by Stephanie Dunn
February 26, 2016
More organizations today are implementing remote access technologies, which allow employees to access network resources from virtually any device anywhere. However, ensuring the security of remote access technology can be a challenging task for any organization to undertake. This dashboard aligns with the NIST Cybersecurity Framework (CSF) PR.AC-3 and PR.MA-2 subcategories that allow an organization to monitor remote desktop and VPN network connections.
The CSF provides guidance based on existing standards, guidelines, and practices that can be tailored to specific organizational needs. This dashboard utilizes the Access Control and Maintenance subcategories within the CSF Protect category, which assists in monitoring remote access connections, status of remote access services, and monitor for unauthorized connections.
Many organizations have expanded remote access capabilities to include VPN devices and remote desktop services for their mobile workforce. Some organizations allow users to connect remotely using personal devices from various outside networks. However remote access may pose a security risk as many systems lack proper security updates, and have malware installed that could compromise internal resources. This dashboard provides a comprehensive view of activity from VPN and remote desktop events. The analyst can use this information to detect suspicious events or unauthorized users.
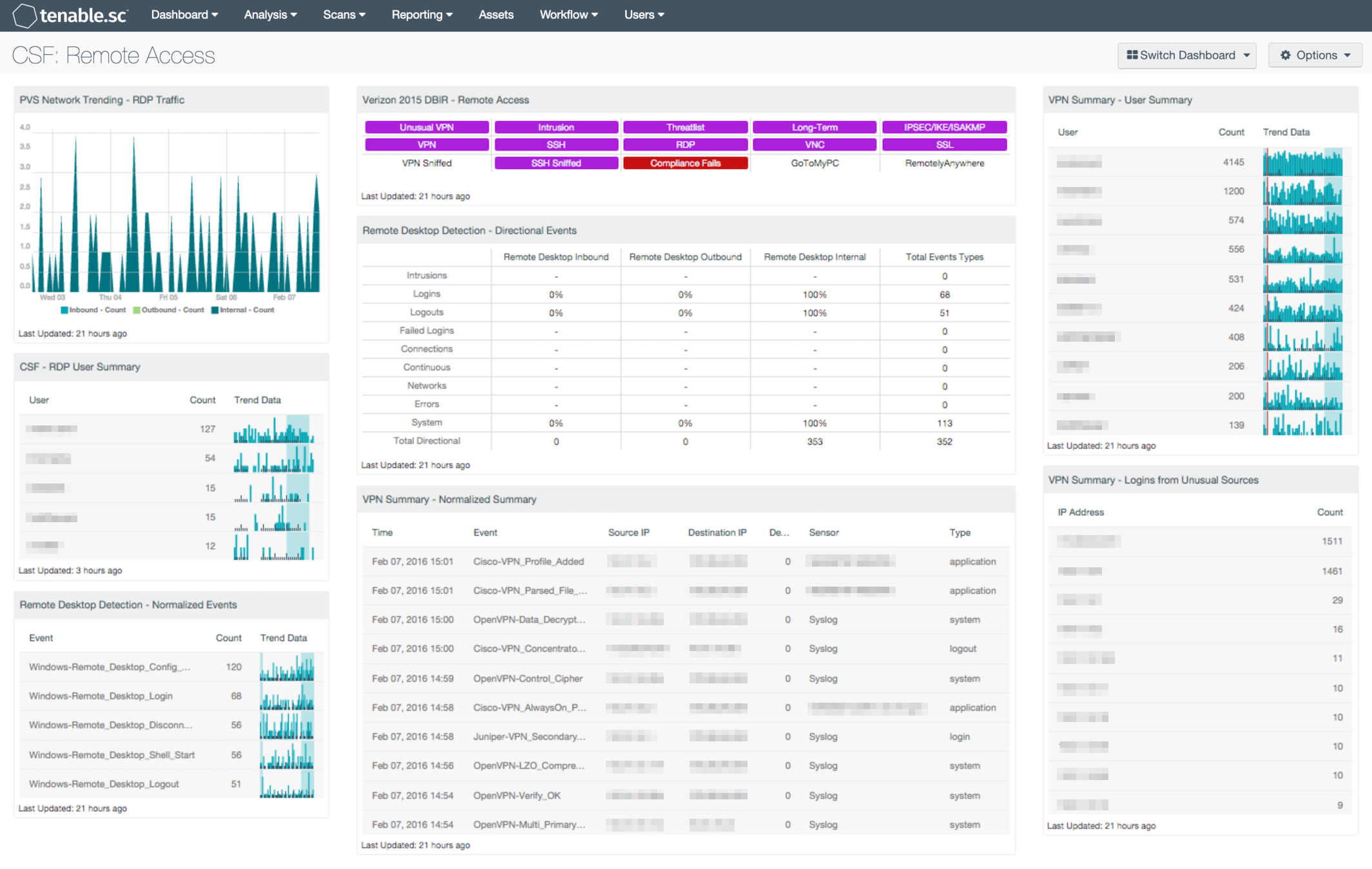
Trends in remote desktop traffic present details on internal traffic, as well as inbound and outbound traffic. Remote desktop users and sessions can be easily identified using remote desktop-based normalized events. Indicators that highlight traffic events, threat-list activity, and detect the presence of remote access protocols are included. A summary of VPN events, VPN user activity, and logins from unusual sources can assist the analyst in detecting possible breaches, attacks, and activity from unauthorized users. The analyst should review both remote desktop, and VPN activity further, as security configurations can vary among organizations. Security teams can utilize the information provided within this dashboard to identify and remediate any security gaps within remote desktop services and VPN devices.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.5.0
- LCE 6.0.0
- NNM 5.9.0
Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable’s nessus Network Monitor (NNM), as well as log correlation with Tenable’s Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of remote access users and events across the network.
