by Sharon Everson
July 18, 2017
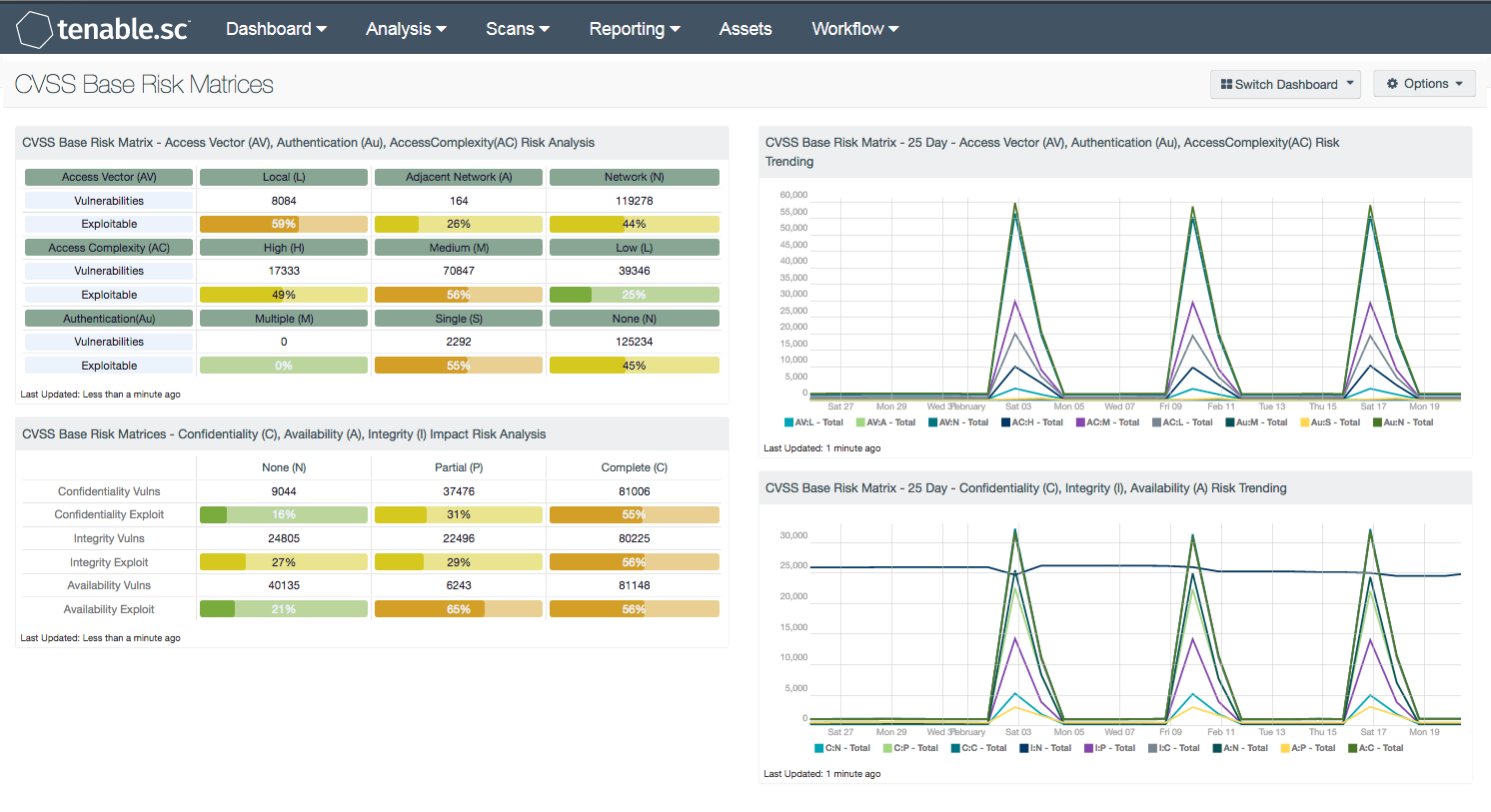
When performing a detailed risk analysis, the use of risk matrices is a common practice. The Forum of Incident Response and Security Teams (FIRST) created the Common Vulnerability Scoring System (CVSS) system to normalize the methodology of analyzing risk. The CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. The CVSS assessment measure three area of concerns: Base Metrics, Temporal Metrics, and Environmental Metrics.
