Tenable Vulnerability Management
Understand Your Exposures and Know Which Vulnerabilities to Fix First
Get a risk-based view of your attack surface to quickly identify, investigate and prioritize your most critical assets and vulnerabilities.
Managed in the cloud and powered by Tenable Nessus, Tenable Vulnerability Management provides the industry's most comprehensive vulnerability coverage with real-time continuous assessment of your organization. Built-in prioritization, threat intelligence and real-time insight help you understand your exposures and proactively prioritize remediations.
Discover Why Industry Experts Choose Tenable
Tenable.io is a great package that takes the powerful Nessus scanner and adds a web-based front end to it that provides a wealth of information about your vulnerabilities and assets. Having full access to the data in a dashboard makes searching it easy. Roles within ...
Tenable we absolutely brilliant in providing help during the pre-engagement stage and also during the implementation of Tenable,io, they have also provided support to us after the too when we needed to increase our licence count during renewal.
It gives assets discovery hence visibility. The CIS benchmark templates help harden the operating systems, databases, network components like routers, switches, firewalls, etc. The built-in dashboard templates are beneficial to administrators and various stakeholde ...
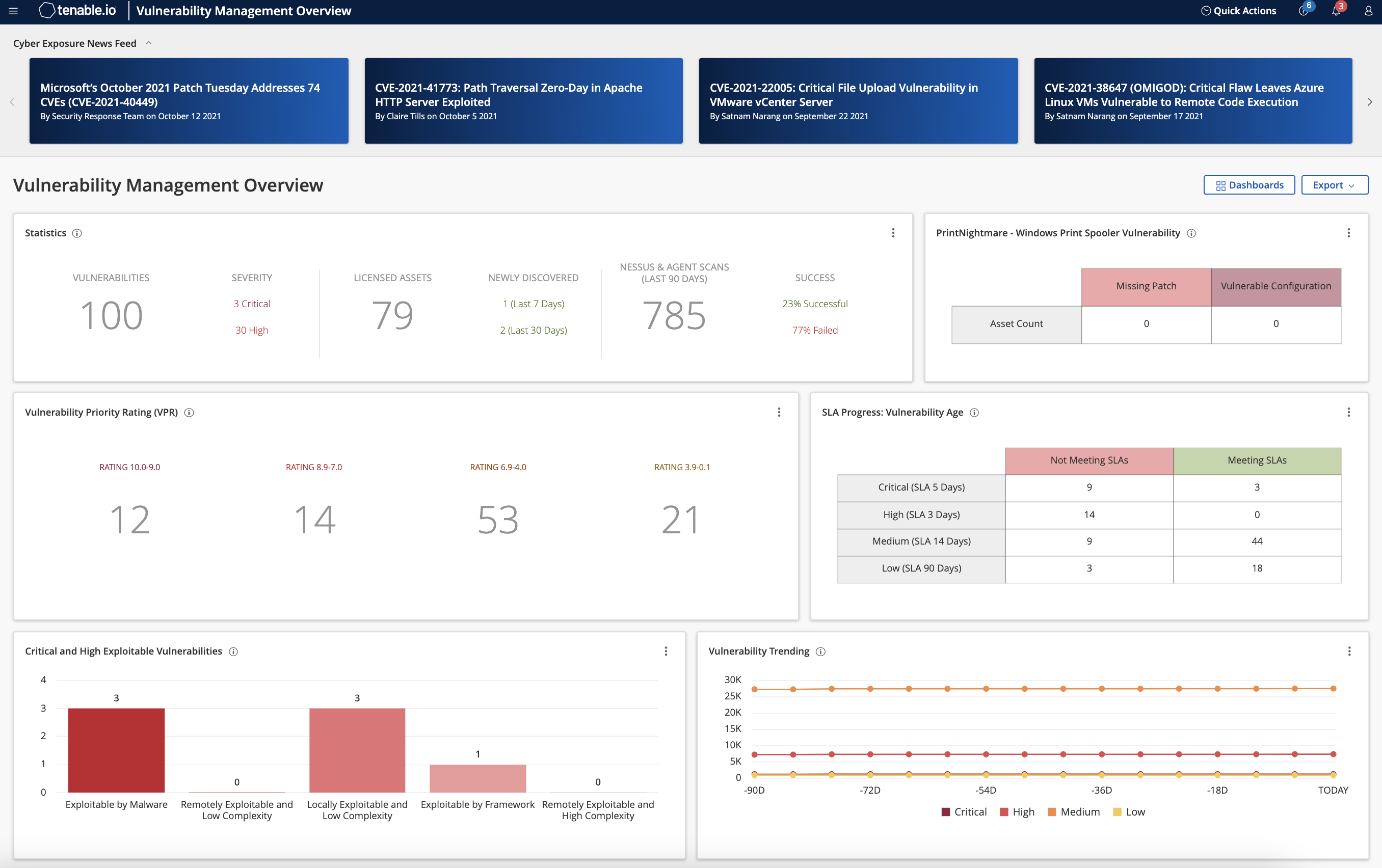
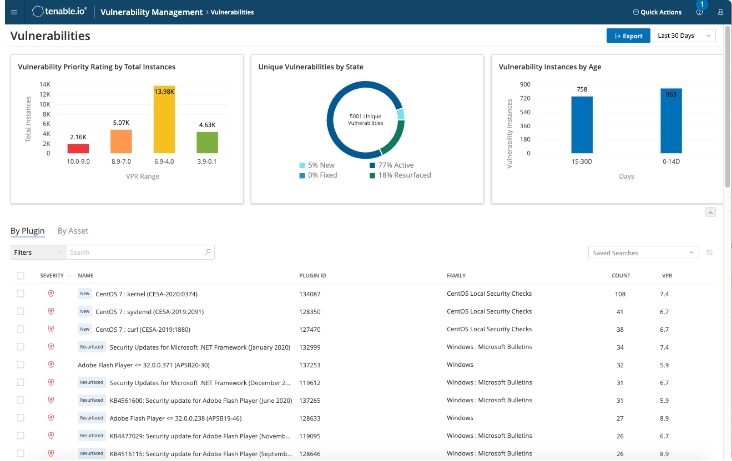
Discover, Assess and Prioritize Vulnerabilities
See Everything
Find hidden vulnerabilities with continuous, always-on asset discovery and assessment of known and unknown assets in your environment, even highly dynamic cloud or remote workforce assets.