This dashboard contains the following components:
- NNM Network Trending – RDP Traffic: LCE provides a trending view of the RDP traffic discovered by the NNM nodes on the network. Traffic is identified in the following three methods. The first is traffic from IP addresses considered external to your network, going to addresses that are internal to your network. The next way that traffic is identified is by traffic from IP addresses considered internal to your network, going to addresses that are external to your network. Lastly, internal traffic is identified by traffic between IP addresses that are considered internal.
- CSF – RDP User Summary: This component presents a list of active Remote Desktop Users, along with associated counts and trend data over the past 7 days. Remote Desktop sessions are detected utilizing Remote Desktop normalized events. Trend data will allow the analyst to drill down and obtain additional information on remote desktop sessions by user, IP addresses, and session status information.
- Remote Desktop Detection – Normalized Events: Analyzing both the normalized event and the trending of these events will help SC CV users understand Remote Desktop (RDP) activity on the network and detect anomalies. This component displays normalized events from SC CV over the past seven days. The fields displayed are: normalized events names, total events, and a trend graph for events collected over the past 7 days.
- Verizon 2015 DBIR – Remote Access: The Verizon DBIR notes that it is important to restrict remote access to systems. This matrix assists the organization in monitoring its remote access. The Unusual VPN indicator is highlighted purple when a VPN login originates from an IP address that is not normal for the user ID. Multiple indicators highlight VPN, SSH, RDP, VNC, and SSL traffic events within the last 72 hours, including potential intrusion events, events associated with known bad IP addresses (threatlist), and long-term events. The VPN Sniffed and SSH Sniffed indicators are highlighted purple if those protocols, respectively, are passively detected on the network. The Compliance Fails indicator is highlighted red if there are any remote access compliance failures. The GoToMyPC and RemotelyAnywhere indicators are highlighted purple if those applications are detected on the network. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation.
- Remote Desktop Detection – Directional Events: Understanding the normal network traffic flow and the direction of Remote Desktop (RDP) communications allows for anomaly analysis and increases the likelihood of breach detection. This component provides a table of RDP network traffic directional flow by nine event types. The event types used are: Intrusion, Login, Logout, Failed Login, Connection, Continuous, Networks, Errors, and System. Tenable.sc Continuous View defines network traffic flow as internal, inbound and outbound. The Total Event Types column displays a count of all of the respective events, while the remaining three columns show the percentage of events according to directional flow.
- VPN Summary – Normalized Summary: This table component presents the analyst with a list of triggered events sorted by time, for the last 7 days. Events that occurred most recently will be listed at the top of the table; the last 50 will be shown. This table is useful to the analyst to see what VPN are currently being triggered in the environment. The update frequency of this table is set to one hour; therefor this table will update results every hour. This update frequency can be altered to a frequency from as small as 15 minutes to a specific day within a month. The table utilized a List of Event tool, with the Normalized Event filter of *VPN* and timeframe set to 7 days.
- VPN Summary – User Summary: This table component presents the analyst with a User Summary of '*VPN*' events over the last 7 days. The top 50 results are displayed, sorted by count, and presents both the user and trend data. This component is included in dashboards related to the 2015 Verizon Data Breach Investigation Report (DBIR).
- VPN Summary – Logins from Unusual Sources: This table presents event data from the Tenable Log Correlation engine's VPN_Login_From_Unusual_Source event where the LCE has seen a VPN authentication occur from a source that is not normal for the user ID. Once the LCE determines a users 'Normal Source', it will alert on any unusual sources of logins for that user. By default, the triggered event occurs if the normal source and the new source are not part of the same class B. This table presents the IP address and number of events for the reported IP address over 90 days. This component is included in dashboards related to the 2015 Verizon Data Breach Investigation Report (DBIR).