by Cody Dumont
June 20, 2016
As organizations continue to face compliance and auditing challenges, many lose track of user activity, privilege changes, and who should have access to what on a network. Having privileged access without the need of elevated privileges, can lead to both unintentional and malicious attacks that could cripple an organization. The ISO/IEC27000 User Access Management dashboard can assist the organization in identifying changes from first time users, expired passwords, disabled accounts, group memberships changes, and more.
The ISO/IEC 27002:2013 framework is a global security standard that provides best practice solutions in support of the controls found in Annex A of ISO/IEC 27001:2013. The framework establishes guidelines and general principles for initiating, implementing, maintaining, and improving Information Security Management Systems (ISMS). Each security control and objective provided within the standard can be tailored to specific business and regulatory objectives while assisting with maintaining overall compliance. This dashboard focuses on the ISO/IEC 27002 9.1, 9.2, 9.3, and 9.4 controls that can help an organization manage and control user access rights and permissions effectively throughout the enterprise.
Many organizations still continue to allow end users to have administrative access, which can place a network at risk for data breaches, malware infections, installation of unauthorized software, and unapproved devices. Internal employees that have administrative rights could gain access to confidential data that they shouldn’t have access to. Some employees may use privileged access maliciously to leak confidential data publicly, which can have negative consequences for an organization.
This dashboard will help to provide insight into user activity, group membership changes, and account status on a network. The Log Correlation Engine (LCE) keeps track of users that have logged into each host, both locally and remotely. Several components within this dashboard can detect accounts that have been locked, disabled, and expired. Nessus scans can detect group membership changes on Windows domains, LDAP, Mac OS X, or local groups. This information can assist analysts in identifying unauthorized users or privilege escalation. LCE also monitors user activity and associate events such as remote connections, file access, and failed logins from specific users. Administrative user events are forwarded to LCE from various network devices, which can help to identify brute force attempts against specific devices and services. Organizations should review user access rights on a regular basis per business requirements. Implementing “least-privilege” practices can aid in reducing overall risk, prevent unauthorized access, and enhance an organization’s security posture.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- LCE 6.0.0
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform. Tenable’s Log Correlation Engine (LCE) performs automatic discovery of users, infrastructure, and vulnerabilities across more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Using Tenable.sc CV, the organization will obtain the most comprehensive and integrated view of its network devices and user activity.
Components
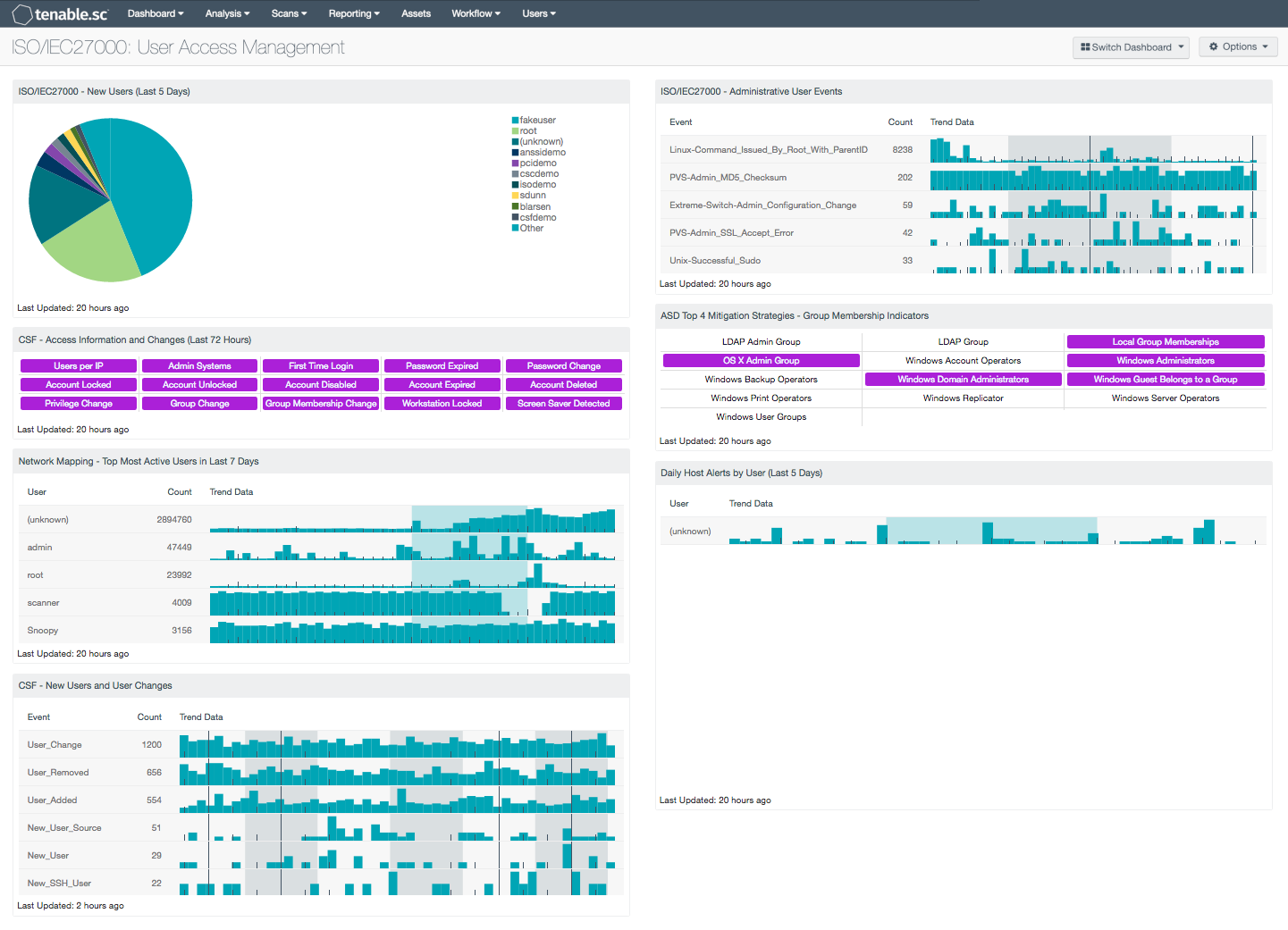
ISO/IEC27000 - New Users (Last 5 Days): This component presents a chart of the top detected new users within the last 5 days. The 'New network user' event records the first time a user is ever seen on the network. The 'New_User' event records the first time a user logs in to a new host and/or a new account type on a host. The analyst should review all new user accounts to determine whether the account is authorized.
