by Stephanie Dunn
February 26, 2016
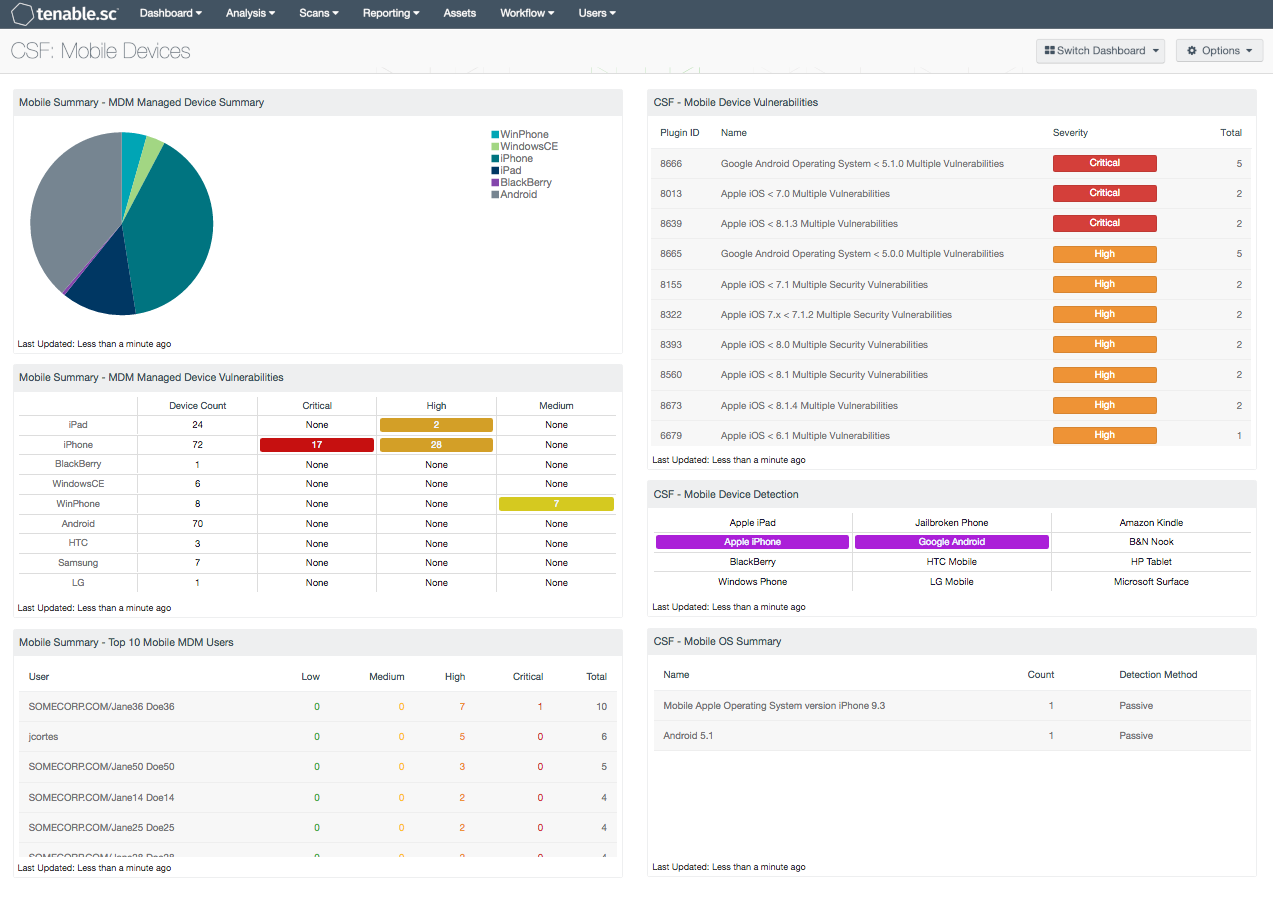
Mobility demands have placed a need for organizations to adopt Mobile Device Management (MDM) solutions to manage and track mobile devices within the enterprise. Mobile devices have also presented major security risks, as many organizations allow unmanaged personal devices that may have outdated operating systems and other security vulnerabilities. This dashboard aligns with the NIST Cybersecurity Framework (CSF) PR.AC-3 subcategories that will assist organizations in monitoring MDM device changes, along with tracking personal mobile devices on the network.
The CSF provides guidance based on existing standards, guidelines, and practices that can be tailored to specific organizational needs. This dashboard utilizes the Access Control subcategory within the CSF Protect function, which can assist organizations with identifying both MDM and BYOD detected devices.
