by Cesar Navas
June 20, 2016
As the number of data breaches continues to increase, many organizations still rely on removable devices to conduct business. Many security teams focus their efforts on detecting attacks, preventing malicious code, and hardening their infrastructure, but do not account for monitoring and securing removable devices. The ISO/IEC27000 Removable Media dashboard can assist the organization in monitoring network endpoints for removable device activity, which can aid in ensuring that critical data remains secure.
The ISO/IEC 27002:2013 framework is a global security standard that provides best practice solutions in support of the controls found in Annex A of ISO/IEC 27001:2013. The framework establishes guidelines and general principles for initiating, implementing, maintaining, and improving Information Security Management Systems (ISMS). Each security control and objective provided within the standard can be tailored to specific business and regulatory objectives, and assist with maintaining overall compliance. This dashboard focuses on the ISO/IEC 27002 8.3.1 control, which can help an organization to detect, manage, and secure removable media devices on a network.
Many data breaches are the result of insiders utilizing unsecured and unmonitored removable devices to copy data in and out of a network. Uncontrolled use of devices such as mobile phones, tablets, digital camera, and USB Drives can lead to data theft of both corporate and customer data. In addition, some users may have the ability to transfer personal data on to corporate devices, which can introduce malware, exploit existing vulnerabilities, or install unauthorized software. By using Tenable.sc Continuous View (CV), organizations have an accurate assessment of removable devices being plugged into the network. Nessus can provide real-time information on specific removable devices, mapped drives, and removable device history. This will allow security teams to assess the effectiveness of current security controls in place, highlight existing security gaps, and identify unauthorized devices in use.
The audit checks for removable media can be performed with several audit files. Listed below are some examples of files supporting CD-ROM and USB checks. The organization should review the audit files and create a specific audit file that applies directly its policies.
- financial_microsoft_windows_os_audit_guideline_v2.audit
- USGCB_Win7_Desktops_v2_official.audit
- PCI_2.0_Redhat.audit
- VMware_vSphere_5.x_Hardening_Guide.audit
This dashboard will provide security teams with information on detected removable devices, mapped drives of removable storage devices, and history of USB devices on Windows systems. Mapped drives will determine when a particular USB devices was used, and by whom. Having a history of previously connected USB devices can provide a point of origin for unauthorized devices or malware infections. Audit checks on removable media such as CD-ROM’s, floppies, and other removable storage are also included. A trend chart of Windows USB device events are obtained from the Log Correlation Engine (LCE), that will detect both attached and USB removal events. Continuous monitoring alone will not provide accurate protection. Organizations should look to enforce security policies that restrict or limit the use of removable devices without completely compromising business continuity.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- LCE 6.0.0
- Content Audit Files
- Audit Files with Checks for USB, CDROM, and other types of media
Organizations should also monitor Cloud and Peer-To-Peer activity, which can assist in identifying and reducing the chance of data leakage. The Data Leakage Monitoring dashboard will provide security teams with targeted information from devices on services with potential data leakage events, which can provide insight into users that are uploading sensitive corporate data into the cloud.
