by David Schwalenberg
September 3, 2014
In February 2014, the Australian Signals Directorate (ASD, formerly DSD) updated the publication “Strategies to Mitigate Targeted Cyber Intrusions” (available at http://www.asd.gov.au/infosec/top35mitigationstrategies.htm). The publication contains a list of 35 strategies to mitigate targeted cyber intrusions, ranked in order of overall effectiveness. According to ASD, over 85% of the cyber intrusions that ASD responds to could be prevented by following the top four mitigation strategies on the list.
According the ASD “Strategies to Mitigate Targeted Cyber Intrusions” publication, “The Top 4 mitigation strategies, when implemented as a package, provide a large reduction of risk for a relatively small investment of time, effort, and money. ASD recommends implementing these Top 4 mitigation strategies first on workstations of users who are most likely to be targeted by cyber intrusions, and then on all workstations and servers across the organisation.”
Tenable’s Tenable.sc Continuous View (CV) provides an organisation with a proactive method of discovering cyber intrusions, so the organisation will not have to just rely on individual products reporting partial findings. Tenable.sc CV provides the unique ability to correlate vulnerabilities, configuration audits, and event logs in a single location, enabling a proactive approach to continuous network monitoring. This dashboard provides an organisation with detailed information on the implementation of each of the ASD Top 4 mitigation strategies: application whitelisting, patch applications, patch operating system vulnerabilities, and restricting users with administrative privileges.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment.
The dashboard requirements are:
- Tenable.sc 4.8.1
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Tenable.sc CV’s ability to continuously monitor the network to identify vulnerabilities, reduce risk, and ensure compliance differentiates Tenable from the competition and provides organisations with the ability to be proactive while implementing the Strategies to Mitigate Targeted Cyber Intrusions. The ability of Nessus, LCE and NNM to detect vulnerabilities on the network is unmatched in the industry. Nessus actively scans the network for vulnerabilities and compliance issues, while NNM passively monitors network traffic. LCE monitors logs and NNM events to detect vulnerabilities, while also using NetFlow and syslog events to correlate threats and provide alerts to security professionals.
For an additional explanation of this dashboard, along with the other strategies listed in the Strategies to Mitigate Targeted Cyber Intrusions, see the SecurityCenter Continuous View and the Australian Signals Directorate’s Strategies to Mitigate Targeted Cyber Intrusions technical paper.
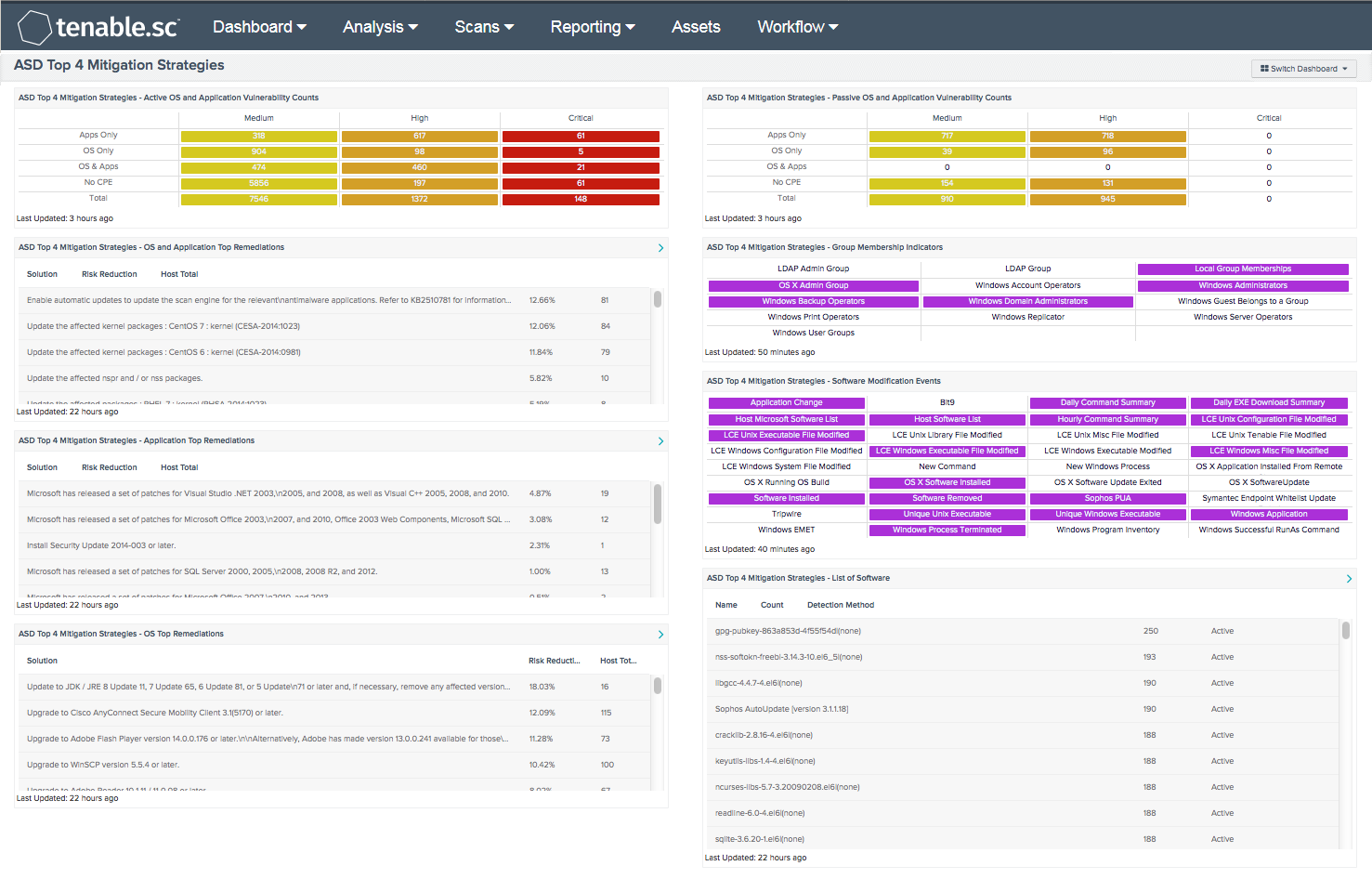
ASD Top 4 Mitigation Strategies - Active OS and Application Vulnerability Counts: This component provides a count of the active vulnerabilities discovered on the network based on if the vulnerabilities are for operating systems, applications, or a combination of both. This data shows analysts a comparison of applications versus operating systems.
ASD Top 4 Mitigation Strategies - OS & Application Top Remediations: This component provides a remediation summary for plugins that are classified as both application and operating system. The list shows remediation actions that may be taken to prioritize solutions that will mitigate several risks. The remediation summary provides the list of solutions to resolve security flaws of a particular application. The data provided includes the solution description, risk reduction percentage, and how many hosts are affected.
