by Sharon Everson
July 25, 2017
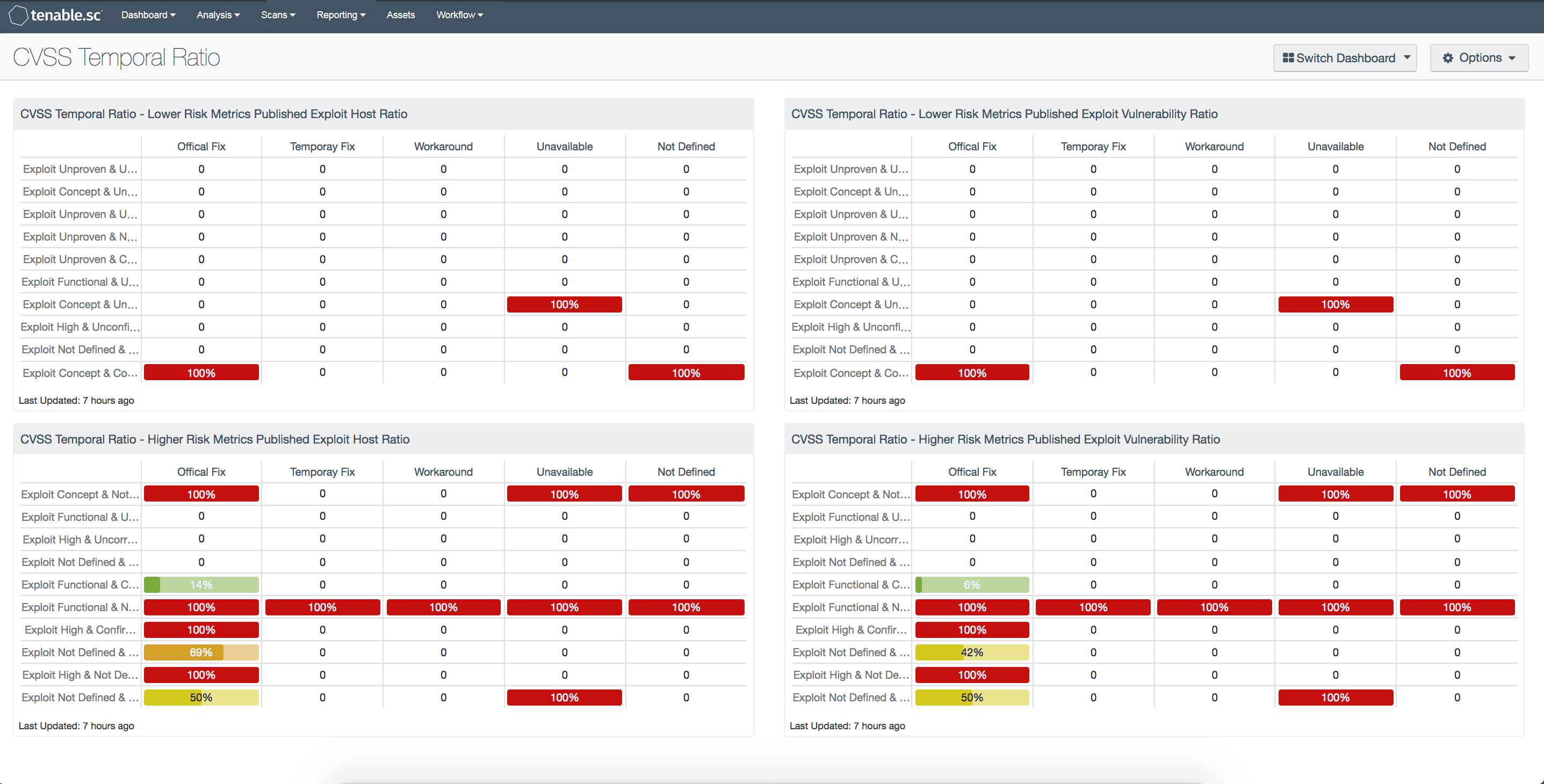
The use of Common Vulnerability Scoring System (CVSS) risk metrics is common and best practice, but it may be difficult to visualize and understand the impact when performing security risk analysis. Temporal metrics change over the lifetime of the vulnerability. The temporal ratio updates as exploits are developed and shared, and as mitigations and fixes are made available. This dashboard is a heat map that displays the vulnerabilities that register if a published exploit is available.
