by Cesar Navas
October 20, 2016
Every organization faces unique challenges in securing and administering networks. Due to business requirements, many organizations rely on internal systems being remotely accessible to support employee mobility needs. However, if left misconfigured, these systems can also provide an entry point for attackers to infiltrate and gain access to internal systems. Once inside, an attacker can also exploit weak controls associated with administrative accounts to launch malware, pivot to other internal systems, and obtain confidential data. Implementing strong authentication policies and limiting administrative access to essential personnel provides the best method to ensuring the security of network assets.
The French Network and Information Security Agency (Agence nationale de sécurité des systèmes d’information or ANSSI) developed the "40 Essential Measures for a Healthy Network" to assist organizations in safeguarding the security of information systems within a network. Following these measures, or rules, for a healthy network will provide basic protection for an organization's critical data. ANSSI states that the majority of IT attacks that have involved ANSSI stepping in could have been prevented had the IT measures set out in the guide been applied.
This dashboard aligns with Section IX of the ANSSI 40 Essential Measures for a Healthy Network guide: Secure Network Administration. This section contains four rules:
- Rule 28 focuses on prohibiting all access to the internet from administrative accounts. Abuse of administrative accounts can compromise critical systems and severely impact the organization. This rule recommends using separate accounts, a non-privileged account for internet access, and an administrative account for administering systems. Non-privileged accounts provide restricted access in comparison to administrative accounts, which can help to reduce the chance of attackers gaining unauthorized access.
- Rule 29 emphasizes using a detected network for the administration of machines or having a network that is logically separate from the user network. By compartmentalizing networks using VLANs, organizations will be able to isolate network traffic and apply additional security controls to protect critical devices within the network.
- Rule 30 advises on not granting administration privileges to users. Users with administrative privileges have the ability to install software and connect personal devices to the network, which can increase security risks and jeopardize the network.
- Rule 31 recommends authorizing remote access for systems that use strong authentication mechanisms. This also includes remote access for network administration purposes, which should use strong authentication policies that have been validated by ANSSI to protect the integrity and confidentiality of network traffic.
This dashboard presents a comprehensive look at administrative user events, privilege changes, remote access activity, external host communications, and administrative compliance issues. Information presented within this dashboard will assist the organization in securing administrative and remote access, which can help to ensure the overall security of the network.
Indicators will provide the latest information on any privilege changes, new users, and group membership changes within the network. Activity from remote access solutions can highlight potential intrusions, long-term events, and unusual activity. Hosts communicating with external systems can alert analysts to botnet activity, compromised hosts, and ports or services that should be disabled. Administrative compliance concerns can help identify systems with misconfigured policies and permissions associated with administrative accounts. Organizations will be able to monitor users with administrative privileges, which can help to detect user accounts with unnecessary privileges and potentially malicious activity.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 6.7.0
- LCE 4.8.0
- NNM 5.1.0
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist in ensuring the security of an organization’s most critical systems. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems and portable devices to determine vulnerabilities and compliance concerns. Passive listening provides real-time monitoring to collect information about user privilege changes and administrative activity. Host data and data from other security devices is analyzed to monitor remote access activity, detect privilege changes, and identify malicious or anomalous behavior from users and devices. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure systems throughout the enterprise.