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform. Tenable’s Log Correlation Engine (LCE) performs automatic discovery of users, infrastructure, and vulnerabilities across more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Using Tenable.sc CV, the organization will obtain the most comprehensive and integrated view of its network devices and assets.
This dashboard contains the following components:
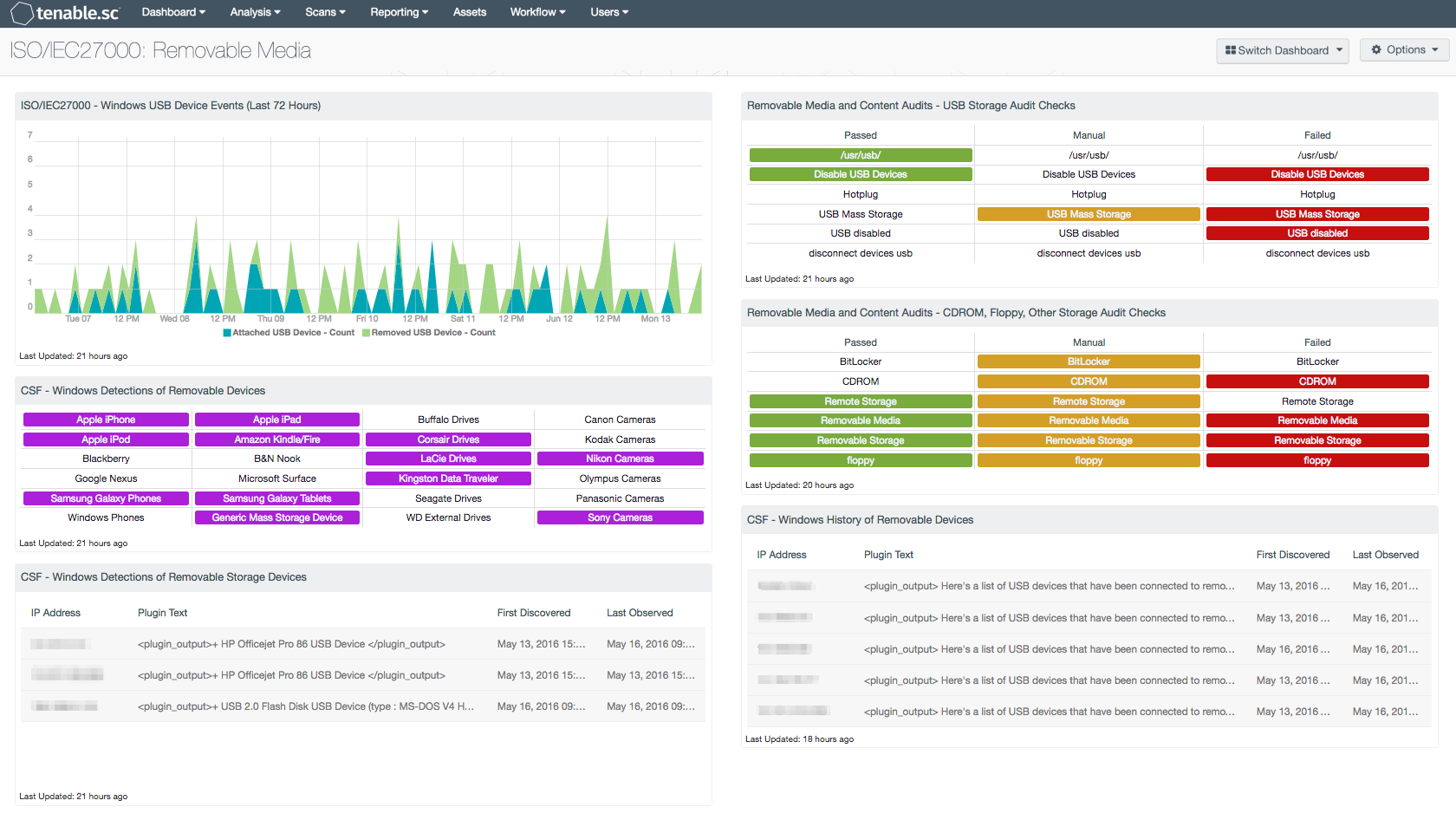
- ISO/IEC27000 - Windows USB Device Events (Last 72 Hours): This component presents trend data of USB Device events on Windows system within the last 72 hours. The Log Correlation Engine (LCE) keeps track of USB attached and removal events for each IP address. Analysts can use this information to identify unauthorized USB devices on a network.
- CSF - Windows Detections of Removable Devices: This component presents a list of connected removable devices on Windows hosts. Information such as IP Addresses, vendor, device type, and drive letter are all included within this table. Additional details such as when the device was first discovered and last observed are also presented. The analyst can utilize this information in detecting unauthorized devices on a network.
- CSF - Windows Detections of Removable Storage Devices: This component presents a list of Windows detections of removable storage devices. The matrix utilizes the Windows Portable Devices plugin, which detects portable devices based on their Vendor ID, Device ID, or by Windows registry string. Some of the more popular portable devices are displayed within this matrix, however the analyst can modify this list as needed. An indicator will turn purple when a specific portable device has been detected. The analyst can click on the indicator, and drill down to obtain additional information on hosts that the removable device has been detected on.
- Removable Media and Content Audits - USB Storage Audit Checks: This component focuses on compliance data, filtering on several strings containing 'USB' in the plugin name. When an audit file is imported into Tenable.sc, the 'description' line for the check becomes the plugin name. The description for each check provides a descriptive statement of the audit check. There are several audit files that contain checks for USB storage devices; the most common strings were compiled and used in this component.
- Removable Media and Content Audits - CDROM, Floppy, Other Storage Audit Checks: This component focuses on compliance data, filtering on strings containing CDROM, floppy, and other removable storage devices in the plugin name. When an audit file is imported into Tenable.sc the 'description' line for the check becomes the plugin name. The description for each check provides a descriptive statement of the audit check. There are several audit files that contain checks for CDROM, floppy, and other removable storage devices; the most common strings were compiled and used in this component.
- CSF - Windows History of Removable Devices: This table presents a list of detected USB devices that have been connected to a Windows host at least once in the past. This component can provide a point of origin for unauthorized devices, malware infections, and possible data leakage events. Information on IP Addresses, vendor, device type, and drive letter are all included. Additional details such as when the device was first discovered and last observed are also presented. The data provided within this component can assist organizations with discovering and tracking data leakage, and can aid in refining security policies.