The “Base Metric” is the focus of this dashboard with trending data for the last 25 days. The Base metric group represents the inherent characteristics of a vulnerability that are constant over time and across user environments. Among other parameters, Base scoring is computed from confidentiality, integrity, and availability impact assessments. Base scoring serves as the foundation of the CVSS assessment that is modified by the Temporal and Environmental metrics for a final CVSS risk score. The Base score has the largest bearing on the final score and represents vulnerability severity.
The first three Base metrics for scoring are Access Vector, Access Complexity, and Authentication which measure how the vulnerability is accessed and whether or not special conditions are needed before the vulnerability can be exploited. The last three base metrics are the impact metrics and measure how will be impacted if exploited. The impact is measured in Confidentiality, Integrity, and Availability. Each metric has a value assigned, and reflects how the metric should be attributed. For example, the Access Vector (AV) has three metric values, Local (L), Adjacent Network (A), and Network (N). The value “L” means that local access is required, while the “A” value reflects that an attacker must be in the same broadcast domain to exploit the vulnerability. The N value means that network access is required and is commonly seen in client-side browser exploits, such as Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF).
Information provided by the matrices use the Severity and CVSS_Vector filters. CVSS_Vector is always arranged in the sequential order, using the following sequence:
- Access Vector (AV): [L,A,N]
- Access Complexity (AC):[H,M,L]
- Authentication (Au):[M,S,N]
- Confidentiality (C):[N,P,C]
- Integrity (I):[N,P,C]
- Availability (A):[N,P,C]
The matrices in this dashboard use Vulnerabilities and Exploitable metrics for the finding of the base metric. The Vulnerabilities row shows the vulnerability count found the respective base metric. The Exploitable row shows the percentage of the vulnerabilities that are exploitable. For ease of review, the ratio bar will change colors based on a percentage threshold. The threshold levels are:
- 0% = Green
- 1% – 25% = Yellow
- 26% – 50% = Orange
- 51% – 75% = Red
- 76% – 100% = Purple
The dashboard and components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends.
The dashboard requirements are:
- Tenable.sc 5.5
- Nessus 8.6.0
- Nessus Network Monitor 5.9.0
Tenable's Tenable.sc Continuous View® (Tenable.sc CV™) provides continuous network monitoring, vulnerability identification and security monitoring. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities and new types of regulatory compliance configuration audit files. Tenable constantly analyzes information from our unique sensors, delivering continuous visibility and critical context, and enabling decisive action that transforms a security program from reactive to proactive. Active scanning periodically examines the applications on the systems, the running processes and services, web applications, and configuration settings. Analysts can better assess risk by utilizing standard CVSS metrics in Tenable.sc CV. Tenable enables powerful, yet non-disruptive, continuous monitoring that will provide organizations with the information needed to reduce risk within the enterprise.
Listed below are the components included with this dashboard.
CVSS Base Risk Matrix - Access Vector (AV), Authentication (Au), Access Complexity (AC) Risk Analysis: This matrix uses the Base Metrics: Access Vector (AV), Access Complexity (AC), and Authentication (Au) and whether or not the vulnerability is exploitable or not to aid in the risk analysis process.
CVSS Base Risk Matrix - Confidentiality (C), Availability (A), Integrity (I) Impact Risk Analysis: This matrix uses the Base Metrics: Confidentiality (C), Integrity (I), and Availability (A) and whether or not the vulnerability is exploitable or not to aid in the risk analysis process.
CVSS Base Risk Matrix - 25 Day - Access Vector (AV), Authentication (Au), Access Complexity (AC) Risk Trending: The CVSS Metrics are identified with a metric and a value. This 25-day trend analysis shows the risk trend identified by the CVSS base metric and different values for each metric. Each data point in the trend line calculates the vulnerabilities discovered within the previous 24 hours.
CVSS Base Risk Matrix - 25 Day - Confidentiality (C), Integrity (I), Availability (A) Risk Trending: The CVSS Metrics are identified with a metric and a value. This 25-day trend analysis shows the risk trend identified by the CVSS base metric and different values for each metric. Each data point in the trend line calculates the vulnerabilities discovered within the previous 24 hours.