The following components are included in this dashboard:
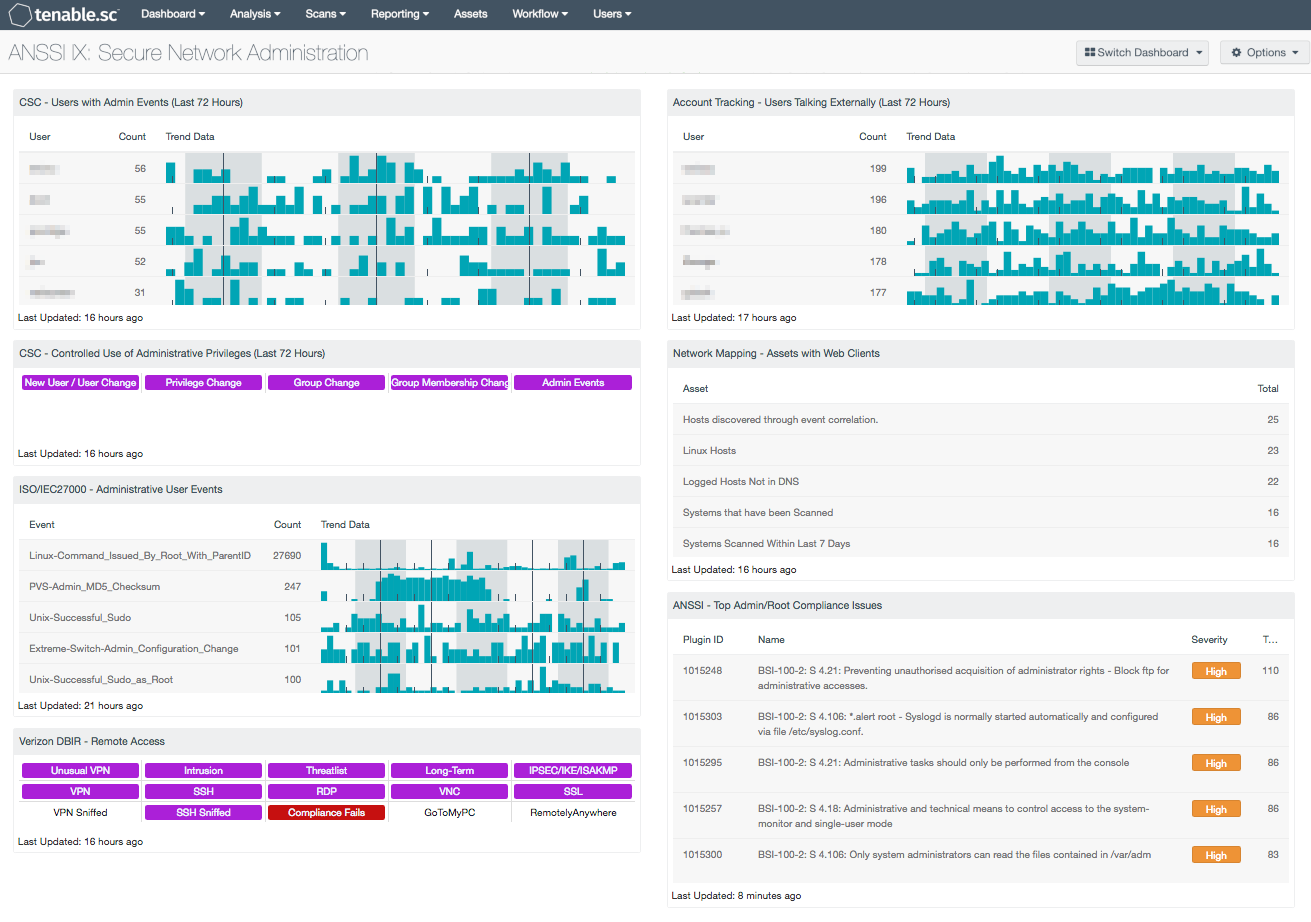
- CSC - Users with Admin Events (Last 72 Hours): This table presents those users associated with events that indicate performed or attempted administrative actions.
- CSC - Controlled Use of Administrative Privileges: This component presents indicators of events related to user accounts and administrative privilege use.
- ISO/IEC27000 - Administrative User Events: The Administrative User Events table presents a list of administrative user events on a network.
- Verizon DBIR - Remote Access: The Verizon DBIR notes that it is important to restrict remote access to systems. This matrix assists the organization in monitoring its remote access.
- Account Tracking - Users Talking Externally: This table displays a list of user accounts associated with internal systems that have communicated with hosts outside of the network over the last 72 hours.
- Network Mapping - Assets with Web Clients: This table presents a list of assets that have detected web clients on the network.
- ANSSI - Top Admin/Root Compliance Issues: This component presents a list of the top administrative privilege compliance issues detected on network hosts.