by Stephanie Dunn
February 26, 2016
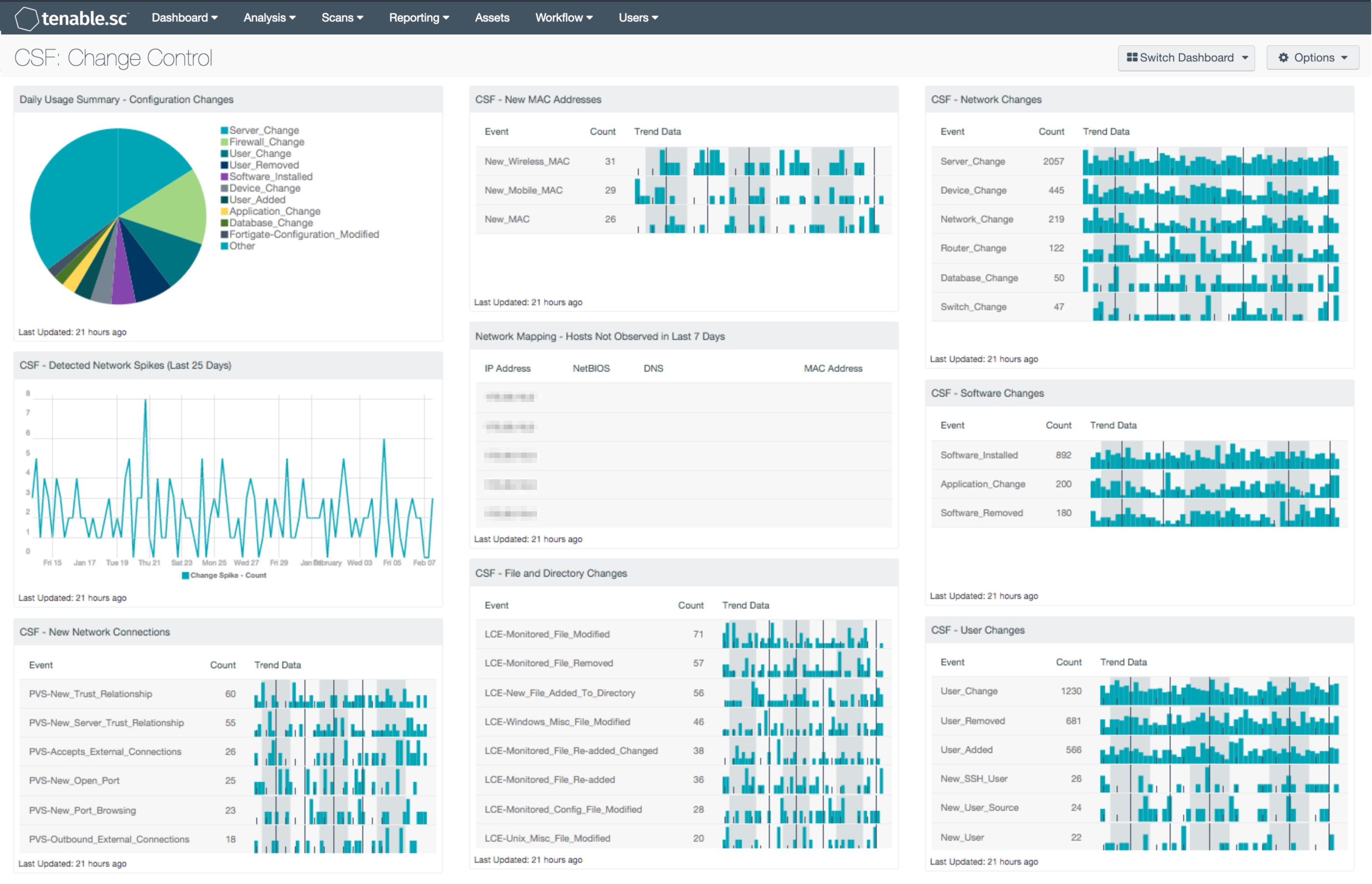
Changes are a part of the dynamic nature of networks that are continually being made to keep up with business demands. However, the lack of a proper change control process can be a costly expense that can lead to network outages, along with devices and servers being compromised. The Change Control Dashboard can assist the organization by detecting changes on servers, infrastructure devices, users, software and more.
The Cybersecurity Framework (CSF) provides guidance based on existing standards, guidelines, and practices that can be tailored to specific organizational needs. One of the five categories within the CSF is “Protect”. This category is divided into multiple subcategories that address specific security requirements of Access Control, Awareness, Data Security, Policies and Procedures, Maintenance, and Technology Protection. The Information Protection Processes and Procedures category (PR.IP) provides guidance on security policies, processes, and procedures to maintain and protect information system assets. This dashboard focuses on the PR.IP-3 subcategory within the CSF, which identifies configuration changes on the network, and can bridge the gap with change control management.