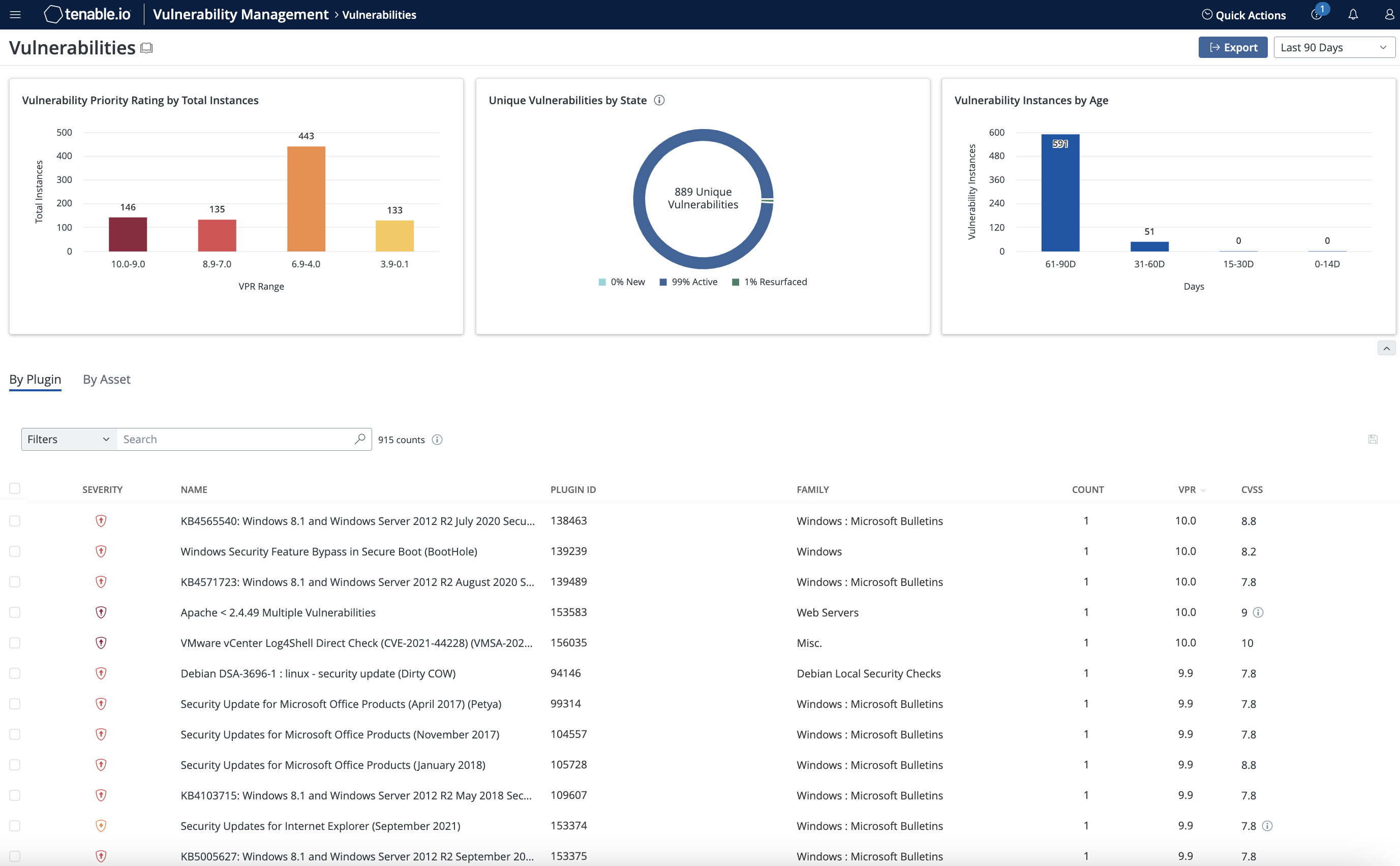
Find and Fix Vulnerabilities Before Attacks Happen
With the industry’s most extensive CVE and configuration coverage you can quickly see scan results and determine exposures. Intuitive dashboard visualizations and easy to understand risk scores ensure you get immediate insight to reduce risk.
Prioritize Vulnerabilities
Identify which vulnerabilities to fix first with automated prioritization that combines vulnerability data, threat intelligence and data science. Built-in prioritization capabilities ensure high risk vulnerabilities are quickly patched.
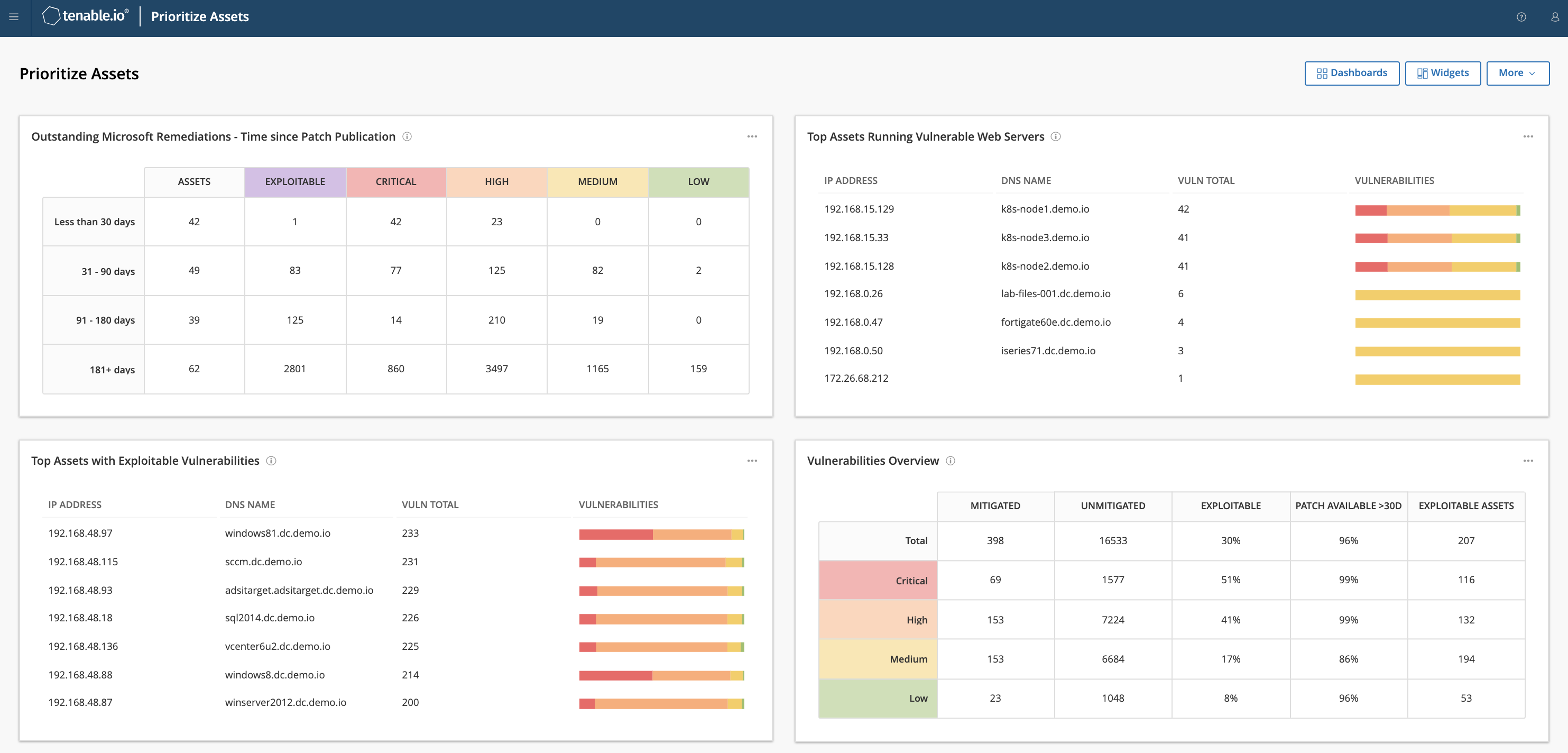
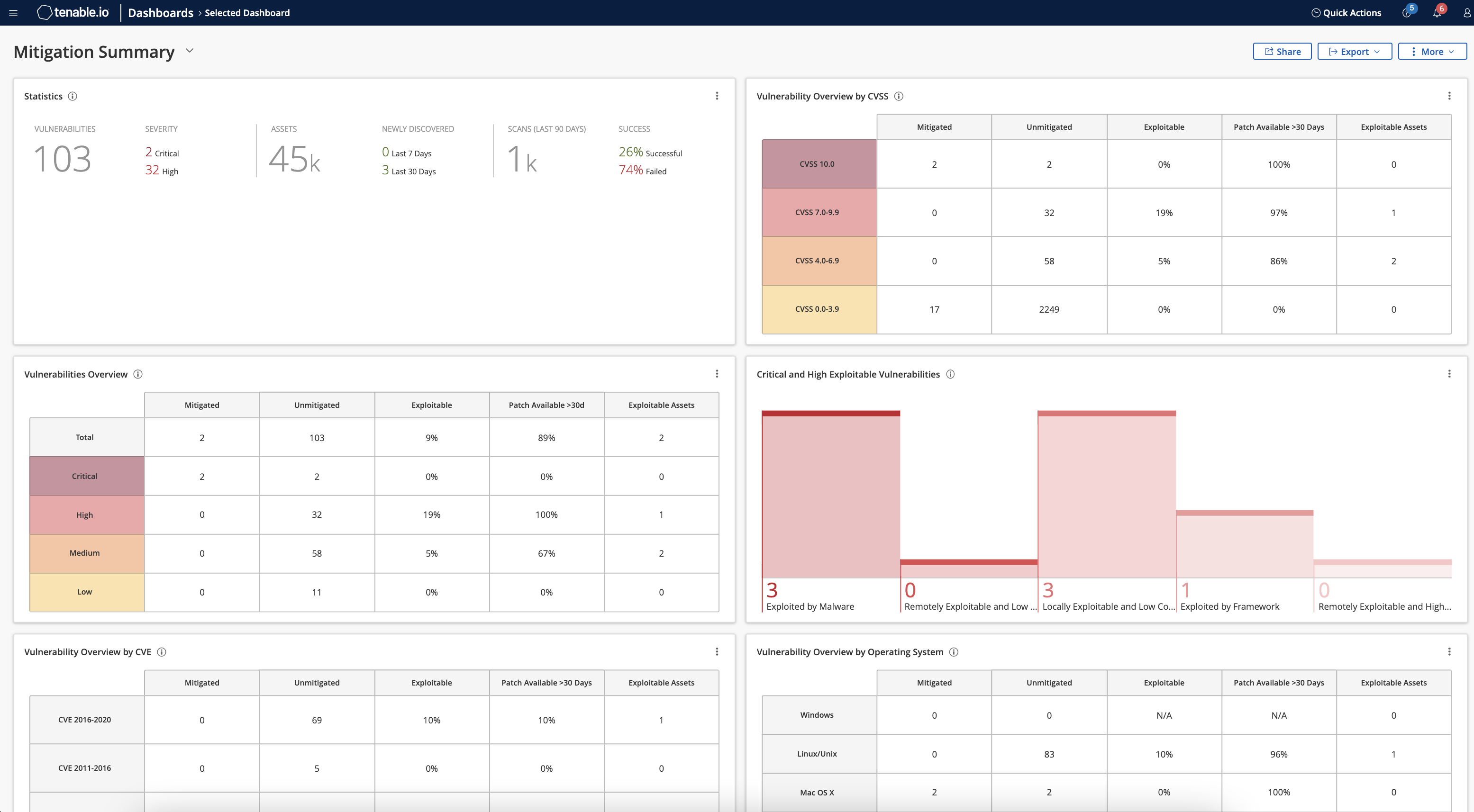
Respond Faster to Disrupt Attacks
Use easy-to-understand risk scores to quickly begin remediation before a breach happens. Take advantage of more than 200 integrations to automate workflows and take decisive action.