This dashboard can assist organizations with managing mobile devices detected by MDM servers, as well as unmanaged personal mobile devices. Tenable supports MDM solutions such as Apple Profile Manager, Microsoft ActiveSync, VMWare AirWatch, MobileIron MDM, and Good Technology MDM. A summary of managed MDM devices allow the analyst to drill down, and obtain additional information on the mobile device. This can be useful for inventory tracking and end-of-life purposes. Device vulnerabilities that are detected by MDM servers are included. When vulnerability is detected on a device, the severity indicator will change color. Users are also tracked based on mobile devices within an MDM server. Several components provide details on mobile operating systems and vulnerabilities, which can assist the analyst in identifying outdated mobile devices that need to be patched. Included mobile device types such as mobile phones, tablets, and jailbroken devices will alert the analyst to any unauthorized mobile devices connected to the network.
Organizations can face a wide variety of security issues when dealing with mobile devices. MDM solutions provide simplified administration and security when managing corporate mobile devices. Mobile applications, security updates, and OS upgrades can be pushed to devices remotely from MDM servers, as well as wiping devices that have been lost or stolen. Many organizations allow employee-owned mobile devices on the network for both personal and professional use to connect to corporate e-mail, VPN, and internal websites. However, allowing employee-owned mobile devices on the network can present security risks from outdated operating systems, software apps, and lack of security controls. Security breaches can also happen if an employee’s personal mobile device is lost or stolen. Additional threats such malicious e-mail links, unauthorized apps, and vulnerable services can easily compromise sensitive data. Organizations should implement appropriate safeguards and policies to protect sensitive data from the security risks associated with personal mobile devices.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.5.0
- LCE 6.0.0
- Mobile Data
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. By integrating with Nessus and an organization’s MDM solution, Tenable.sc CV provides the most comprehensive view of both managed and unmanaged mobile devices.
This dashboard contains the following components:
- Mobile Summary – MDM Managed Device Summary: This component provides a model summary of the managed devices by an MDM server. Using the 'Model Summary' tool and sorting devices based on the Model column, the device count is used to create a pie chart that is easy to read and understand. The analyst can drill down to obtain information on device type, serial number, model, device version, timestamp and more.
- Mobile Summary – MDM Managed Device Vulnerabilities: This component contains a list of managed mobile devices, along with detected vulnerabilities by critical, high, and medium severity levels. The basis of each cell query within the matrix is the 'Model' type. Please note that this field is case sensitive. As an example, if the model type is set to 'ipad', the returned result will be 0. To ensure the correct values are displayed, use the Analysis > Mobile > Model Summary to view the current device models present. When device models use a common OS over several platforms (for example, Android), an additional filter can be used. This component illustrates this functionality by combining the 'Model' and 'Serial Number' fields. The HTC devices have HTC as the serial number prefix, while Samsung has SAMSUNG. This allows the component to display a more granular data view. However, all Android-based devices do not follow this pattern. Therefore the 'Android' row uses only the 'Model' field as the filter.
- Mobile Summary – Top 10 Mobile MDM Users: This component contains a table listing users with the most mobile devices registered to an MDM server. The table is based on the 'User Summary' tool, and displays the top 10 users based on the total number of mobile devices. The sort column is based on the device total count and is sorted in descending order. The user, low, medium, high, critical, and total columns are displayed.
- CSF – Mobile Device Vulnerabilities: This component displays a list of existing vulnerabilities on mobile devices that are not managed by a Mobile Device Management (MDM) server. Any unmanaged mobile device can present serious security risks to an organization’s network. Outdated mobile operating systems can be full of security vulnerabilities that can expose a network to serious risks. The table is sorted by severity, and present details on the vulnerability and total number of devices affected. Data provided within this component can assist the analyst in adjusting security policies regarding unmanaged mobile devices that can aid in mitigating security risks.
- CSF – Mobile Device Detection: This component displays a list of detected mobile devices that are not managed by a Mobile Device Management (MDM) server. Any unmanaged mobile device can present serious security risks to an organization’s network. Several mobile phone types, jailbroken devices, and tablets are included. The indicator will turn purple once a device is detected. The analyst can click on the highlighted indicator to obtain information about the mobile device. This information can also assist organizations in adjusting security and device blocking policies regarding unmanaged mobile devices.
- CSF – Mobile OS Summary: This component displays a list of detected mobile operating systems (OS) on mobile devices that are not managed by a Mobile Device Management (MDM) server. Outdated mobile operating systems contain vulnerabilities that can pose a significant risk to an organization’s network. Data provided within this table can assist the analyst in detecting outdated mobile devices that need to be patched.