by Cesar Navas
July 9, 2020
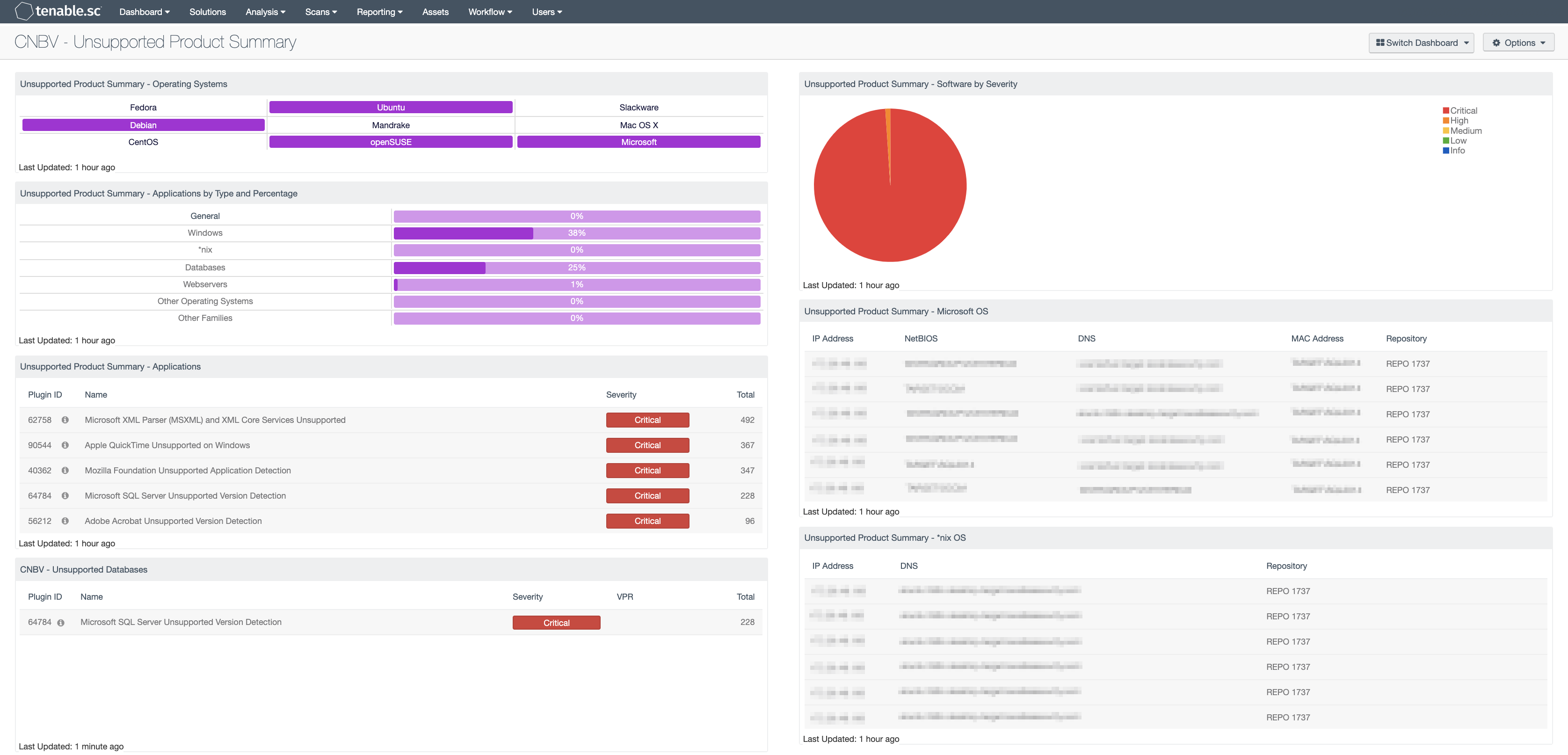
The National Banking and Securities Commission (CNBV) Annex 72 is a collection of Key Risk Indicators (KRI) that establish compliance standards for financial institutions operating in Mexico. Financial institutions in Mexico should be prepared to divulge cyber risk KRIs to CNBV when requested. The KRIs relating to obsolete or outdated system versions are grouped by asset function, for example the servers, workstation, network devices, and other asset types. Within each of these asset categories, there are KRI’s that require only supported and maintained software is allowed to be installed on systems. This dashboard relates to the following KRIs: KRI0008, KRI0018, KRI0024, KRI0026, and KRI0027.