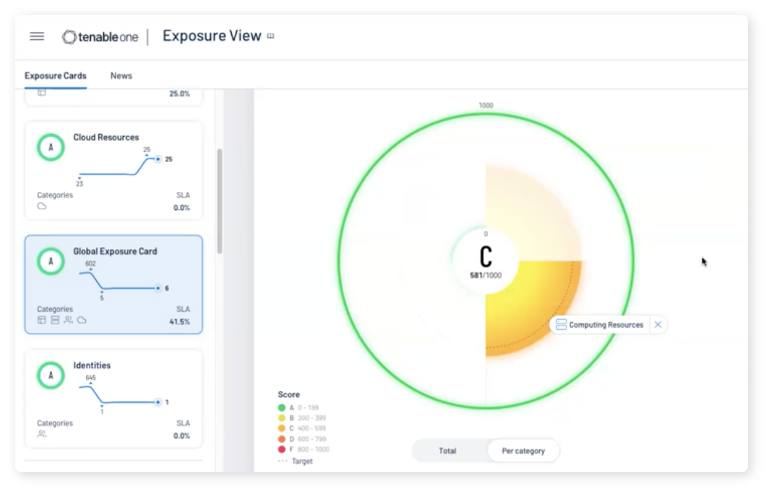
Available Through Tenable One Exposure Management Platform
Tenable One is an exposure management platform designed to help your organization gain visibility across your modern attack surface, focus efforts to prevent likely attacks, and accurately communicate cyber risk to support optimal business performance. The Tenable One platform offers broad vulnerability coverage spanning IT assets, cloud resources, containers, web apps and identity systems.
Learn moreHarness the Power of Data to Respond Faster
Tenable Vulnerability Management is available as part of the Tenable One Exposure Management Platform or as a stand-alone product.
- Continuous discovery and assessment with always-on sensors
- Built-in threat intelligence
- Automated vulnerability prioritization
- Real-time visualization of risk, and tracking of vulnerabilities, assets and remediations
- Built-in vulnerability risk scores to identify risk
- Fully documented API and pre-built integrations

FAQs
Tenable Vulnerability Management is a risk-based vulnerability management platform that gives you full network visibility to predict attacks and quickly respond to critical vulnerabilities. Continuous, always-on discovery and assessment provide the visibility you need to find all assets on your network, as well as hidden vulnerabilities on those assets. Built-in prioritization, threat intelligence and real-time reporting help you understand your risk and proactively disrupt attack paths. Built on leading Tenable Nessus technology and managed in the cloud, you get complete visibility of the assets and vulnerabilities on your network so you can quickly and accurately understand your risk and know which vulnerabilities to fix first.
