by David Schwalenberg
February 26, 2016
User account management, access control, and enforcement of least privilege are critical to effective network security. Without proper user account management, an organization may not know who has access to their network, whether or not the old accounts of former employees are still active, and whether or not user passwords meet policy requirements. Without proper access control and enforcement of least privilege, users on the organization's network may inadvertently access information they should not access, change files, or install malware on the network. This increases the risk of network intrusion and compromise, insider activity, and data loss. Monitoring user access and least privilege and taking appropriate actions are very important to protect the organization.
This dashboard aligns with the NIST Cybersecurity Framework (CSF) subcategories PR.AC-1 and PR.AC-4 that deal with user account management, credential management, and least privilege. The CSF provides guidance based on existing standards, guidelines, and practices, which can be tailored to specific organizational needs. This dashboard can assist an organization in understanding and controlling user accesses and enforcing least privilege.
This dashboard provides components to assist an organization in identifying the users on its network, monitoring for any account and credential vulnerabilities, and identifying any user access, password requirement, or least privilege compliance failures. The dashboard also provides components that allow an organization to monitor user access-related events and changes, such as first time logons to a system, systems that logged into other systems using administrative accounts, and systems on which passwords expired, accounts were disabled, and privileges or group memberships were changed. Indicators for suspicious and anomalous user activity are also presented. Analysts can use this dashboard to easily drill down into the data presented and gain more detailed information.
This dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.50
- LCE 6.0.0
- NNM 4.4.0
- ComplianceData
Tenable.sc Continuous View (Tenable.sc CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with the Nessus Network Monitor (NNM), as well as log correlation with the Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network.
This dashboard contains the following components:
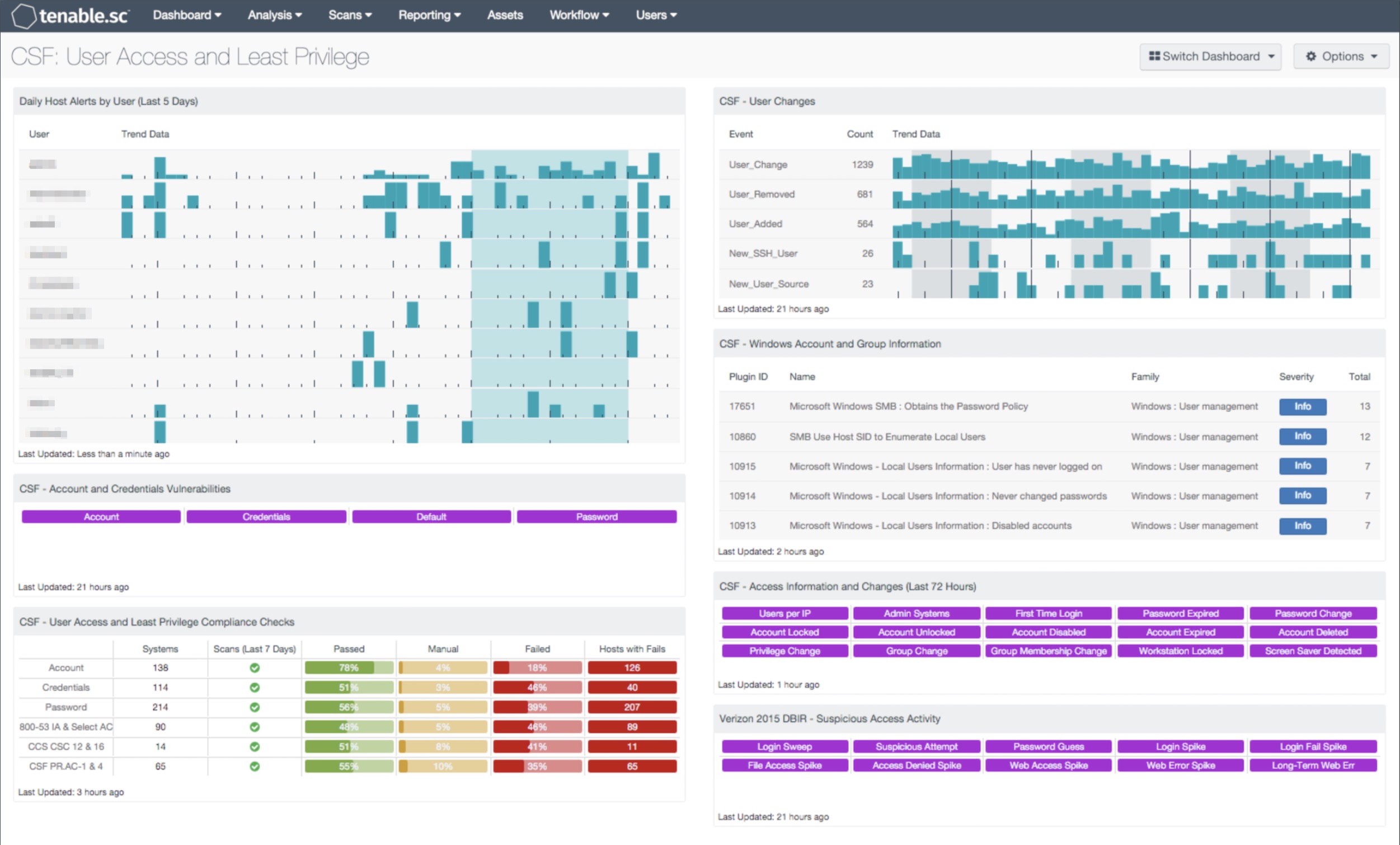
- Daily Host Alerts by User (Last 5 Days): Most users in an organization have a typical pattern of when they use an organization’s resources. This component shows when users generate alerts with hosts in the organization. Using this component, analysts can quickly determine user activity outside of expected work hours.