ASD Top 4 Mitigation Strategies - Application Top Remediations: This component provides a list of application-centric remediation actions which have the greatest effect in reducing risk. By applying the defined patches, other vulnerabilities will also be mitigated. The CPE regex “cpe:/a” is the prefix for application CPE strings. The remediation summary provides the list of solutions to resolve security flaws of a particular application. The data provided includes the solution description, risk reduction percentage, and how many hosts are affected.
ASD Top 4 Mitigation Strategies - OS Top Remediations: This component provides a list of operating system-centric remediation actions which have the greatest effect in reducing risk. By applying the defined patches, other vulnerabilities will also be mitigated. The CPE regex “cpe:/o” is the prefix for operating system CPE strings. The remediation summary provides the list of solutions to resolve security flaws of a particular application. The data provided includes the solution description, risk reduction percentage, and how many hosts are affected.
ASD Top 4 Mitigation Strategies - Passive OS and Application Vulnerability Counts: This component provides a count of the passive vulnerabilities discovered on the network based on if the vulnerabilities are for operating systems, applications, or a combination of both. This data shows analysts a comparison of applications versus operating systems.
ASD Top 4 Mitigation Strategies - Group Membership Indicators: This Group Membership component is a matrix of saved queries which quickly identifies plugins that match on group membership settings. When a query result is greater than 1, the indicator will turn purple. Plugin ID 45477 defines LDAP Group indicators as a query in remote LDAP for a list of groups. Plugin 71246 connects to a host via SMB and retrieves a list of local Groups and their Members. Plugin 10901 collects the members of the Account Operators group. Members of this group can create or modify local user accounts but cannot modify or create administrative accounts or edit user rights. These are just a few of the indicators in this matrix.
ASD Top 4 Mitigation Strategies - Software Modification Events: This component provides an indicator for file changes or modification events collected from systems with LCE Clients installed, or from systems where syslogs are collected. For each indicator, when a pattern match is found, the indicator will turn purple. Some of the event indicators in the matrix are application changes, a Windows executable file has changed, and UNIX library file changes. The indicators of this component provide system administrators with a central location to monitor for authorized or unauthorized software execution, installation, or changes. Regardless of if the software is downloaded from the internet or a USB drive, LCE Client software can log the application events. When configured appropriately, whitelisting can help prevent unauthorized intruders from modifying or adding software to secure servers or workstations.
ASD Top 4 Mitigation Strategies - List of Software: The foundation of application whitelisting is knowing what applications are installed within an organization. Tenable.sc CV can collect information about installed applications using the List of Software tool, and by collecting logs from several sources such as workstations, servers, and enterprise whitelist applications. This component provides a detailed list of software currently discovered on the network. The best practice with this component is to create several copies of the component, and apply an asset or subnet to each component. Modifying the filters in this manner will provide the organization with the details for installed software for each targeted segment of the network.