Secure Configuration Baselines for Network Devices
In a recent blog post, Ted Gary discussed results from a Tenable survey about configuration hardening at the system level. In short, organizations are making progress on enforcing and auditing their desktops and servers for secure configurations, but there is still a lot of work to do. While the whole realm of network devices was beyond the scope of the survey, it obviously can’t be beyond that of your hardening efforts.
Background
Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices and endpoints equally:
NIST Cybersecurity Framework
PR.IP-1 - A baseline configuration of information technology/industrial control systems is created and maintained.
NIST 800-53 rev 4
CM-2 - Baseline Configuration CM-2(1) - Reviews and Updates
ITSG-33 (Canada)
CM-2 - Baseline Configuration
CM-2(1) - Reviews and Updates
CM-2(2) - Automation Support for Accuracy/ Currency
Some frameworks and standards, like the Center for Internet Security (CIS) Controls and Payment Card Industry Data Security Standard (PCI-DSS), see the management of the network itself as important enough to justify its own sections and recommendations, in addition to their general system requirements.
CIS Controls
11 - Secure Configurations for Network Devices
PCI-DSS
1.1 – Establish and implement firewall and router configuration standards.
1.1.7.a – Verify that firewall and router configuration standards require review.
2.2 - Develop configuration standards for all system components.
The central theme of all of these recommendations across the various frameworks is fundamentally a threefold process.
- Design and implement a secure hardened baseline across the devices in your organization.
- Monitor and validate that the baseline has been implemented and drift doesn’t occur.
- Periodically review the baseline and update it according to new threats and the ever-evolving environment.
Some of the best starting places for building the secure baseline for a number of devices are either the CIS Benchmarks or the Defense Information Systems Agency (DISA) Secure Technical Implementation Guides (STIG). These resources provide technical hardening recommendations for many popular and widely implemented devices.
If a particular device in your environment is not covered by a CIS Benchmark or DISA STIG all hope is not lost. Most vendors provide their own stand-alone hardening guides. For example, Juniper Networks published their own guide, “Hardening Junos Devices”. Much like in the desktop and server environment, there’s a chance that none of the recommendations are going to be a perfect fit out-of-the-box for all environments. If that’s the case, there might be a need to tailor one or a combination of several in order to get a complete baseline. The important lesson here is that multiple resources exist to help you build the initial baselines and avoid having to start with a blank slate.
Tenable Solutions
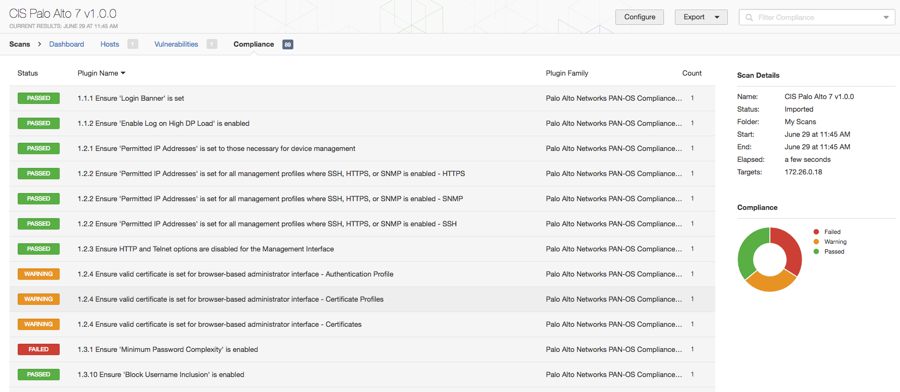
Tenable's secure configuration auditing solutions provide a number of audit files for network devices. Right alongside your regular vulnerability scanning you can test and validate the configuration baselines you defined for the organization. These audit files cover a wide range of devices from Cisco and Juniper to Palo Alto Networks and Huawei. Any of these devices can be evaluated for a number of different configuration parameters and generally have multiple audit files available.
Most of the audit files are built according to the CIS Benchmark or DISA STIG recommendations, and in general, overlap quite a bit. For example, testing DNS and NTP server settings, validating whether specific services or protocols are enabled and/or configured correctly, and checking that accounts and authentication are setup properly for local and remote management are all included in both standards and have checks in Tenable audit files.
If your organization requires a hybrid or tailored version of one of the benchmark documents, a completely custom audit file can be created or, in many cases, one of the standard files can be customized by adding/removing checks or modifying acceptable values.
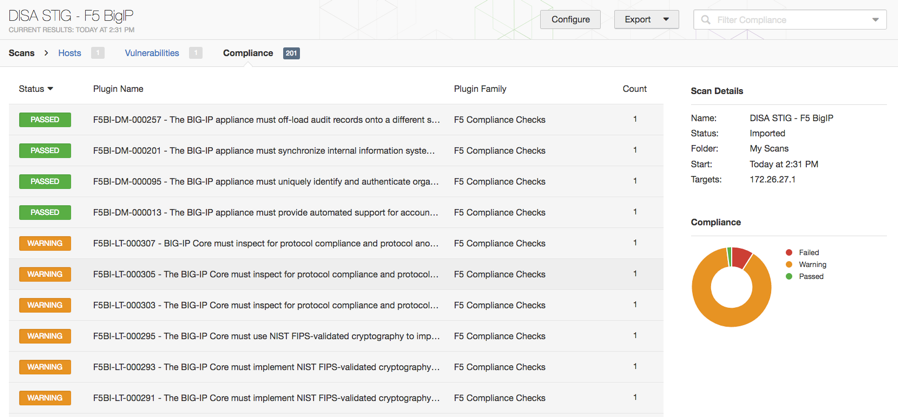
Recent Additions (F5 and Arista Devices)
Recently, Tenable has added support for additional network devices, specifically F5 BigIP and Arista MLS devices.
