by Cesar Navas
July 22, 2015
The UK initially published the 10 Steps to Cyber Security to help organisations reduce threats coming from the Internet. Later in 2014, the UK government and industry developed the Cyber Essentials scheme, which offers a sound foundation to significantly reduce an organisation’s risk profile. This dashboard contains components that will assist organisations reach the stated goals of the Cyber Essentials Scheme.
The UK initially published the 10 Steps to Cyber Security to help organisations reduce threats coming from the Internet. Later in 2014, the UK government and industry developed the Cyber Essentials scheme, which offers a sound foundation to significantly reduce an organisation’s risk profile. This dashboard contains components that will assist organisations reach the stated goals of the Cyber Essentials Scheme. More information can be found here: Cyber Essentials Scheme Requirements
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends.
The dashboard requirements are:
- Tenable.sc 5.0.0.1
- Nessus 8.5.1
- LCE 6.0.0
The Cyber Essentials Scheme provides several requirements that focus on basic cyber hygiene. The Cyber Essentials Scheme consists of 5 critical controls. They are: Boundary firewalls and internet gateways, secure configurations, access control, malware protection, and patch management.
The dashboard addresses each topic in the 5 critical areas of the Cyber Essentials Scheme in the following manner.
Boundary Defense, those devices that are designed to prevent unauthorised access to private networks, should be set up properly and monitored. The objective of the Cyber Essentials Scheme for Boundary Defense states: “Information, applications and computers within the organisation’s internal networks should be protected against unauthorised access and disclosure from the internet, using boundary firewalls, internet gateways or equivalent network devices”. Boundary devices are the first line of defense against outside threats. Monitoring for suspicious activity is critical in eliminating potential threats and risk of compromise. To assist with this step, components are included to display information on the detected bot activity or spikes in connection, authentication failures, and denials.
Computers and network devices should be properly configured to reduce vulnerabilities. The objective of the Cyber Essentials Scheme is for Secure Configurations states: “Computers and network devices should be configured to reduce the level of inherent vulnerabilities and provide only the services required to fulfil their role”. Computers and other devices cannot be considered secure from a typical default installation. By applying simple security controls (system hardening), vulnerabilities can be minimized. Secure Configurations components within this dashboard provide results on reference data from the Cyber Security Framework Protect and Detect Functions, by NIST. These functions provide compliance indications that assist the analyst in configuring systems in the most secure way. This reduces inherent weakness, providing increased protection against attacks.
Controlling user accounts, especially those with elevated access privileges (Administrator Accounts), is a critical function. The objective of the Cyber Essentials Scheme states: “User accounts, particularly those with special access privileges (e.g. administrative accounts) should be assigned only to authorised individuals, managed effectively and provide the minimum level of access to applications, computers and networks”. Many attacks attempt to leverage and exploit privileged accounts. Those privileged accounts that become compromised can result in large-scale corruption of information, and may affect many business processes. Exploited privileged accounts may also go undetected for a significant amount of time. Compromised privileged accounts make it easier for attackers to destroy evidence, cover tracks, and install backdoors or other hidden access points. Protection against user account misuse, restricting access or applying the principle of least privilege should be applied to all accounts. Access Control components present data gathered using references to NIST 800-53 Security Control and Assessment Procedures. Specifically, access control policies AC-3 (Access Enforcement), AC-11 (Session Locks), AC-12 (Session Terminations) and AC-13 (Supervision and Review). Components that provide data based NIST’s Cyber Security Framework Protect Function also include Access Control indications to assist the analyst with tracking access, and monitoring appropriate access levels.
Computers and devices that have access to external resources should be protected from malware. Malware is easily defined as any unwanted software or application that is designed to be harmful or have an adverse affect on a device. The objective of the Cyber Essentials Scheme states: “Computers that are exposed to the internet should be protected against malware infection through the use of malware protection software”. Devices can become vulnerable to malware in a wide variety of methods. Viruses and Trojans are often transmitted via email or websites, where unsuspecting users then download infected files, or open infected email. Malware Protections components of the Cyber Essentials Scheme dashboard display trend analysis of vulnerabilities that can be exploited by malware. Additional malware components track and monitor antivirus deployment, and assist in ensuring malware protection is installed and up to date.
Patches can be upgrades or updates that improve computer software, apply security fixes to correct vulnerabilities, or improve performance or usability. The objective of the Cyber Essentials Scheme states: “Software running on computers and network devices should be kept up-to-date and have the latest security patches installed”. Applying patches and keeping software up to date is critical in maintaining a secure environment. According to the 2015 Verizon DBIR, “99.9% of exploited vulnerabilities had been compromised more than a year after a CVE was published and patched”. Most attacks are designed to take advantage of, and rely upon unpatched systems. Patch Management components of the Cyber Essentials Scheme dashboard assist in ensuring the latest supported versions of vendor patches have been applied. Indications provide a summary of vulnerabilities and patch release dates by severity and exploitability to assist in patching efforts.