The proliferation of unsupported and end-of-life products is common security problem experienced across all institutions. The risk managers work closing with IT Managers to minimize risk using managed software deployment systems. As applications and operating systems reach their end-of-life (EOL), vendors stop offering support. Therefore, security and stability decrease, raising concern as time progresses. Patches, updates and security fixes will no longer be available, so identifying systems running EOL applications is an important part of assessing and minimizing organizational risk. In compliance with CNBV’s Annex 72, Financial institutions are required to keep track of whether infrastructural equipment (KRI0008), workstations (KRI0018), servers (KRI0024), databases (KRI0026), and applications (KRI0028) are out of date.
Tenable.sc uses active and passive detection methods to identify unsupported (end-of-life) products found in the environment. Passive detection methods include monitoring for user-agent string, service banners, and other clues in network communications that indicate the software installed on the asset. Active detection methods use a more exact discovery by looking in the Microsoft registry, common software installations locations, or using applications utilities such as YUM or APT in Linux systems. Using all of the available methods the risk manager is able to verify the operation team’s activities and identity areas for risk mitigation.
This dashboard is available in the Tenable.sc feed, which is a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc feed under the Executive category. The dashboard requirements are as follows:
- Tenable.sc 5.14.1
- Nessus 8.10.1
This dashboard provides the organization with a clear and simplified method to identify and establish compliance according to Annex 72 by CNBV. The data can be Analyzed to provide more detail in non-compliant areas, which facilitates the Fix and Measuring steps to the Cyber Exposure Lifecycle. Tenable.sc is the On-prem solution for understanding the picture of the network, while keeping the data under the organization’s control. Built on leading Nessus technology, Tenable.sc discovers unknown assets and vulnerabilities, and monitors unexpected network changes before they turn into breaches.
Components
Unsupported Product Summary - Operating Systems: This indicator matrix reports on operating systems that are no longer supported. The matrix displays popular operating systems but is easily modified to fit organizational requirements. Plugin ID #33850, with vulnerability text filters that filter for the appropriate operating system name in the plugin output, alert on Unix-based operating systems that are no longer supported. Keyword filters, along with a CPE string for Microsoft, is used to alert on end-of-life Microsoft operating systems by turning the indicator purple when a vulnerable asset is present.
Unsupported Product Summary - Software by Severity: This pie chart presents a graphical representation based on severity, unsupported applications and operating systems found in the environment.
Unsupported Product Summary - Applications by Type and Percentage: This matrix displays the percentage of unsupported applications and operating systems based on plugin family, such as database servers, web servers, Windows, or other operating systems. In this component, the base query uses the plugin family. The percentage is then calculated using the “Unsupported” keyword in the plugin name. The matrix helps illustrate the percentage of unsupported or end-of-life applications within the organization.
Unsupported Product Summary - Microsoft OS: This table displays all unsupported Microsoft operating systems. Displayed are the IP address, NetBIOS identifier, DNS name, MAC address, and repository of the offending device. This component identifies unsupported Microsoft operating systems by the "unsupported" filter against the plugin name. and the base CPE string to identify Microsoft operating systems via the IP Summary tool.
Unsupported Product Summary - Applications: The table displays unsupported applications by name and sorted by severity. Displayed is the plugin ID, application name, plugin family, severity, and the total host count found. This component utilizes the keyword “unsupported” in the plugin name field. Additionally the table filters based on severity, dropping any informational results, and presents them via the Vulnerability Summary tool.
Unsupported Product Summary - *nix OS: This table displays all unsupported Unix-based operating systems. Displayed are the IP address, NetBIOS identifier, DNS name, MAC address, and repository of the offending device. This component identifies unsupported *nix operating systems by the Nessus plugin 33850 (Unix OS No Longer Supported) operating systems via the IP Summary tool.
CNBV - Unsupported Databases: This table shows unsupported databases that have been detected. The component utilizes the plugin name and plugin family filters to determine the plugin ID for the unsupported database. The selected display columns show the plugin ID, plugin name, severity, count and if applicable, the plugin’s VPR.