Our support for F5 covers a number of its technologies from the Advanced Firewall Manager and Application Security Manager to Device and Local Traffic Management.
Alongside these new plugins are accompanying audits based on the DIS STIG guidance that has been released. A full list of available DISA STIG documents is available from the DISA Information Assurance Support Environment (IASE) homepage.
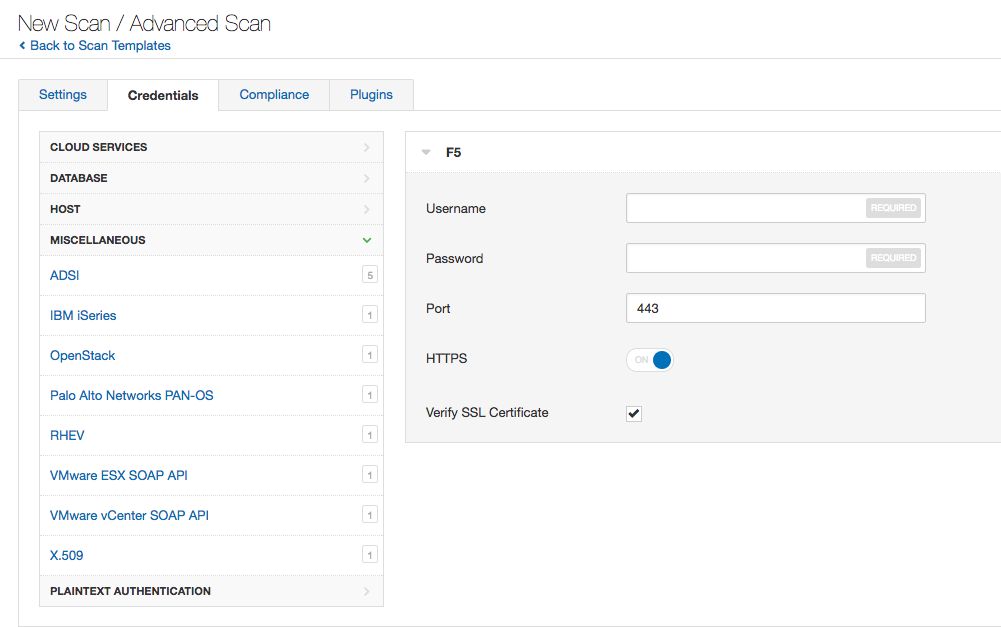
Scans of F5 devices are very similar to many of the existing network device scans. F5 scans can be initiated from both the Advanced Scan or Policy Compliance templates. Inside either of those templates should be a new entry for the F5 credentials under Miscellaneous in the credentials tab.
Under the Compliance tab, you should also see a new entry for F5 which allows both the upload of custom audit files in addition to the list of audit files Tenable has released.
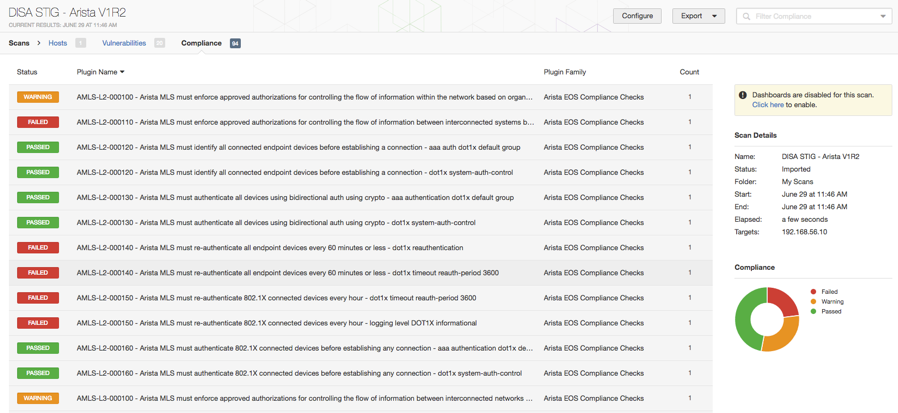
Like F5 devices, online Arista scans can be initiated from both the Advanced scan and Policy Compliance templates. For online scans, an SSH login is required and the credentials are stored just like any other SSH login. A new Arista section contains the custom audit upload along with the list of Tenable provided audits.
Offline Audit Support
Arista devices can also be audited in offline mode which is often convenient for validating backed-up configurations or testing a baseline configuration before it's rolled out. Offline scans are configured via the Offline Configuration Audit template.
An offline scan doesn’t require any credentials, so an SSH login is unnecessary. Setting up the audit only requires you to select an audit file or upload your custom audit and then add the configuration file you would like to be evaluated on the Compliance tab.
Wrap-Up
When planning the baseline hardening for network devices, it’s important to keep in mind that, in most cases, issues with devices such as firewalls, routers and load balancers, will ripple across the environment. A device’s configurations aren’t limited to providing its own services and protecting itself, but they also play a significant role in most organizations’ layered security practices. A compromised firewall doesn’t just mean it isn’t filtering and passing traffic, it might also be putting other devices at risk to threats they are unable or not configured to handle.
How Tenable Can Help
Tenable products offer a wide range of audit files for most popular network device platforms like Cisco, Juniper and Huawei, along with the addition of F5 and Arista. Many of these can be conducted both online against running systems and in offline mode against an exported configuration file. This offline support often proves very handy in developing a secure baseline since changes can be tested and the results are available immediately against your chosen audit file.
- Security Frameworks
- Vulnerability Management