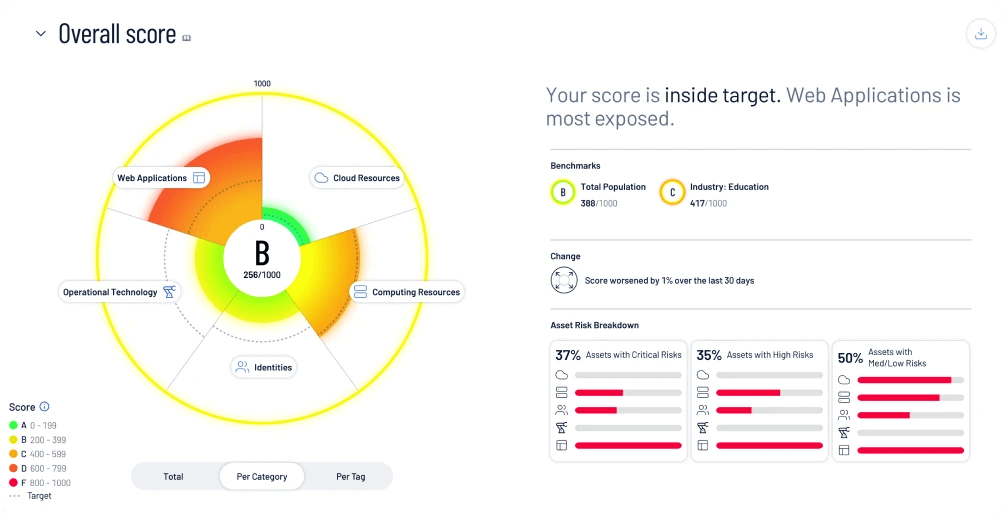
Key features







