by Josef Weiss
May 7, 2014
Today's organizations are increasingly making use of cloud-based services such as file storage and sharing in their normal operations. Using cloud-based file storage services such as Dropbox, OneDrive, and iCloud requires less infrastructure and maintenance and can result in cost savings for the organization. However, by using these cloud services, the organization gives up visibility and control. What vulnerabilities do cloud-based applications have? How are credentials managed? Is the organization's data encrypted and isolated from other users of the file storage service? What about availability and redundancy?
The increased use of cloud-based file storage may lead to data security, availability, and access control issues. An organization should make an informed decision when moving services to the cloud. The organization should also then be able to track and monitor the cloud services being used and discover if any unauthorized cloud service interactions are occurring.
This dashboard presents detections of network interactions with cloud-based file storage and sharing services. These cloud service interactions are detected primarily through passive traffic analysis or via logged events, although some are also detected through active scans. The dashboard also presents information on SSL sessions involving cloud-based file storage services. This dashboard can help an organization understand and monitor interactions with cloud-based file storage services.
This dashboard is available in the Tenable.sc Feed. This includes a comprehensive collection of dashboards, reports, assurance report cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the Monitoring category. The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.6.0
- NNM 5.9.0
- LCE 6.0.0
Note that this dashboard relies on Nessus Network Monitor (NNM) detections being forwarded to the LCE. Make sure that NNM is configured to send syslog messages to LCE: in Configuration > NNM Settings > Syslog, include the LCE host (with port 514) in the Realtime Syslog Server List. LCE listens for syslog messages by default.
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with NNM, as well as log correlation with the LCE. Using Tenable.sc CV, an organization obtains the most comprehensive and integrated view of the network and the cloud services being used.
Included components are:
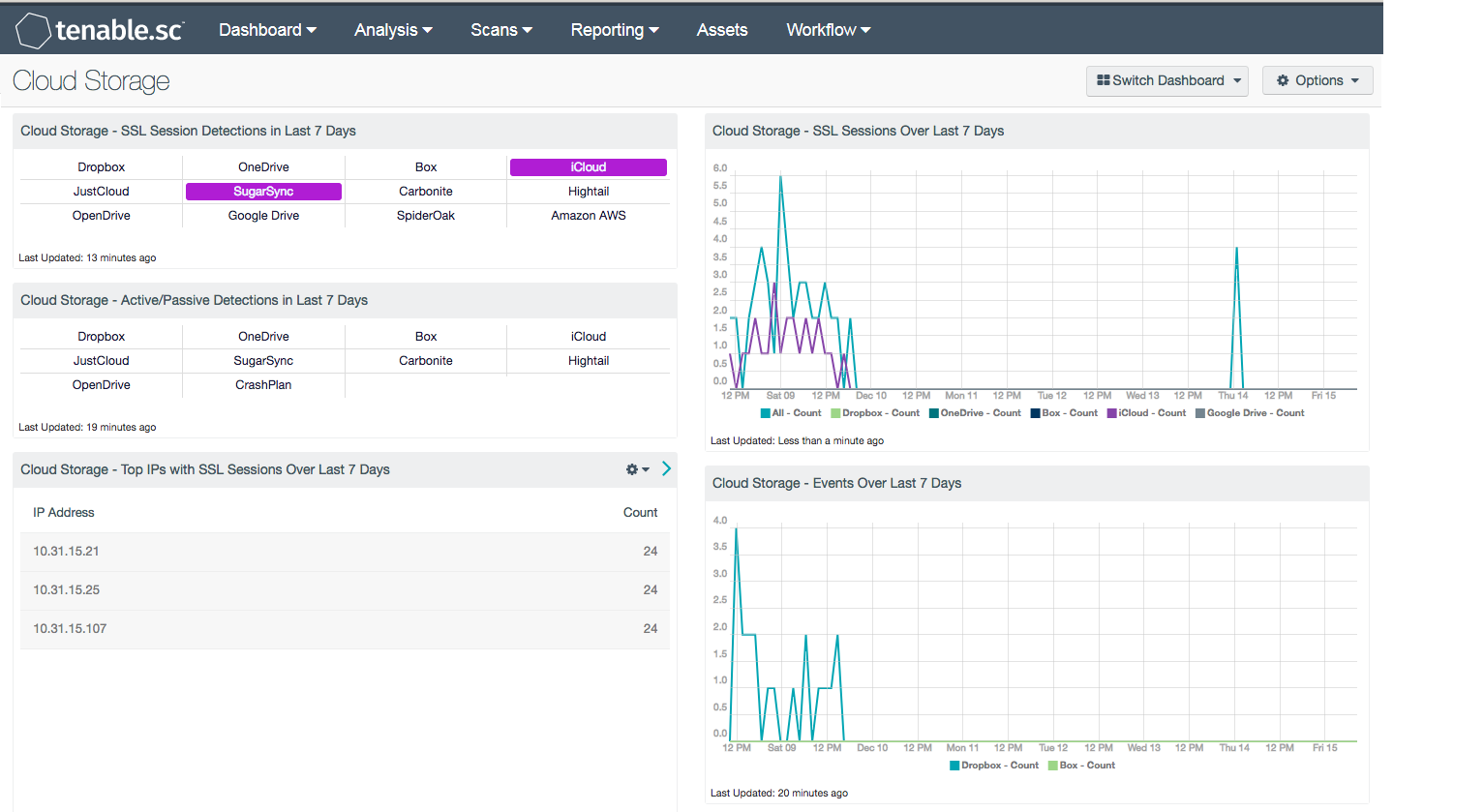
Cloud Storage - SSL Session Detections in Last 7 Days - This matrix presents detections of SSL sessions initiated to various cloud storage services that have occurred in the last 7 days.
Cloud Storage - Active/Passive Detections in Last 7 Days - This matrix presents active and passive detections of interactions with various cloud storage services that have occurred in the last 7 days.
Cloud Storage - Top IPs with SSL Sessions Over Last 7 Days - This table presents the top ten IP addresses that have initiated the most SSL sessions to cloud storage services within the last 7 days.
Cloud Storage - SSL Sessions Over Last 7 Days - This chart presents a 7-day trend graph of SSL sessions initiated to various cloud storage services.
Cloud Storage - Events Over Last 7 Days - This chart presents a 7-day trend graph of events related to various cloud storage services.