by Andrew Freeborn
October 10, 2016
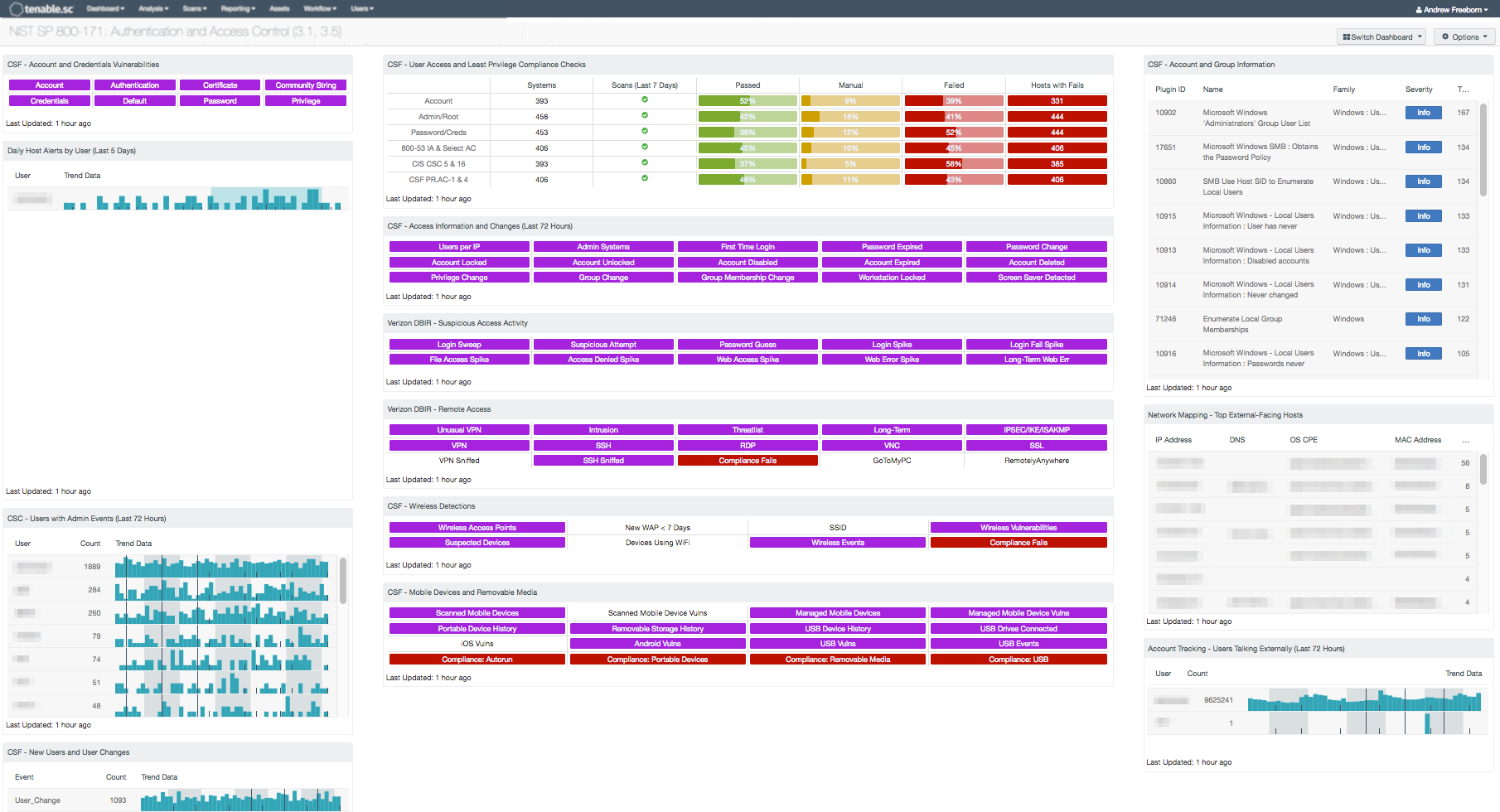
Organizations rely on robust authentication, access control, and enforcement of least privilege to protect critical systems and sensitive data. Without proper user authentication and account management, an organization may not know who has access to their network, whether or not the old accounts of former employees are still active, and whether or not user passwords meet policy requirements. Default credentials that have not been changed and are well known to attackers could allow systems to be exploited and data to be lost. Without enforcement of least privilege, users on the organization's network may inadvertently access systems or information they should not access, change files, or install malware on the network. Without proper access control, intruders may gain access to the organization's network and sensitive data through compromised mobile devices or removable media, or through remote or wireless means.
