by Josef Weiss
September 1, 2015
WordPress is a popular Content Management System (CMS). Content Management Systems are web applications that make it easier to manage a website. A CMS typically allows for the creation, editing, publishing, organizing, and management of web-based content from a central interface. Much of the backend, or behind the scenes management, such as generating navigational elements, indexing, and more are automated, requiring less technical knowledge to manage the content of a website.
Many Content Management Systems are built on open source frameworks, and that makes them appealing as shared development offers many benefits. However, their popularity often also makes them appealing targets to malicious attacks. Statistically, WordPress is one of the most popular, and most frequently deployed CMS, according the data collected of the top 10 million website by Alexa. WordPress vulnerabilities can potentially turn into virtual gold mines for attackers. Add to this the fact that Content Management Systems require a database on the backend, common database vulnerabilities such as potentially weak or default passwords, missing patches, and default installations can leave an organization very vulnerable to attack.
There are a number of things an organization can do to protect against WordPress vulnerabilities. The most significant would be to keep the WordPress application, corresponding WordPress plugins, and the underlying OS, Apache, MySQL, and PHP patched (LAMP).
Considering the large number of available WordPress plugins and customizable options available to CMS installations, each WordPress installation typically becomes an individual snowflake. Keeping up-to-date on the application and each and every WordPress plugin, along with all the open source developers associated with them, is a relatively daunting task. This WordPress Security dashboard assists in identifying WordPress and WordPress plugin vulnerabilities present in the environment. Tenable recommends this dashboard be used with the Web Application Scan Policy, proper OS Compliance Scan, and CIS MySQL compliance audit. Optionally, the WordPress Dynamic Asset can be used to provide a more centralized collection of information on WordPress servers, all of which are available as items available conveniently and directly within SecurityCenter. Vulnerabilities are presented in tables that identify all common vulnerabilities, exploitable vulnerabilities, and WordPress plugin vulnerabilities in tables, severity charts, indicators, and IP network-specific views.
As WordPress requires Apache, MySQL and PHP to function, this dashboard will also provide vulnerability data for those applications, as well as the underlying OS. This allows the analyst to quickly and effortlessly identify which vulnerabilities exist within the WordPress environment, further allowing the organization to create a patch schedule to update and patch their WordPress installations and WordPress plugins.
Tenable recommends running MySQL compliance scans against systems running WordPress, along with OS compliance scans. Vulnerabilities from these scans will also appear in the tables of the WordPress Security dashboard. Additional tables can be added to provide summary information on database or underlying OS specific vulnerability details if so desired. If Tenable’s Passive Vulnerability Scanner (PVS) is installed within the environment, vulnerability data as it pertains to WordPress installations will also be displayed.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- SecurityCenter 5.0.1
- Nessus 6.4.2
- Database Compliance Audit File
SecurityCenter Continuous View (CV) provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. SecurityCenter CV enables the analysts to react to advanced threats, zero-day vulnerabilities, and new forms of regulatory compliance. With more supported technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure, SecurityCenter CV users are more prepared for the dynamic changing environment.
The dashboard contains the following components:
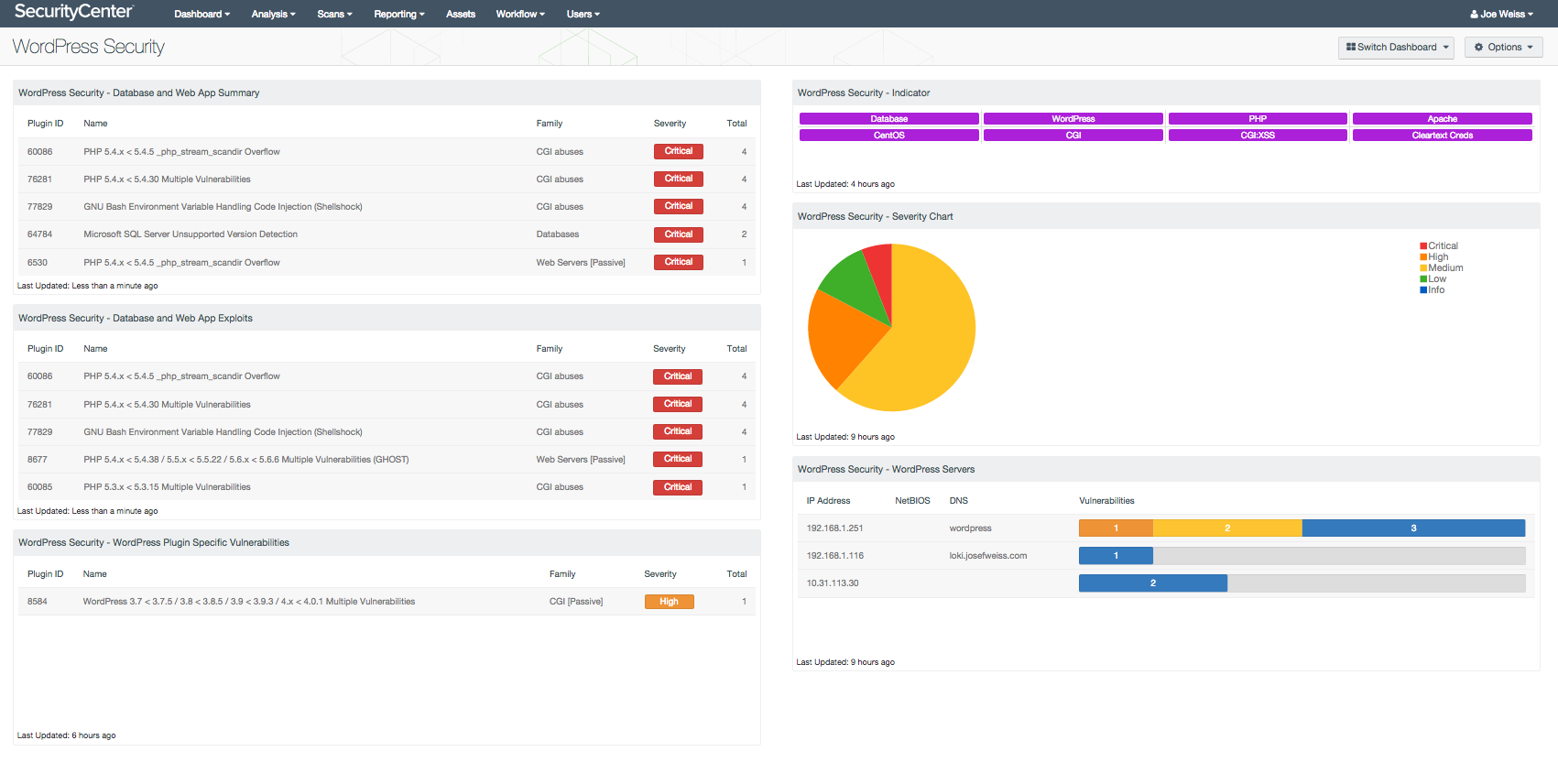
