by Megan Daudelin
September 29, 2015
Discovering mobile devices on a network is a growing challenge. Bring-Your-Own-Device (BYOD) and enterprise mobile device programs are becoming commonplace and the need to manage these devices is increasing with this trend. Mobile Device Management (MDM) solutions are gaining popularity in an attempt to improve the security of mobile device policies. By integrating SecurityCenter with implemented MDM platforms, organizations can more effectively monitor the presence of mobile devices in their network.
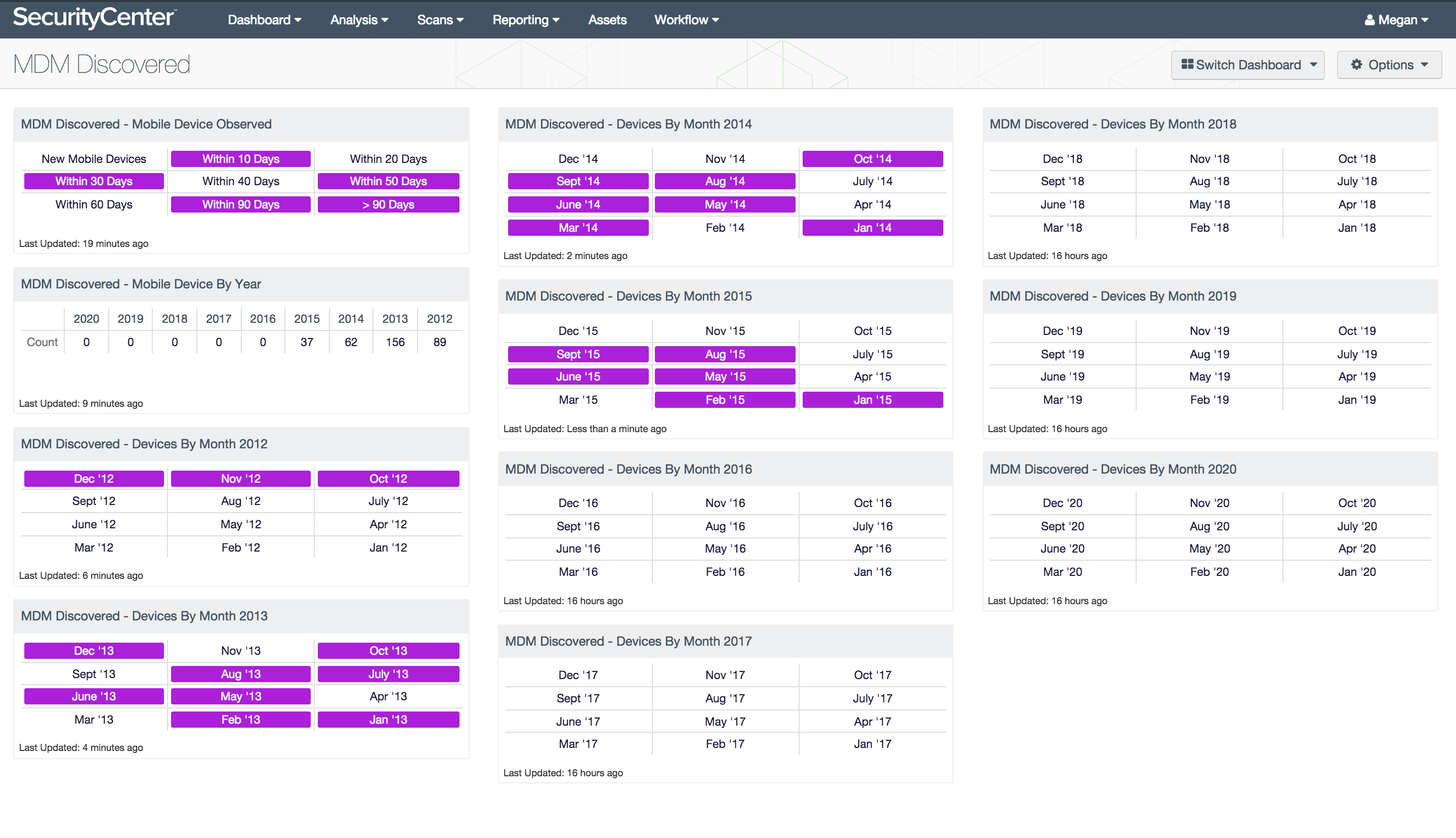
The MDM Discovered dashboard assists security teams in understanding the presence of mobile devices in the network. New devices are tracked by date based on their first connection. A series of indicator components show the discovered dates for devices added by an organization’s MDM solution. Nessus and SecurityCenter support scanning of mobile devices using MDM solutions. The supported MDM solutions are currently Apple Profile Manager, Microsoft ActiveSync, VMWare AirWatch, MobileIron MDM, and Good Technology MDM. This dashboard uses the timestamp found in the plugin output or the “Days Since Observation” to provide a quick and easy understanding of when mobile devices have been discovered by the MDM solution.
The components in this dashboard focus on the timeframe of discovery of mobile devices. Most components are tailored to address one year between 2012 and 2020 and are broken down by month. A purple cell in these matrices indicates that one or more mobile devices were added during that month. Other components show the number of devices added each year and whether any new devices have been added in the past 10 to 90 days in 10 day increments. Security analysts can use these components to identify when mobile devices are added to the network in order to determine whether additional steps or policies regarding mobile devices are necessary.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Discovery & Detection.
The dashboard requirements are:
- SecurityCenter 4.8.2
- Nessus 6.4.3
SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. By integrating with Nessus and an organization’s MDM solution, SecurityCenter CV provides the most comprehensive view of network security data.
This dashboard contains the following components:
- Mobile Device Observed: This component shows all devices discovered by the MDM solution within the defined time period. The indicators start with devices discovered within the last 24 hours, then progress in 10-day intervals. The final cell is an indicator for devices discovered over 90 days ago. Analysts can use this matrix to track which timeframes new mobile devices have been detected during.
- Mobile Device by Year: This component provides a brief indicator summary of mobile devices discovered within each calendar year between 2012 and 2020. Each column shows the count of new mobile device detections during that year. Analysts can use this table to track the rates of new devices being connected by year.
- Devices By Month 2012: This component displays the mobile devices with a timestamp of 2012. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2013: This component displays the mobile devices with a timestamp of 2013. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2014: This component displays the mobile devices with a timestamp of 2014. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2015: This component displays the mobile devices with a timestamp of 2015. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2016: While 2016 is not here quite yet, this component displays the mobile devices with a timestamp of 2016. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2017: While 2017 is not here yet, this component displays the mobile devices with a timestamp of 2017. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2018: While 2018 is not here yet, this component displays the mobile devices with a timestamp of 2018. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2019: While 2019 is not here yet, this component displays the mobile devices with a timestamp of 2019. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.
- Devices By Month 2020: While 2020 is not here yet, this component displays the mobile devices with a timestamp of 2020. Using the “Plugin Output” field, the month and year a device was discovered by the MDM solution is identified. Please note that MDM solutions may interact with this date differently.