Change Control is a process to help ensure that no unnecessary or unauthorized changes are made. This process ensures that a device, application, or service is properly tested, and approved before being deployed. Manual changes to a network device or server, such as software updates or policy changes, can inadvertently cause network outages. Many of the changes are often made without knowledge, formal risk assessment, or management approval. Lack of communication between security teams, locations, and other groups is common, but can be avoided to prevent costly mistakes.
The components within this dashboard can ease the complexities associated with change control, by providing information on a variety of network event changes. Increases in network spikes can interfere with network resources and indicate potential malicious activity. Another important aspect of change control is maintaining an inventory of existing and newly detected devices. Along with physical and virtual hosts, wireless and mobile devices detected by MAC address are included. This will identify authorized devices that have been moved, changed, or decommissioned. Changes with ports, trust relationships, and new external connections can uncover malicious addresses attempting to connect to the network. Tenable.sc Continuous View (CV) can detect changes by monitoring LCE and syslog events across multiple devices, servers, and databases, which provides complete visibility and accountability of network changes. PVS can alert the analyst in real-time when new hosts, devices, and events are discovered. When combined, the components will allow organizations to answer who, what, when, and where changes were made.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment . The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.5.0
- LCE 6.0.0
- NNM 5.9.0
Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable’s Nessus Network Monitor (NNM), as well as log correlation with Tenable’s Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network changes.
The following components are included in this dashboard:
- Daily Usage Summary - Configuration Changes: This component collects the top 10 configuration changes. Adding a new user account into Windows, changing a firewall rule, or installing new software may generate these events. Networks are always evolving and constantly require changes. Tenable.sc Continuous View (Tenable.sc CV) customers can detect these changes by monitoring LCE and syslog events. PVS can alert in real-time when new hosts are discovered. This component refreshes hourly and should be monitored throughout the workday.
- CSF - Detected Network Spikes (Last 25 Days): This chart utilizes the ‘Statistics-Detected_Change_Large_Anomaly’ normalized event, which detects anomalous network spikes. The LCE stats daemon has found a detected-change type event spike. Events of this type are being sent to the LCE stats daemon, and are comparing this hour's event rate for each unique targeted IP address to the same hour in each previous day for the entire body of collected data. Any large changes in event rates can indicate new types of software installations, patching, or can indicate instances of malicious activity on the network.
- CSF - New Network Connections: This table presents a list of new network connections discovered by PVS and logged by LCE. Events displayed within this table present information on new trust relationships, internet connections, newly opened ports, and external connections. The analyst can drill down and select the syslog events to obtain additional information on a detected event. Uncovering new network connections can assist with detecting rogue and unauthorized connections on a network.
- CSF - New MAC Addresses: This table detects new MAC addresses from workstations, servers, mobile, and wireless devices that were first observed in the last 72 hours. LCE utilizes the ‘New_MAC’, ‘New_Wireless_MAC’, and ‘New_Mobile_MAC’ normalized events when a new, never-before-seen MAC address is observed on the network. Each event displays the time observed, IP address, MAC address, and the raw syslog text. Discovering new hosts on the network can assist an organization in maintaining an accurate inventory and detecting rogue devices.
- Network Mapping - Hosts Not Observed in Last 7 Days: This table lists those systems that were last passively observed on the network more than seven days ago. Tenable's PVS detects hosts on the network and records their last observed date. This table presents host information for any hosts whose last observed date is more than seven days ago. Discovering hosts that have stopped talking on the network can assist an organization in maintaining an accurate inventory and detecting unusual activity.
- CSF - File and Directory Changes: This table detects file changes or modification events collected from systems with LCE Clients installed, or from systems where syslogs are collected. The component leverages several normalized event types as well as the 'detected-change' event type over the last 72 hours. LCE Clients will detect files that have been modified, removed, added, re-added, and monitored. This table can provide valuable data to assist with change management policies, and discover unauthorized changes to files on the network.
- CSF - Network Changes: This component displays a list of network changes over the last 72 hours. There are several normalized event types presented that detect changes from servers, database, and infrastructure devices. Many of these detected changes are additions to the network, such as new hosts, new software, policy and security settings changes, and new open ports. Any new additions or changes should be investigated to determine if they are authorized. To obtain additional information, the analyst can click on any of the normalized events.
- CSF - Software Changes: This component displays a list of software and application changes over the last 72 hours. LCE will detect any software changes utilizing the ‘Software_Installed’, ‘Application_Change’, and ‘Software Removed’ normalized events. These changes detect software installations, updates, and removals through various operating system methods. The analyst can drill down to obtain additional information on the presence of authorized or unauthorized software on the network.
- CSF - User Changes: This component presents data on new and existing user events on the network over the past 72 hours. The LCE normalized events of ‘User_Added’, ‘User_Change’, ‘User_Removed’ and ‘New_User’ are displayed within this table. These detected event changes will display information on new user accounts, user account password changes, rights access, and new user logins seen for the first time. The data within this component will be highly valuable to any analyst in determining the presence of unauthorized accounts on the network.