by Cody Dumont
April 12, 2016
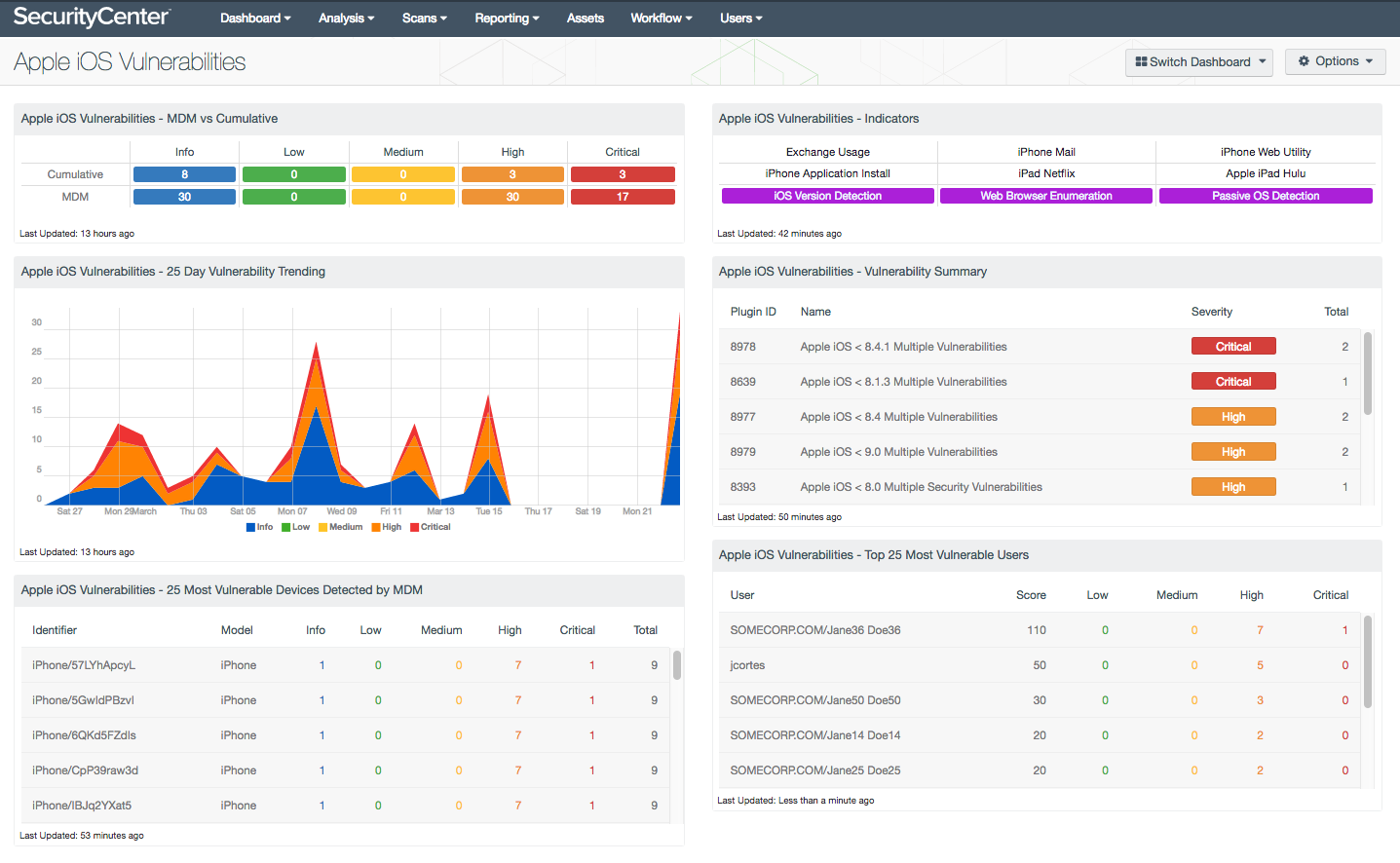
As BYOD (Bring Your Own Device) propagates into corporate environments, the risk profile of an organization expands to include all sorts of mobile devices. SecurityCenter supports collecting data from MDM solutions and by passive detection methods. This dashboard helps the security operations team to identify threats from Apple iOS devices.
