by Stephanie Dunn
February 26, 2016
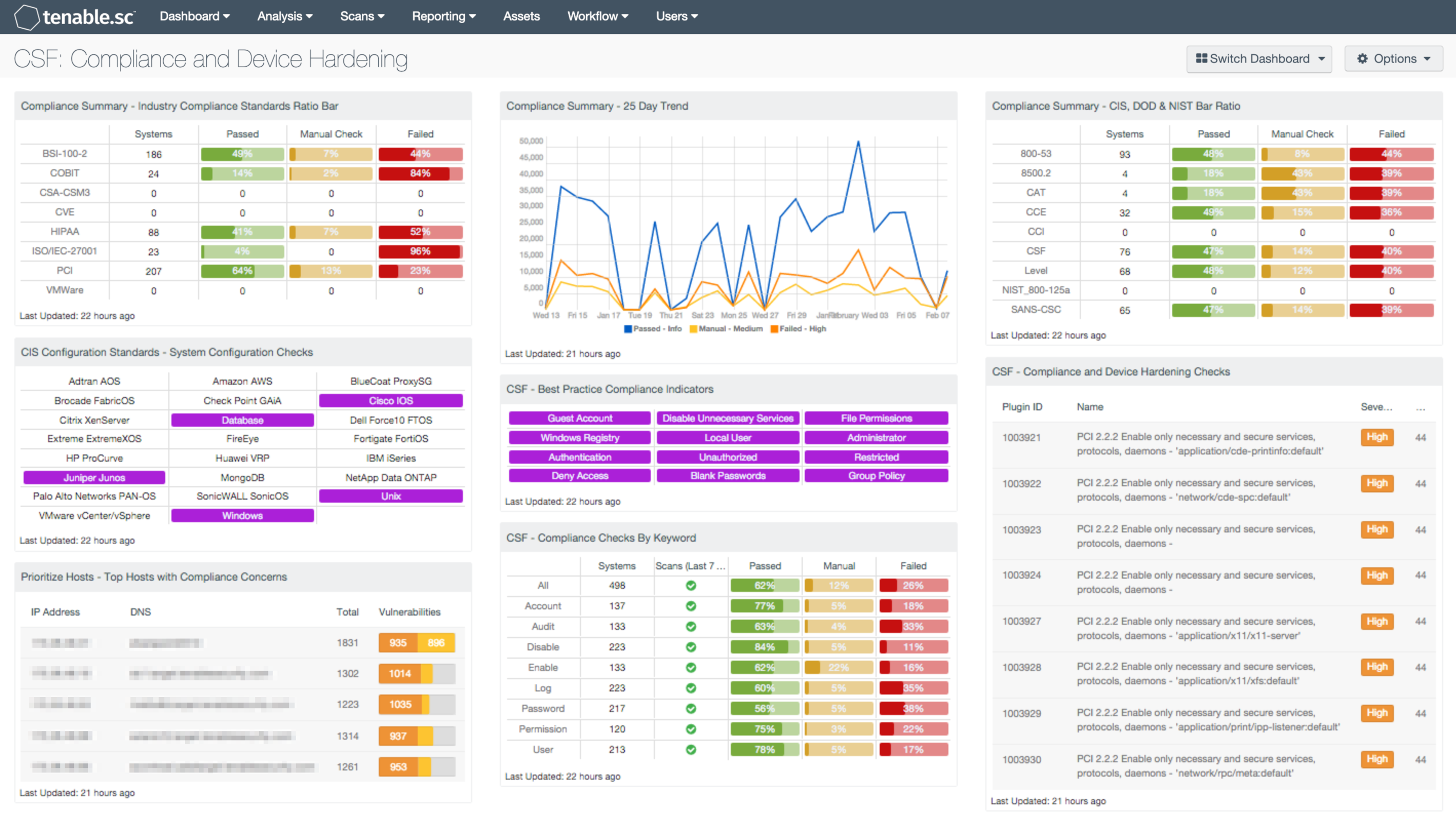
Compliance and regulatory changes can be challenging for any organization to manage effectively. Not only do organizations have to keep systems updated with the latest patches, systems also need to be hardened to reduce the attack surface. This dashboard aligns with the NIST Cybersecurity Framework (CSF) PR.IP-1, PR.IP-7 and ID.GV-3 subcategories, which provide a series of system configuration, compliance, and device hardening checks, along with specific industry standards and regulation checks.
