by Cody Dumont
August 22, 2023
Web application security is a key concern for any organization that develops or uses web applications. The software security community created the Open Web Application Security Project (OWASP) to help educate developers and security professionals on the latest web application security risks. This dashboard provides organizations the ability to monitor web applications by identifying the top 10 most critical web application security risks as described in OWASP's Top 10 Application Security Risks document for 2021.
The OWASP Application Security Risks document outlines several different categories of web-based security concerns, such as Cross-Site Scripting attacks (XSS), security misconfigurations, and sensitive data exposure. OWASP's focus is to reduce risk across the most vulnerable business assets across the internet. Following these guidelines empowers organizations to reduce risk of organizational and consumer data theft.
Administrators need to ensure that their organization is not vulnerable to any of the attacks identified by OWASP. Remediating compliance related issues, such as known vulnerable components and insufficient logging, is important to eliminate gaps in an organization's infrastructure that are not directly tied to exploitable attacks.
These dashboards are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboards can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 6.2.0
- Tenable Web Application Scanning
This dashboard covers all versions of the OWASP Top 10 from 2010 to 2021, and provides administrators the tools and information needed to aid their efforts. The dashboard provides comparative view between version, using the cross-reference field utilized by plugins. The information will guide organizations on the actions to mitigate business risk through strong security practices.
Components
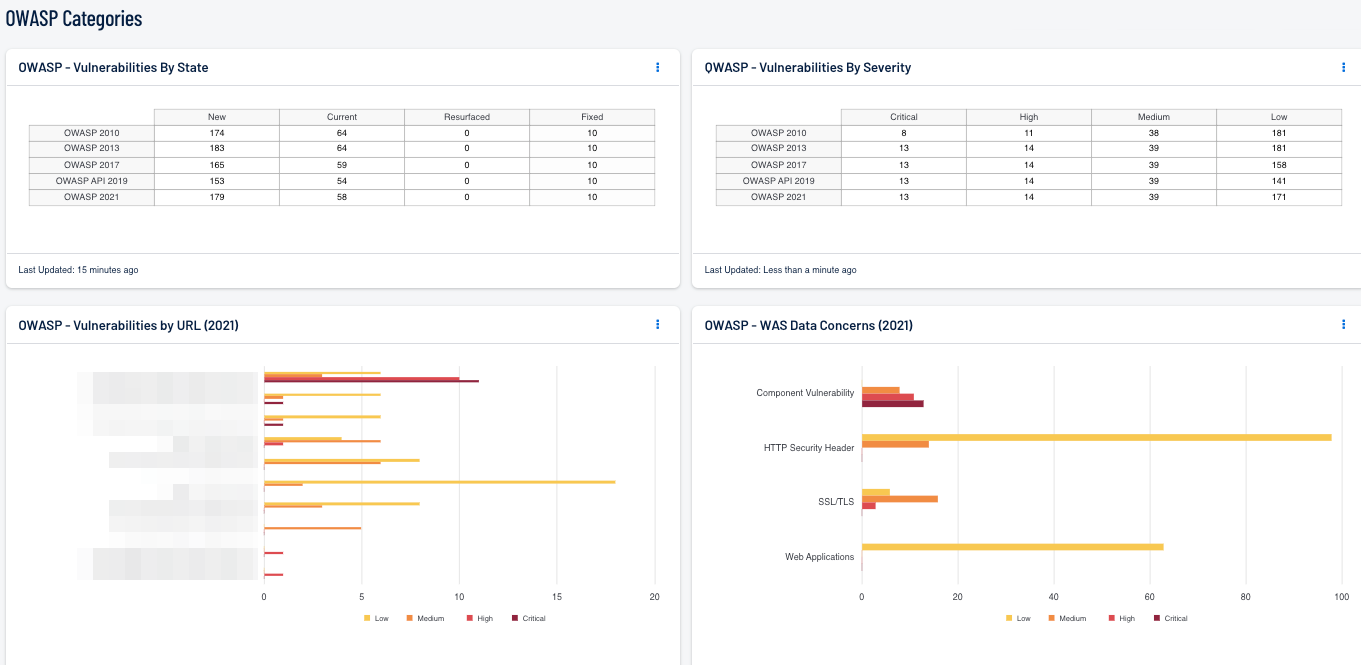
WAS Data Concerns: This bar chart displays current (2021) OWASP vulnerability counts, sorted by plugin family and severity. According to OWASP, "the Top 10 represents a broad consensus about the most critical security risks to web applications." Identifying and fixing these issues provides organizations with a solid foundation for secure web development.
OWASP Categories by URL: This component displays vulnerability status counts for each Uniform Resource Locator (URL) within the organization. The URLs are sorted from those with the highest, most severe vulnerabilities to the least severe. Each URL has a graph of severity results for each severity category.
OWASP Versions by State: This matrix displays the current and all previous OWASP versions along with a column displaying each state (New, Current, Resurfaced, Fixed). This information assists organizations in identifying OWASP vulnerabilities that are new, currently active, have previously been mitigated and have resurfaced, or have been fixed, for each OWASP version.
OWASP Versions by Severity: This matrix displays the current and all previous OWASP Top 10 from Critical to Low. Each cell displays data on the count of web application vulnerabilities associated with the OWASP Top 10 release, and severity level. This information assists organizations in identifying the most severe OWASP vulnerabilities for the OWASP version in use.