For many organizations, including mobile devices in their vulnerability management programs is challenging. Mobile devices can connect and disconnect from the network at any time, and scanning these devices for vulnerabilities and compliance violations can be very difficult. The result of excluding mobile devices as part of the risk profile makes for a less secure environment and less informed risk management team, which can lead to inconsistent security and compliance policies for mobile devices. To help address these issues, SecurityCenter has the ability to scan MDM solutions such as Apple Profile Manager, Microsoft ActiveSync, VMWare AirWatch, MobileIron MDM, and Good Technology MDM.
SecurityCenter Continuous View (CV) includes the additional feature of detecting mobile devices using the Passive Vulnerability Scanner (PVS). PVS can detect a wide variety of devices, such as those running Apple iOS. An advanced feature provided by PVS is OS detection using deep packet analysis. PVS includes a variety of checks which look for Apple iPhones, iPods, and iPads that have not been updated with the latest security checks.
This dashboard combines both collection methods into a single place to easily understand the risk associated with allowing Apple iOS devices to be used on the network. Several of the components compare the MDM-collected data with data collected by PVS and stored in the Cumulative database. The Cumulative database is the location where SecurityCenter stores all vulnerability data that has been recently collected from Nessus, PVS and LCE. The MDM database is a specialized database populated by connecting to a MDM solution. Other components list devices identified as Apple iOS devices and their users. Combined together, this dashboard will provide a more accurate picture of Apple iOS device activities and risk.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 4.8.2
- Nessus 6.5.6
- PVS 5.0.0
- MDM Repository
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. SecurityCenter CV shows risk across all systems, including cloud, virtual, mobile and traditional systems, enabling informed decisions. SecurityCenter CV provides tight integration and API extensibility with SIEMs, malware defenses, patch management tools, BYOD, firewalls, and virtualization systems. PVS is a sensor for SecurityCenter CV, an upgrade to SecurityCenter, and provides deep packet inspection enables discovery and assessment of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, cloud applications, and critical infrastructure.
Components
Apple iOS Vulnerabilities - MDM vs Cumulative: This matrix provides an easy to understand method of monitoring Apple iOS devices collected via MDM and other methods. The Cumulative database is the location where SecurityCenter stores all vulnerability data that has been recently collected from Nessus, PVS and LCE. Monitoring this component for gaps in coverage between MDM and other collection methods will help the organization understand the effectiveness of the BYOD management program.
Apple iOS Vulnerabilities - 25 Day Vulnerability Trending: This component provides at graphical representation of the vulnerabilities discovered over the past 25 days. The component searches the cumulative database for the vulnerabilities related to “Apple iOS”. The chart provides analysts with a count of vulnerabilities discovered with one day for each data point in the graph.
Apple iOS Vulnerabilities - 25 Most Vulnerable Devices Detected by MDM: This component provides a list of the most vulnerable Apple iOS devices. The component uses the MDM database and a filter using the OS CPE string. This combination searches the MDM for all Apple iOS devices and then provides a sort based on Vulnerability Score. The Vulnerability Score is calculated by assigning a value to each severity level, and then adding the collective scores together.
Apple iOS Vulnerabilities - Indicators: This indicator component provides easy access to PVS data for iPhone and iPad detection plugins. The indicators focus on specific PVS related plugins which have iPhone or iPad in the name. Other indicators focus on device detection information, and will turn purple when a match is found.
Apple iOS Vulnerabilities - Vulnerability Summary: This component provides a summary of vulnerabilities detected using PVS. The table searches for vulnerability data in the cumulative database, which generally will only display PVS detected data. The query looks for “Apple iOS” in the plugin name and sorts based on the severity level in descending order. By monitoring the patch level of Apple iOS devices, the organization can detect vulnerable systems, and work with users to reduce overall risk.
Apple iOS Vulnerabilities - Top 25 Most Vulnerable Users: This component provides a list of the most vulnerable Apple iOS users. The component uses the MDM database and a filter using the OS CPE string. This combination searches the MDM for all Apple iOS device users and then provides a sort based on Vulnerability Score. The Vulnerability Score is calculated by assigning a value to each severity level, and then adding the collective scores together.