by Cody Dumont
May 23, 2016
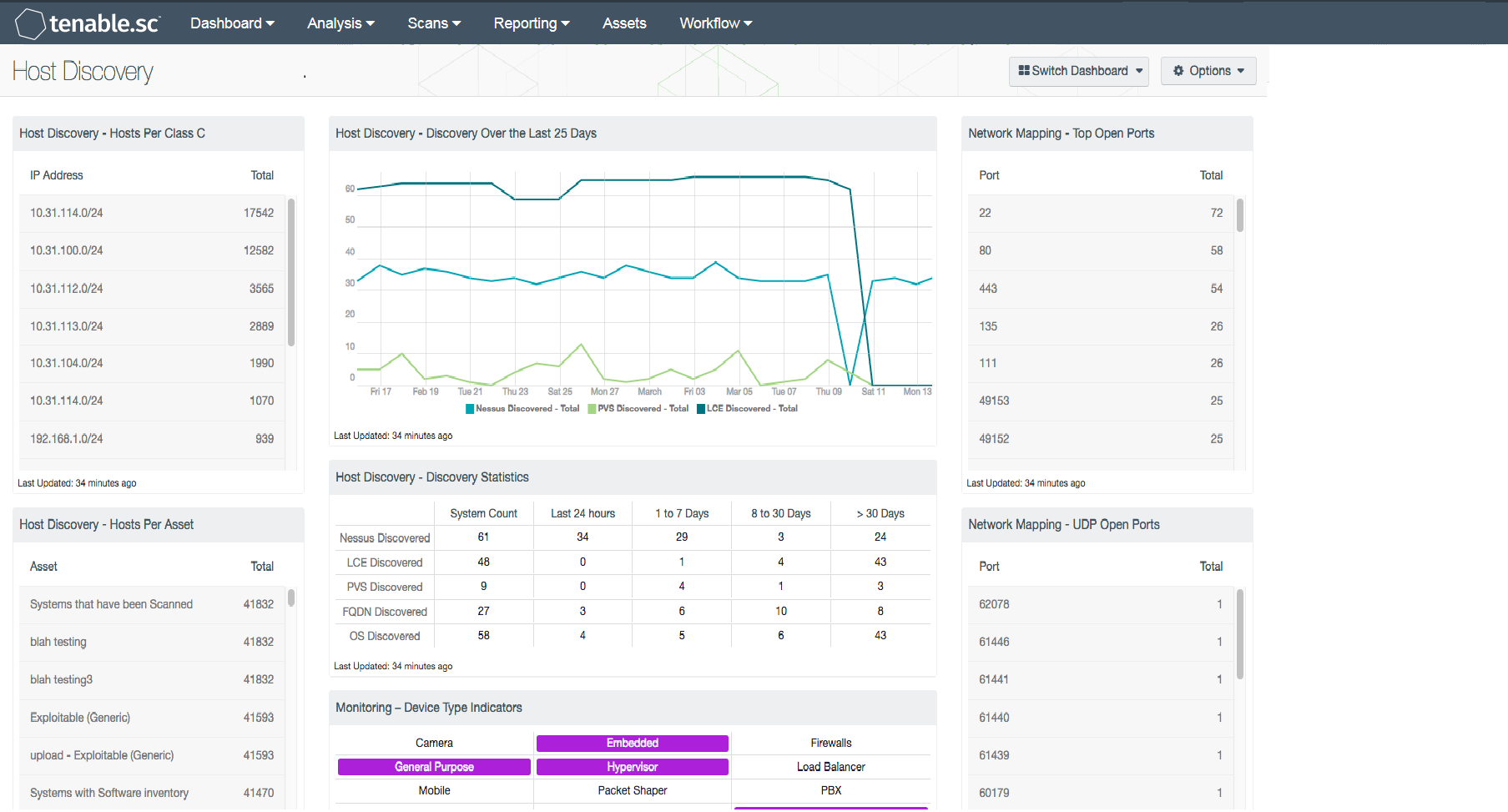
The first step in many security practice guidelines is to identify all the systems on the network. There are several methods to identify hosts, such as port scans, monitoring logs and passively monitoring TCP communications. This dashboard provides an easy method of tracking host counts and detection methods.