The federal government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. Sensitive but unclassified federal information is routinely processed by, stored on, or transmitted through nonfederal information systems. Failing to properly protect this Controlled Unclassified Information (CUI) could impact the ability of the federal government to successfully carry out required missions and functions.
The National Institute of Standards and Technology (NIST) created Special Publication 800-171 "Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations" to provide recommended requirements for protecting the confidentiality of CUI. Federal agencies should use these requirements when establishing contracts and agreements with nonfederal entities that process, store, or transmit CUI.
This dashboard aligns with the Access Control (section 3.1) and Identification and Authentication (section 3.5) families of security requirements in NIST SP 800-171. These families are closely related and focus on limiting access to CUI through control of information system access and strong user authentication. Using this dashboard, an organization will be better able to monitor authentication and access control, and address any issues.
Components on this dashboard assist an organization in identifying users on the network, identifying users who have performed administrative actions on the network, and identifying users associated with outbound traffic. Additional components assist in monitoring for account and credential vulnerabilities, and identifying compliance failures related to user access, password requirements, and least privilege. Components are also provided that allow an organization to monitor user access-related events and changes, such as first time logons to a system, login failures due to expired passwords or disabled accounts, and privilege and group membership changes. Indicators for suspicious and anomalous user activity are shown. Remote access activity and wireless activity are presented, along with mobile device, removable media, and external-facing host information. This information will assist the organization in managing and properly restricting access to information systems that process, store, or transmit CUI. Analysts can use this dashboard to easily drill down into the data presented and gain more detailed information. If necessary, assets or subnet filters can be used to narrow the focus of this dashboard to only those systems that process, store, or transmit CUI.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.4.0
- LCE 6.0.0
- NNM 5.9.0
- Compliance data
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in securing and controlling access. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find account and credentials vulnerabilities and enumerate system information. Audit files can be used to assess compliance with authentication policies. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security investments is analyzed to monitor user activity across the network. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure user authentication, control access, and safeguard sensitive information.
The following components are included in this dashboard:
- CSF - Account and Credentials Vulnerabilities: This component displays warning indicators for vulnerabilities actively and passively detected on the network related to accounts and credentials
- Daily Host Alerts by User (Last 5 Days): The “Daily Host Alerts by User” table component displays alerts of user activity for the last five days
- CSC - Users with Admin Events (Last 72 Hours): This table presents those users associated with events that indicate performed or attempted administrative actions
- CSF - New Users and User Changes: The User Changes component presents data on new and existing user events on the network over the past 72 hours
- CSF - User Access and Least Privilege Compliance Checks: This component displays user access and least privilege compliance information in areas such as password requirements, lockout policy after failed logins, and controlled use of administrative privileges
- CSF - Access Information and Changes (Last 72 Hours): This matrix component can help an analyst quickly pull up information on systems where certain user access-related events and changes have occurred
- Verizon 2015 DBIR - Suspicious Access Activity: This matrix assists the organization in monitoring for suspicious access activity such as suspicious login activity and spikes in file and web accesses
- Verizon DBIR - Remote Access: The Verizon DBIR notes that it is important to restrict remote access to systems. This matrix assists the organization in monitoring its remote access
- CSF - Wireless Detections: This component presents a breakdown of detected wireless access points, wireless vulnerabilities, and wireless event activity on the network
- CSF - Mobile Devices and Removable Media: This component assists an organization in monitoring mobile devices and removable media
- CSF - Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists
- Network Mapping - Top External-Facing Hosts: This component uses both NNM plugin ID 14 (Accepts external connections) and NNM plugin ID 16 (Outbound external connections) to identify internal hosts participating in connections to systems outside of the internal network
- Account Tracking - Users Talking Externally (Last 72 Hours): This table displays a list of user accounts associated with internal systems that have communicated with hosts outside of the network over the last 72 hours