The primary objective of the Cyber Essentials Scheme is to make the UK a safer place to conduct business online. This dashboard contains components to assist organisations track and monitor vulnerability status. Active scanning with vulnerability filter references to: NIST 800-53, Cyber Security Framework, ISO/IEC 20071, and others, are utilized to provide these compliance results.
Tenable.sc Continuous View (CV) can assist organisations reach the stated goals of the Cyber Essentials Scheme by monitoring each of the 5 stated critical controls. Additional resources may be added to this collection as needed. The Cyber Security Framework by NIST, Council on Cyber Security Top 20 Critical Controls, and components that support Tenable’s 5 Critical Controls may also be useful additions.
Tenable.sc CV provides continuous network monitoring, identifies vulnerabilities, helps reduce risk, and monitors for compliance. Nessus is the global standard in detecting and assessing network data. The Log Correlation Engine (LCE) performs deep log analysis and correlation to continuously discover and track users, applications, cloud infrastructure, trust relationships, and vulnerabilities.
The Cyber Essentials Scheme dashboard contains the following components:
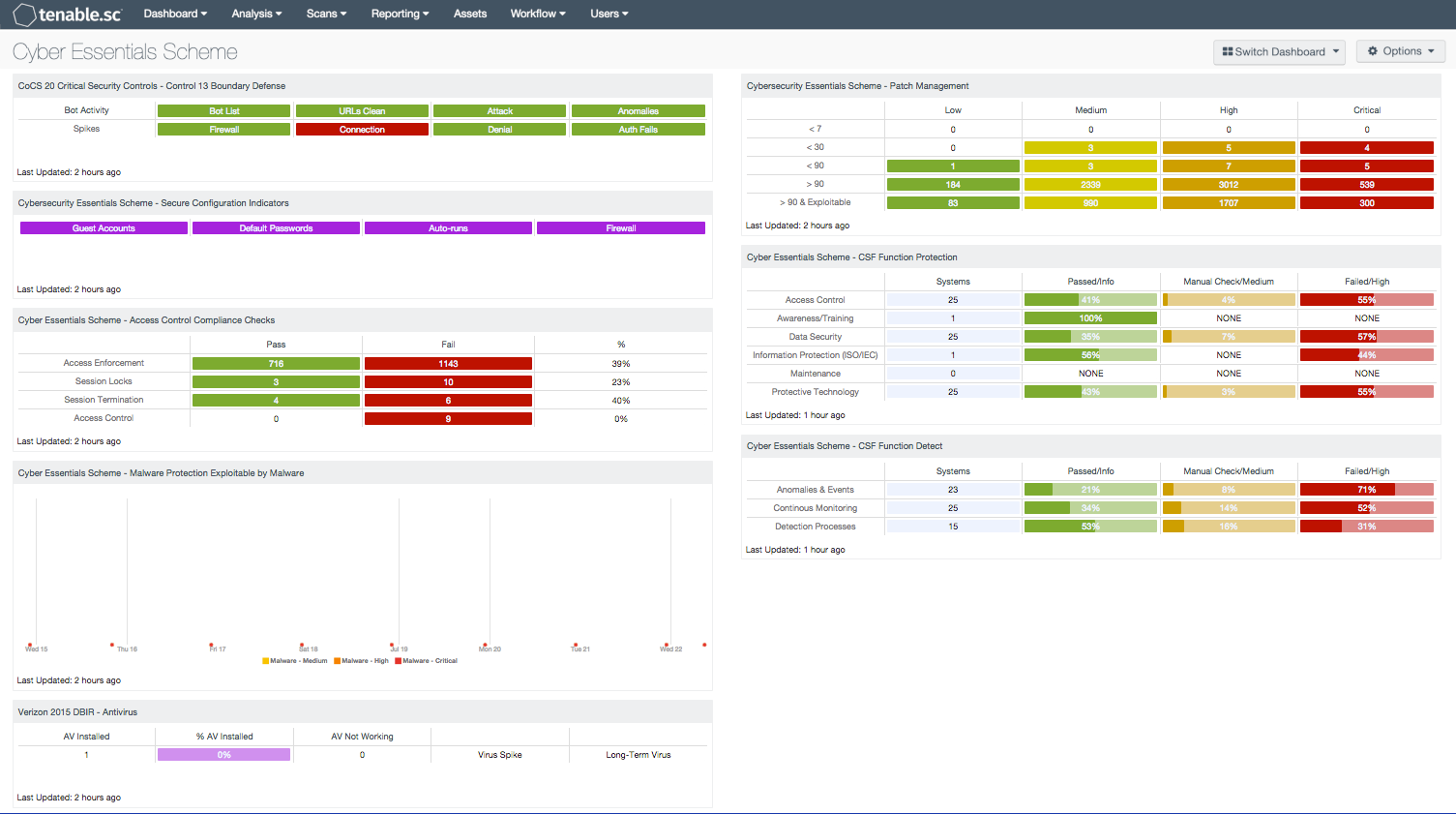
- CoCS 20 Critical Security Controls - Control 13 Boundary Defense - This component assists with the Cyber Essentials Scheme, Boundary Defense requirement. The component displays information on a series of plugins that detect bot activity or spikes in connection, authentication failures, and denials. This component is from the CoCS Top 20 Critical Security Controls – Control 13 – Boundary Defense. Review the CoCS collection for additional components. The component displays data that assists in detecting possible exploits of devices that transfer data across networks with different trust levels. Devices that communicate in such a fashion are likely communicating over the internet through network boundaries.