Tenable.sc uses active scanning and agent scanning to interactively communicate with targets on the network. Both active scanning and agent scanning use the Tenable Nessus vulnerability scanner to craft packets and send said packets to remote hosts. One of the types of messages that is sent is a Packet Internet Gopher (PING), which uses Internet Control Message Protocol (ICMP) to send an “Echo Request” to a host. The remote host sends an “Echo Reply” for each request received. The content of the echo reply varies based on OS implementation, but the exact same payload must be returned to the host that sent the echo request. The process uses Plugin ID 10180 (Ping the remote host) to discover hosts on the network. A second method uses Plugin ID 19506 (Nessus Scan Information), which contains a summary of the scan parameters, time to complete scan and other useful information. In many cases both plugins 10180 and 19506 will be present, but in some cases 10180 may not be present due to environmental variables. To accurately detect systems discovered using active plugins, ensure both 10180 and 19506 are selected.
Tenable's Tenable.sc Continuous View (Tenable.sc CV) supports active scan data collected using Nessus, but data can also be collected using host data or passive listening. Host data is gathered by the Tenable Log Correlation Engine (LCE) to monitor different data sources such as NetFlow, firewall logs, host logs and other log types of TCP communications. For each TCP communication event discovered that is not related to a TASL event, the IP address from the event is recorded with plugin 800000 (Host Discovered). The discovered IP addresses must be part of the Internal Host setting and any logs must indicate that a connection is established. Passive listening uses the Tenable Nessus Network Monitor (NNM) to detect new devices using plugin 12 (Host TTL Discovered). NNM identifies hosts if they are part of the monitored range configured in NNM and if the IP address is found in either the source or destination field within the IP packet.
Tenable.sc designates several plugins that do not count against licensing. This dashboard brings together all the aforementioned plugins in a way that allows administrators to easily understand and budget for licensing requirements. By allowing customers the opportunity to scan their entire network without impacting their license count, customers can gain a more complete view of their network and scan the most critical systems.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection. The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.4.0
- LCE 6.0.0
- NNM 5.9.0
Using the active scanning, agent scanning, passive listening and host data sensors, Tenable.sc can provide a more comprehensive view of devices accessing the network. By practicing continuous monitoring, organizations can more effectively assess risk and identify authorized and unauthorized systems on their network. As hosts connect to the network, the race begins to identify all the vulnerabilities and assess how each system will affect the network. Only Tenable can automatically analyze information from active scanning, intelligent connectors, agent scanning, passive listening and host data. Active scanning periodically examines hosts to determine the level of risk posed to the organization. Intelligent connectors leverage other security investments in the environment to integrate security data in order to improve context and analysis. Agent scanning provides the ability to rapidly assess hosts without the need for credentials and to detect hosts that were offline during active scans. Passive listening provides real-time monitoring to collect information about hosts connected to the network and how the hosts are communicating. Host data uses logs, file system activity and configuration changes to actively monitor host activities and events in order to identify malicious activity and anomalous behavior.
Components
Host Discovery - Hosts Per Class C: This table displays hosts detected across /24 network blocks using active scanning, passive listening and host data.
Host Discovery - Hosts Per Asset: This table displays the count of hosts detected across the top 50 assets using active scanning, passive listening and host data.
Host Discovery - Discovery Over the Last 25 Days: This chart displays hosts detected over time using active scanning, passive listening, and host data.
Host Discovery - Discovery Statistics: This matrix provides a high-level historic view of when hosts were discovered. Each row depicts a different detection method and each column uses the Vulnerability First Discovered filter to identify when a plugin was first detected. The Vulnerability First Discovered field is set when a plugin, IP address and repository combination is first encountered. This value is reset when a vulnerability is moved from the mitigated database to the cumulative database. Analysts can use this table to gain an understanding of how and when devices are first detected.
Monitoring – Device Type Indicators: This component uses the Device Type plugin and breaks out all the possible device types. Plugin 54615 (Device Type) uses the OS fingerprinting ability in Nessus to define the device type. There are 17 device types that are identified: camera, embedded, firewall, general purpose, hypervisor, load balancer, mobile, packet shaper, PBX, printer, print server, router, SCADA, switch, VPN, webcam, and wireless access point.
Network Mapping - Top Open Ports: This table presents the top ports that were detected to be open by various active scanning techniques. The table is sorted so that the ports with the highest number of detections are at the top. This table displays ports that are detected to be open, not necessarily ports that are being actively used. To reduce the network attack surface, open ports that are not being used should be disabled.
Network Mapping - UDP Open Ports: This table provides a list of UDP ports that are discovered during a UDP port scan. UPD port scans take a long time to complete and are notoriously unreliable, but can provide an idea of the UDP traffic on the network. PCI is a major standard that requires UDP port scans.