The CSF provides guidance based on existing standards, guidelines, and practices that can be tailored to specific organizational needs. Multiple subcategories within the CSF address configuration management and configuration hardening practices. This dashboard can assist the organization in providing compliance and device hardening checks across various compliance standards and systems on a network. Several components will provide the analyst with targeted information on hosts, subnets, and device types. A trend chart displaying an analysis of new compliance checks observed daily is also included. The analyst can utilize the data to obtain specific compliance information on hosts, and apply hardening techniques to reduce the overall attack surface.
Many organizations are required to comply with various compliance standards and guidelines. Along with patching systems, many have implemented hardening techniques as a requirement of compliance. Servers, network devices, and workstations are all top targets for attackers to gain access to a network. Additionally, virtually all devices have default security configurations setup within every operating system that can make network systems vulnerable to attacks.
Hardening systems will remove access to unnecessary services, software, and users, which ensures the security of network systems. Examples of hardening techniques can include disabling unneeded user accounts and services, implementing screen saver locks, using strong passwords, auditing logs, and more.
Nessus uses a wide variety of compliance and audit policies that can be leveraged to check systems against multiple industry standards and guidelines. Organizations that utilize this dashboard should consult with their security teams to determine appropriate policies based on organizational and compliance requirements.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.5.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network vulnerabilities and compliance status.
The following components are included in this dashboard:
- Compliance Summary - Industry Compliance Standards Ratio Bar: This component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are BSI, COBIT, CCM, CVE, HIPAA, ISO, PCI & VMWare. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
- CIS Configuration Standards - System Configuration Checks: This component provides indicators for CIS audits based on the device audited. The indicators search on two fields, the Cross Reference and vulnerability text. The Cross Reference uses the audit file keyword search, while the plugin text searches for “cisecurity.org”. These indicators will show the analysts which type of CIS audits have been run and provide an easy method for accessing CIS audit data. The indicators will turn purple when a match is discovered.
- Prioritize Hosts - Top Hosts with Compliance Concerns: This table displays the top hosts on the network that have either compliance failures or compliance checks that must be performed manually. The list is sorted so that the host with the worst compliance concerns is at the top. A count of compliance concerns and a bar graph indicating the severity of the concerns are given for each host. Use this table to determine the hosts most out of compliance on the network.
- Compliance Summary - 25 Day Trend: This component provides a 25-day trend analysis for all compliance checks. The data points for are calculated using the 'Days Since Observation' set to 'within the last day'. Thus, each data point only calculates the new compliance checks observed daily. The resulting graph more accurately depicts the change in compliance over the period of 25 days.
- CSF - Best Practice Compliance Indicators: This component uses results from the compliance audit to trigger on specific plugin keywords for best practice configuration guidelines. When the keyword or phrase has been detected within the plugin name, the indicator will turn purple. The analyst can click on the indicator and drill down to obtain additional information on hosts affected. This matrix will allow the analyst to readily identify specific compliance best practice keywords, and can be modified to suit organizational needs.
- CSF - Compliance Checks by Keyword: This component uses results from the compliance audit to trigger on specific plugin keywords. Each column includes the respective keyword along with the host count, scans performed in the last 7 days, and whether the checks have passed, failed, or require manual verification. Passed checks are green, failed are red, and checks that require manual verification are in orange. This component will allow the analyst to readily identify specific compliance vulnerabilities. The keywords can be modified to suit organizational needs.
- Compliance Summary - CIS, DOD & NIST Bar Ratio: This component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are: NIST, DoD, CCE, CCI, CSF, & CSC. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
- CSF - Compliance and Device Hardening Checks: This component displays Compliance and Device Hardening Checks from the NIST CSF PR.IP-1 and PR.IP-7 sub-categories. Additional references from other compliance related standards such as NIST CM-2 through CM-7, CM-9, CA-7, PCI DSS 2.1 and 2.2, and the COBIT BAI10 process are also included. Each check will search for vulnerability text that includes each of the respective guidelines and standards noted above. The table will display the plugin name, along with the number of hosts affected, and is sorted by severity level. The analyst can drill down to obtain additional information on specific vulnerabilities, hosts affected, and solutions to mitigate the vulnerability. This information can assist the analyst in patching a large number of hosts at once, which will reduce the overall risk footprint.