- Cyber Essentials Scheme - Secure Configuration Indicators - This component assists with the Cyber Essentials Scheme, Secure Configuration requirement. The matrix component provides an indication when guest password, default password, auto-runs, and firewall compliance conditions have failed or require further attention. Indications that are purple could indicate items such as active guest accounts, accounts with defaults passwords still enabled, auto-runs are enabled, firewalls are disabled, firewalls require additional check, or exceptions are found with certain firewall rules.
- Cyber Essentials Scheme - Access Control Compliance Checks - This component assists with the Cyber Essentials Scheme, Access Control requirement. This component displays the number of compliant and non-compliant settings across all systems. The component also calculates a percentage of compliance based on the total number of passing checks divided by the total number of passing and failing checks using NIST 800-53 Security Control and Assessment Procedures. Specifically, access control policies AC-3, AC-11, AC-12 and AC-13. These policies cover the areas of Access Enforcement, Session Lock, Session Termination and the Supervision and Review of Access Control.
- Cyber Essentials Scheme - Malware Protection Exploitable by Malware - This component assists with the Cyber Essentials Scheme, Malware Protection requirement. The component shows an additive trend analysis of vulnerabilities that can be exploited by malware. The additive trend data is displayed for medium, high, and critical severity vulnerabilities for the last 7 days. This trend analysis takes a data point measurement in 24 hour increments. At each data point, the count represents vulnerabilities observed within the preceding 24 hours. From this, management can see the trend on vulnerabilities observed.
- Verizon 2015 DBIR - Antivirus - This component assists with the Cyber Essentials Scheme and Malware Protection requirement. The matrix assists the organisation in monitoring its antivirus deployment. The AV Installed column displays the number of scanned hosts that have AV installed and working properly; the % AV Installed column displays a bar graph of the ratio of systems with AV installed to total systems scanned. The AV Not Working column displays the number of scanned hosts that have AV installed, but it is not working properly or not up to date. The Virus Spike indicator is highlighted in purple if a large spike in virus activity was detected in the last 72 hours. The Long-Term Virus indicator is highlighted purple if in the last 72 hours an IP address has been the source of virus or malware events continuously for more than 20 minutes. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation. Review the Verizon 2015 DBIR Collection for additional components.
- Cyber Essentials Scheme - Patch Management - This component assists with the Cyber Essentials Scheme, Patch Management requirement. The component provides a summary of vulnerabilities and patch release dates. The dates are summarized with 7, 30, 90, more than 90 days and more than 90 days and exploitable. The matrix provides columns for each severity, ranging from low to critical. The low severities are displayed with a green background and white text, and the medium severities are white on yellow. The high and critical severities are orange and red with white text. The results are useful because as stated by the Verizon DBIR 2015 Report, 99.9% of exploited systems had missing patches that were both actively exploitable, and over one year old.
- Cyber Essentials Scheme - CSF Function Protection - This component assists with several Cyber Essentials Scheme requirements, covering the areas of Access Control, Awareness and Training, Data Security, Information Protection Processes and Procedures, Maintenance, and Protective Technology. The component provides a ratio view of systems that have been checked for the Cybersecurity Framework (CSF) function Protect. The ratio bar provides a visual of the number of compliance checks that have either passed, failed, or that require some manual verification. Review the Cybersecurity Framework dashboard, which includes many other components based on Cybersecurity Framework (CSF) functions. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event. Examples of outcome Categories within this Function include: Access Control; Awareness and Training; Data Security; Information Protection Processes and Procedures; Maintenance; and Protective Technology.
- Cyber Essentials Scheme - CSF Function Detection - This component assists with several Cyber Essentials Scheme requirements, Anomalies and Events, Security Continuous Monitoring, and Detection Processes. The component provides a ratio view of systems that have been checked for the Cybersecurity Framework (CSF) function Detect. This component assists with several Cyber Essentials Scheme requirements, Anomalies and Events, Security Continuous Monitoring, and Detection Processes. The component provides a ratio view of systems that have been checked for the Cybersecurity Framework (CSF) function Detect. The ratio bar provides a visual of the number of compliance checks that have either passed, failed, or that require some manual verification. Review the Cybersecurity Framework dashboard, which includes many other components based on Cybersecurity Framework (CSF) functions. CSF Detect Function - Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables timely discovery of cybersecurity events. Examples of outcome Categories within this Function include: Anomalies and Events; Security Continuous Monitoring; and Detection Processes.