- CSF - Account and Credentials Vulnerabilities: This component displays warning indicators for vulnerabilities actively and passively detected on the network related to accounts and credentials. A purple indicator means that one or more vulnerabilities contain the specified keyword. Clicking on a highlighted indicator will bring up the vulnerability analysis screen to display details on the vulnerabilities and allow further investigation. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present. Setting the tool to Vulnerability Detail List will display the full details on each vulnerability, including a description, the solution to fix the vulnerability, and in some cases, links to more information.
- CSF - User Access and Least Privilege Compliance Checks: This component displays user access and least privilege compliance information in areas such as password requirements, lockout policy after failed logins, and controlled use of administrative privileges. The first rows display compliance information by keyword. The last rows display user access and least privilege compliance information related to several standards: NIST 800-53 (IA family and selected AC controls), CCS Critical Security Controls (v5.1, CSC 12 and 16), and the Cybersecurity Framework (PR.AC-1 and PR.AC-4). For each row, the columns provide the number of hosts audited, whether an audit scan was run in the last seven days, the ratios of passed audit checks (in green), checks that require manual verification (in orange), and failed audit checks (in red), and the count of hosts with failed checks. Clicking on a highlighted indicator in the Hosts with Fails column will bring up the vulnerability analysis screen to display the systems with failed audit checks and allow further investigation. Note that in order for data to appear in this component, appropriate audit/compliance scans must first be run on the network.
- CSF - User Changes: This component presents data on new and existing user events on the network over the past 72 hours. The LCE normalized events of ‘User_Added’, ‘User_Change’, ‘User_Removed’ and ‘New_User’ are displayed within this table. These detected event changes will display information on new user accounts, user account password changes, rights access, and new user logins seen for the first time. The data within this component will be highly valuable to any analyst in determining the presence of unauthorized accounts on the network.
- CSF - Windows Account and Group Information: This table displays detections of Windows account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists. This information is obtained through Nessus credentialed scans. Most of these detections will contain lists of accounts in their output. The Obtains the Password Policy detection will contain the retrieved password policy in its output. Clicking on the Browse Component Data icon on the component will bring up the vulnerability analysis screen to display the detections and allow further investigation. In the analysis screen, setting the tool to Vulnerability Detail List will display the full details for each detection, including its description and output.
- CSF - Access Information and Changes (Last 72 Hours): This matrix component can help an analyst quickly pull up information on systems where certain user access-related events and changes have occurred. This includes such information as the first time users logged into a system, and systems on which passwords expired, accounts were disabled, and privileges or group memberships were changed. If an event occurred in the last 72 hours, the indicator will be highlighted purple; an analyst can use this to determine whether an expected behavior such as workstations locking or accounts expiring is happening at all. Clicking on the highlighted indicator will bring up the event analysis screen to display details on the events and allow further investigation. In the analysis screen, setting the tool to IP Summary will display the systems on which the events happened. Setting the tool to Raw Syslog will display the raw syslog of the events, which can give more details. Also, the LCE keeps track of all users that logged into each host and all systems that logged into other systems using administrative accounts; this information is available by clicking on the Users per IP and Admin Systems indicators, respectively.
- Verizon 2015 DBIR - Suspicious Access Activity: This matrix assists the organization in monitoring for suspicious access activity such as suspicious login activity and spikes in file and web accesses. Each indicator is based on one or more LCE events; the indicator is highlighted purple if the event occurred in the last 72 hours. Login spikes can occur when an account is compromised and shared and used by many hackers. Login failure spikes may indicate brute-force password guessing. File access and access denied spikes may indicate suspicious access to files. Web access spikes may indicate a busier-than-normal web server or more Internet browsing. Web error spikes and long-term Web errors can identify web application scanning and web probes. Clicking on a highlighted indicator will bring up the analysis screen to display details on the events and allow further investigation.