Tenable Vulnerability Management and Tenable Security Center are both leading vulnerability management solutions that give you a comprehensive view of all the assets and vulnerabilities on your network so you can understand cyber risk and know which vulnerabilities to fix first. The key difference between the solutions is how they are managed. Tenable Vulnerability Management is managed in the cloud, while Tenable Security Center is an on-prem solution. For a comprehensive understanding of the differences between the products, contact your Tenable certified partner or Tenable representative for more information.
Tenable Vulnerability Management is available as a critical component of the Tenable One platform or as a stand-alone product. Tenable Vulnerability Management powers the Tenable One Exposure Management Platform with vulnerability management capabilities such as:
- Continuous discovery and assessment with always-on sensors
- Built-in threat intelligence
- Automated vulnerability prioritization
- Real-time visualization of risk, and tracking of vulnerabilities, assets and remediations
- Built-in vulnerability risk scores to identify risk
- Fully documented API and pre-built integrations
Tenable One is a comprehensive exposure management platform that translates technical asset, vulnerability and threat data into clear business insights and actionable intelligence for security executives and practitioners. The platform combines the broadest vulnerability coverage spanning IT assets, cloud resources, containers, web apps and identity systems, builds on the speed and breadth of vulnerability coverage from Tenable Research, and adds comprehensive analytics to prioritize actions and communicate cyber risk.
The following applications can be purchased with, or independently from Tenable Vulnerability Management, or as part of the Tenable One bundle:
- Tenable Vulnerability Management Web App Scanning (WAS)*: Comprehensive vulnerability scanning for modern web applications. Its accurate vulnerability coverage minimizes false positives and negatives, ensuring your security team understands true security risks in your web applications.
- Tenable Lumin*: A visualization, analytics and measurement solution allowing you to visualize your cyber risk, track risk reduction over time and benchmark against your industry peers.
- Tenable Cloud Security*: Analyzes cloud infrastructure for vulnerabilities and misconfigurations to help secure cloud resources, container images, cloud assets, and Infrastructure as Code (IaC).
- Tenable OT Security: Provides protection for industrial control networks from cyber threats, malicious insiders and human error. You get unmatched visibility into converged IT/OT operations and leading security capabilities to maximize your operational environments visibility, security and control.
- Tenable PCI ASV: Streamlines the ASV process, including running scan, resolving disputes and preparing compliant scan reports.
- Tenable Identity Exposure*: Enables customers to find and fix weaknesses in Active Directory before attackers exploit them and respond to attacks in real time.
*Application included in the Tenable One platform
Tenable is committed to protecting the confidentiality, integrity and availability of all customer data. Tenable Vulnerability Management data is encrypted in transit and stored using TLS Encryption ciphers. AES-256 Encryption is applied to application infrastructure layers.
The Tenable cloud platform is built on isolated, private networks and uses multiple network controls such as container isolation, inbound/internal traffic restrictions, monitoring of traffic rates, sources and types at multiple network points.
Tenable also implements multiple access controls to help customers control data access, as well as performs frequent vulnerability, docker container and web application scans to conduct periodic security assessments.
For detailed descriptions of the applied security measures, review the Tenable Trust and Assurance webpage or the Data Security and Privacy data sheet.
Tenable Vulnerability Management is licensed by annual subscription and priced by asset, rather than by IP address. Our proprietary asset-counting algorithm leverages multiple asset attributes to programmatically identify unique assets to reduce duplication.
An asset is:
- A physical or virtual device with an operating system connected to a network
- A web application with an FQDN
- An active (not terminated) cloud resource
Yes. Tenable provides the vulnerability management industry’s first uptime guarantee of 99.95% through a robust service level agreement (SLA) with service credits offered if the SLA is not met.
Tenable uses the AWS platform and other leading technologies to ensure high availability for customers. Using fault tolerant and redundant components, Tenable ensures you get the best possible service with minimal downtime.
Technical documentation for all Tenable products, including Tenable Vulnerability Management, is at https://docs.tenable.com.
To learn more about Tenable Vulnerability Management, please visit the Tenable Vulnerability Management product page, register for a free evaluation or contact your Tenable certified partner or Tenable representative for more information.
To purchase Tenable Vulnerability Management, you can work with your local certified partner, contact your Tenable representative or visit tenable.com.