CSF - Access Information and Changes (Last 72 Hours): This matrix component can help an analyst quickly pull up information on systems where certain user access-related events and changes have occurred. This includes such information as the first time users logged into a system, and systems on which passwords expired, accounts were disabled, and privileges or group memberships were changed. If an event occurred in the last 72 hours, the indicator will be highlighted purple; an analyst can use this to determine whether an expected behavior such as workstations locking or accounts expiring is happening at all. Clicking on the highlighted indicator will bring up the event analysis screen to display details on the events and allow further investigation. In the analysis screen, setting the tool to IP Summary will display the systems on which the events happened. Setting the tool to Raw Syslog will display the raw syslog of the events, which can give more details. Also, the LCE keeps track of all users that logged into each host and all systems that logged into other systems using administrative accounts; this information is available by clicking on the Users per IP and Admin Systems indicators, respectively.
Network Mapping - Top Most Active Users in Last 7 Days: This table presents the most active users on the network in the last seven days based on the number of network user events generated. The table is sorted so that the user with the highest count of events is at the top. Trend lines of events per user over the last seven days are included. This information can assist an organization in tracking normal activity, as well as discovering any unusual activity. Note that the number of users that the table displays can be adjusted in the component based on the size of the organization, and should typically be 10-15% of the total users on the network.
CSF - New Users and User Changes: This component presents data on new and existing user events on the network over the past 72 hours. The LCE normalized events of ‘User_Added’, ‘User_Change’, ‘User_Removed’ and ‘New_User’ are displayed within this table. These detected event changes will display information on new user accounts, user account password changes, rights access, and new user logins seen for the first time. The data within this component will be highly valuable to any analyst in determining the presence of unauthorized accounts on the network.
ISO/IEC27000 - Administrative User Events: This table presents a list of administrative user events on a network. Administrative events are reported by LCE from various network devices and operating systems. The results are displayed and sorted by count, and uses the Normalized Event Summary tool and filters based on administrative keywords. This component can help to detect potential brute force attempts, and login failures. The analyst can drill down to obtain additional information on each event.
ASD Top 4 Mitigation Strategies - Group Membership Indicators: This Group Membership component is a matrix of saved queries which quickly identifies plugins that match on group membership settings. When a query result is greater than 1, the indicator will turn purple. Plugin ID 45477 defines LDAP Group indicators as a query in remote LDAP for a list of groups. Plugin 71246 connects to a host via SMB and retrieves a list of local Groups and their Members. Plugin 10901 collects the members of the Account Operators group. Members of this group can create or modify local user accounts but cannot modify or create administrative accounts or edit user rights. These are just a few of the indicators in this matrix.
Daily Host Alerts by User (Last 5 Days): Most users in an organization have a typical pattern of when they use an organization’s resources. This component shows when users generate alerts with hosts in the organization. Using this component, analysts can quickly determine user activity outside of expected work hours.