- WordPress Security – Database and Web App Summary - The WordPress Vulnerability Summary table displays vulnerability summary information for CGI abuses, Web Servers and Databases. The vulnerability data is sorted from high to low severities and provides the analyst with information on vulnerabilities information for WordPress associated applications. Additionally, compliance scans are recommended against MySQL or OS utilizing the WordPress Asset as a target. Those results will assist the analyst to resolve all WordPress and LAMP related vulnerabilities, allowing the analyst to view a complete dataset of vulnerabilities against WordPress servers from one location.
- WordPress Security – Database and Web App Exploits - The WordPress Exploitable Vulnerabilities table displays vulnerability summary information on known exploitable vulnerabilities for CGI abuses, Web Servers and Databases. The vulnerability data is sorted from high to low severity and provides the analyst with information on WordPress associated applications. These vulnerabilities should take priority in resolving as exploits are known and readily available. Additionally, compliance scans are recommended against MySQL or OS utilizing the WordPress Asset as a target. Those results will assist the analyst to resolve all WordPress and LAMP related vulnerabilities, allowing the analyst to view a complete dataset of vulnerabilities against WordPress servers from one location.
- WordPress Security – WordPress Plugin Specific Vulnerabilities - The WordPress Plugin Vulnerabilities table displays summary information on WordPress plugin vulnerabilities provided by scans against WordPress devices utilizing the Web Application Scan Policy. The vulnerability data is sorted from high to low severity and provides the analyst with specific information on WordPress plugin vulnerabilities from a scan against WordPress devices utilizing the Web Application Scan Policy. This allows the analyst to isolate and view a complete dataset of WordPress plugin-specific vulnerabilities against WordPress servers from one location.
- WordPress Security – Indicator - The WordPress Indicator matrix displays vulnerability data for WordPress related applications. This is valuable as specific vulnerabilities can be identified such as OS, Apache, database and PHP, and can each have a triggered indicator. Additionally, if scans compliance scans against MySQL or operating systems are conducted with the WordPress assets as a target, those results will also be present in this table. This allows the analyst to rapidly determine the overall vulnerability state, by severity, of individual WordPress servers from one location.
- WordPress Security – Severity Chart - The WordPress Severity Chart displays severity information in a pie chart format provided by scans against WordPress devices utilizing the Web Application Scan Policy. The severity chart provides the analyst with information on enterprise-wide WordPress vulnerabilities in an easy to understand format. Additionally, compliance scans are recommended against MySQL or operating systems utilizing the WordPress Asset as a target. Those results will assist the analyst resolving all WordPress and LAMP related vulnerabilities, allowing the analyst to view a complete dataset of vulnerabilities against WordPress servers from one location.
- WordPress Security – WordPress Servers - The WordPress Servers table displays vulnerability counts in a table format provided by scans against WordPress assets utilizing the Web Application Scan Policy. The table provides the analyst with information on individual WordPress server vulnerabilities in an easy to understand format. Each known server can be easily and quickly identified by its IP address and DNS or NetBIOS name, if available, providing the analyst with server-specific vulnerability information. Additionally, if scans compliance scans against MySQL or operating systems are conducted with the WordPress assets as a target, those results will also be present in this table. This allows the analyst to rapidly determine the overall vulnerability state, by severity, of individual WordPress servers from one location.