The three metric types of the CV scoring system are Base, Temporal, and Environmental. Temporal metrics along with Environmental metrics modify the Base scoring when calculated. Each of the three Temporal metrics holds the following set of values:
The first metric is “Exploitability”. The exploitability metric represents the current state of exploit techniques and availability of code. As the exploit code becomes easier to use and the number of attackers increase, the severity of the vulnerability also increases. The exploitability metric has five associated values. This first is “Unproven (U)” and means that there no exploit code is available, or an exploit is entirely theoretical. The second is “Proof-of-concept (POC)” and means that the code or technique is not functional in all situations and may require substantial modification by a skilled attacker. The third is “Functional (F)” and means that the code works in most situations where the vulnerability exists. The fourth is “High (H)” and means that the code works in every situation, or the code is actively being delivered via a mobile autonomous agent (such as a worm or virus). The fifth value is “Not Defined (ND)”, which means that assigning this value to the metric will not influence the score. Receiving the ND value is a signal to the equation to skip this metric.
The second metric and primary focus of this dashboard is the “Remediation level.” The remediation level of a vulnerability factors into prioritization. When initially published, a vulnerability is unpatched. During the life cycle of the vulnerability, the remediation level changes to reflect the respective stages. The risk associated with a vulnerability decreases as the vulnerability progresses through its life cycle. The remediation level metric also has five values. The first is “Official Fix (OF)” and means that a complete vendor solution is available. The second is “Temporary Fix (TF)” and means that there is an official but temporary fix available. The third is “Workaround (W)” and means that there is an unofficial, non-vendor solution available. The fourth is “Unavailable (U)” and means that there is either no solution available or that the solution is impossible to apply. The fifth is “Not Defined (ND)”, which means that assigning this value to the metric will not influence the score. Receiving the ND value is a signal to the equation to skip this metric.
The third metric of Temporal metrics is the “Report Confidence (RC).” When a vulnerability is first published, the details may be limited. However, as the vulnerability is confirmed by other researchers or by the vendor, more details may become available. The urgency to mitigate is higher when more details are available. The risk associated with a vulnerability increases as more details are made public and validated by reputable. The “RC metric” is comprised of four values. The first is “Unconfirmed (UC)” and means that there is a single unconfirmed source or possibly multiple conflicting reports. The second is “Uncorroborated (UR)” and means that there are multiple unofficial sources, such as independent security companies or research organizations. The third is “Confirmed (C)” and means that the vulnerability was acknowledged by the vendor or author of the affected technology. The fourth value is “Not Defined (ND)”, which means that assigning this value to the metric will not influence the score. Receiving the ND value is a signal to the equation to skip this metric.
The matrices on the left of the dashboard reflect the host count, while the matrices on the right show the vulnerability count. The matrices with ratio bars also change color based on thresholds with the following percentages that are color coordinated.
- 0% = White
- 1% – 25% = Yellow
- 26% – 50% = Orange
- 51% – 75% = Red
- 76% – 100% = Purple
The dashboard and components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection & Vulnerability Assessment.
The dashboard requirements are:
- Tenable.sc 5.5
- Nessus 8.6.0
- Nessus Network Monitor 5.9.0
- LCE 6.0.0
Tenable's Tenable.sc Continuous View® (Tenable.sc CV™) provides continuous network monitoring, vulnerability identification and security monitoring. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities and new types of regulatory compliance configuration audit files. Tenable continuously analyzes information from our unique sensors, delivering continuous visibility and critical context, and enabling decisive action that transforms a security program from reactive to proactive. Active scanning periodically examines the applications on the systems, the running processes and services, web applications, and configuration settings. Analysts can better asses risk by utilizing standard CVSS metrics in Tenable.sc CV. Tenable enables powerful, yet non-disruptive, continuous monitoring that will provide organizations with the information needed to reduce risk within the enterprise.
The componets with this dashbaord are:
CVSS Temporal Ratio - Lower Risk Metrics Published Exploit Host Ratio: This component displays a table with the exploitable host ratio for the lower range of temporal risk metrics, while maintaining a perpetual risk elevation found in heat maps.
CVSS Temporal Ratio - Higher Risk Metrics Published Exploit Host Ratio: This component displays a table with the exploitable vulnerability ratio for the higher range of temporal risk metrics, while maintaining a perpetual risk elevation found in heat maps.
CVSS Temporal Ratio - Lower Risk Metrics Published Exploit Vulnerability Ratio: This component displays a table with the exploitable vulnerability ratio for the lower range of temporal risk metrics, while maintaining a perpetual risk elevation found in heat maps.
CVSS Temporal Ratio - Higher Risk Metrics Published Exploit Vulnerability Ratio: This component displays a table with the exploitable vulnerability ratio for the higher range of temporal risk metrics, while maintaining a perpetual risk elevation found in heat maps.